There are a lot of stupid things you can do with the ports on your computer. The best example is the Etherkiller, an RJ45 plug wired directly to a mains cable. Do not plug that into a router. USB is a little trickier, but with a sufficient number of caps, anyone can build a USB killer that will fry any computer (.ru, Google Translatrix)
The USB Killer v2.0 is [Dark Purple]’s second version of this device. The first version was just a small board with a DC/DC converter, a few caps, and a FET. When plugged in to a computer, the converter would charge the caps up to -110V, dump that voltage into the USB signal wires, and repeat the entire process until the computer died. This second version is slightly more refined, and it now dumps -220V directly onto the USB signal wires. Don’t try this at home.
So, does the device work? Most definitely. A poor Thinkpad X60 was destroyed with the USB killer for purposes of demonstration in the video below. This laptop was originally purchased just for the test, but the monster who created the USB killer grew attached to this neat little laptop. There’s a new motherboard on the way, and this laptop will live again.

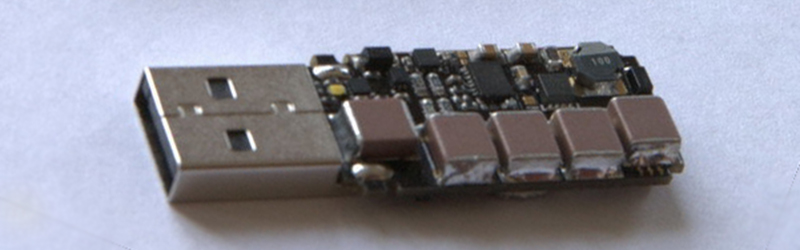















This is one of those things that I really want to exist, but I feel is a terrible thing to put out there. Very cool bit of tech, and a lovely form factor!
Just out of curiosity, anyone know what would happen if you were arrested with one of these and the cops plugged it in? Could their be legal repercussions?
discovery through experimentation
hail hydra
hail hydra
Edit: Also, does anyone see schematics for the device on there? It’s simple enough, but that’s a very lovely fromfactor.
I’m sure some charges would fit in destroying a police computer, but since technically it was destroyed by a police officer *ponder*. Legally do you need to consent to the search ? If consent was sought and granted, then technically you would have destroyed a police computer. It could be a space with no clear laws have been created yet, depending on the country.
I’m kind of reminded of that tale of a basket of USB sticks with a company logo dropped off in the lobby of their corporate headquarters, and then jumping past three layers of physical security as staff (and management) grabbed them (they were free) and plugged them into their computers (Back when Microsoft Windows used to automatically run everything in the Autorun.inf without prompting the user). Who is legally responsible for that attack vector ? And if someone abuses Microsoft COFEE, is Microsoft legally responsible for adding the backdoor to every OS that they ship ?
I would “hope” (yeah, I know, that might be pretty far fetched) that an investigator with the police would be aware of the possibility of malware on a USB stick and would plug it into a “sacrificial lamb” that was not connected to a network. Hopefully that PC would be an old one ready for surplus/salvage and with Linux or Minix loaded on it to ignore common M$ directed malware.
For evidence collection, a write blocker device would have to be used to prove that police did not tamper with it. Maybe the write blocker device has some protection for this… Though I doubt it does.
That’s exactly the reason why this USB Killer is posted on the internet. Since law enforcement now KNOWS it’s out there, they know to watch out for it and put adequate protection circuitry between their computers and the target USB port (in which case, a crowbar circuit with a few zener diodes and a series fuse would do that job just fine).
The write blocker might be destroyed but, from my experience, it’s unlikely that the computer itself would also be damaged unless you were using a forensics tower with built in USB write blockers. Normally the write blockers are separate pieces of hardware (sometimes with their own external power source). You plug a USB into one end and a cable into your machine and the write blocker does some magic inside the box.
A write blocker looks to be almost the price of a cheap laptop (and probably more, once purchased through the public sector burocrazy), so it’s still going to hurt the police.
They ask people if they have knives or needles on them when searched to prevent officers getting injured. Not sure what the consequences are if you lie to that but it seems a good fit. ‘Are you carrying any digital media which may damage equipment used to investigate it?’ Though if they write regulations for that then someone will surely have already designed a protected port for investigating suspicious devices or something.
I’d expect some optical coupling would do the trick, it wouldn’t even be that expensive to pull off. You may not be able to easily get USB 3.x throughput, but you don’t need that for forensic purposes anyway. You could probably even build this all into an in-line cable for use on any USB host.
Simpler even than that, I should imagine. Just some basic glass fuses that cut out at the threshold for voltage on data ports – below where the port’s own internal fusing would try to cut off, of course.
Even just a few current-limiting resistors may be more than adequate, if they’re designed to block high current DC that can destroy the USB port but let AC signals pass, the USB killer would be rendered harmless while still being able to use the flash drive.
Fuses don’t work on voltage, and neither would current-limiting resistors, it’s not a matter of current, it’s the voltage. Of course, voltage drops with low resistance, but electronics are pretty high-resistance, especially signal lines. Well, it worked, anyway.
Zener diodes, as mentioned, might be a solution, use ones at 7V, say, for a bit of slack. Assuming they can close before the voltage does any damage. That’d be the issue. You could design something that has a delay before connecting the data lines, but then an improved zapper could just wait til it sees data.
Since nobody expects a USB-zapper, it’s not the sort of thing anyone would bother protecting against. It’s probably cheaper overall to just replace the motherboard on the million-to-one chance it happens. It’s only a nuisance really, the hard drive data would still be OK, might be the hard drive electronics are fine too. There’s a fair amount of transistors between USB and SATA ports. Not the sort of thing you could really model and test, too unpredictable. But it’s probably not going to erase data. Only ever be an expensive annoyance.
Voltage by itself doesn’t do any damage. It’s the high current *caused* by that voltage breaking down the isolating layers on the chip that causes the damage.
Voltage multiplied by current means power (energy per unit time). If either of them is zero, there can be no energy transfer into the ‘victim’ circuit, hence no damage.
The best protection is therefore to clamp the voltage (by using the zener diodes) and shunt the excess current through a series fuse which breaks the circuit, meaning no current goes into your victim circuit and no damage.
“I don’t know, unless you show me the schematics and source code of the device you’ll be using to investigate it”.
It really depends how poorly made the investigating device might be. What if your USB stick had a new FTDI device driver on it, it could brick the policeman’s USB missile launcher…
Not when ALL hardware and software is required to have a backdoor for government wiretapping do to The CALE Act being expanded (The Patriot Act didn’t help). Like it or not, the backdoors are required by law and the companies are under NDA not to disclose, even if they are discovered by security researchers (like what happened to Apple). It is all laid out in the laws, but no one bothered to actually READ them.
I assume from your comment that you have bothered to read this law, then. Could you tell us which one it is, and quote the bit that requires all tech companies to backdoor their products?
Communications Assistance for Law Enforcement Act of 1994 (CALEA)
In October 1994, Congress took action to protect public safety and national security by enacting CALEA. The law further defines the existing statutory obligation of telecommunications carriers to assist law enforcement in executing electronic surveillance pursuant to court order or other lawful authorization. CALEA is codified at 47 U.S.C. § § 1001-1021 .
The legislative history of CALEA is provided in House Report No. 103-827, Part I .
https://askcalea.fbi.gov/calea/
https://www.fcc.gov/public-safety-and-homeland-security/policy-and-licensing-division/general/communications-assistance
and Cisco’s RFP on Lawful Intercept https://tools.ietf.org/html/rfc3924
http://cyberlaw.stanford.edu/blog/2016/02/calea-limits-all-writs-act-and-protects-security-apples-phones
CALEA Section 1002(b)(1) provides:
(1) Design of features and systems configurations. This subchapter does not authorize any law enforcement agency or office
(a) to require any specific design of equipment, facilities, services, features, or system configurations to be adopted by any provider of a wire or electronic communication service, any manufacturer of telecommunications equipment, or any provider of telecommunications support services;
(b) to prohibit the adoption of any equipment, facility, service, or feature by any provider of a wire or electronic communication service, any manufacturer of telecommunications equipment, or any provider of telecommunications support services.
— so this means that a government mandated backdoor — is illegal — under CALEA.
Also look at: https://www.law.cornell.edu/uscode/text/47/1002
(b) Limitations
(3) Encryption
A telecommunications carrier shall not be responsible for decrypting, or ensuring the government’s ability to decrypt, any communication encrypted by a subscriber or customer, unless the encryption was provided by the carrier and the carrier possesses the information necessary to decrypt the communication.
You are better off encrypting the FLASH drive and have a high chance that the police don’t have the resources to do anything about it. At most they are just fishing for crimes. With this device, now they have hard evidence. They can add a half dozen charges.
It may not be the police you could be a documentary maker travelling through an unfriendly country, and encryption could get you jail time if you do not cough up the passwords. But if their computers die, then they may just wave you through, fearing for their own lives.
It seems to me you really shouldn’t travel with anything more offsenive than Bach’s Brandenburg Concerto’s these days. Additionally, if I really needed to go small, go with a 64Gb SIM chip – small enough to conceal, large enough to copy out the largest of state secrets.
SIM as in mobile phone? Do they make SIMs that store data? Why!? You might get a K or so in the phonebook area of a normal SIM. For hiding data, there’s steganography. Or just sending it across the net, encrypted and stego’d.
Plenty of countries will convict you for obstruction if you do not hand over encryption credentials when asked.
That is under the condition that you actually *know* the credentials. Which is kind of difficult when using “strong” security methods like random passwords which are only generated once for every encryption session (and may quite possibly be disclosed to the user only after verifying his/her safe arrival).
If you have some files you need to take with you, just use a dropbox or mail/courier it. Your charges get a lot worse if you are carrying a device that can destroy the computer it is plugged in. It is not like they have only one computer. If it blows it up, they might take a closer look or detain you far longer than usual. Crossing a border with something like that can get you nailed as a terrorist by both sides. They xray stuff and can see that it look very different than regular usb sticks. More questions lead to more suspicions and next thing you know you are detained. There are no duel process these days.
People that like to destroy perfectly working things for amusement don’t understand that there are poor people out there that can afford one. While it is within an individual’s rights, I think it is morally wrong and immature to promote that on HaD.
And you really think that nobody is going to suspect you if you carry a device that is either blank or only contains data that is completely harmless and non-incriminating?
I’d be very suspicious about people that look and sound too good to be true.
What??? if you carry a device that is either blank or only contains data that is completely harmless and non-incriminating? Yeah. I always carry several blanks. Some have magazines or books and music on them. Frankly, security never blinked twice. People on this thread all think they are legal experts smarter then the next poster.
LOL. TSA can’t find their ass with both hands Do you really think they could decipher electronic circuitry?
Mail/courier??? Oh year right.
LOL. TSA can’t find their ass with both hands Do you really think they could decipher electronic circuitry?
Mail/courier??? Oh year right.
– Sir, whats in the USB-drive?
– Oh…. I don’t think you would want to look in there….
I really want to see this happen
Yeah…the cop says: “Yeah, right!….I don’t believe you. [plugs in drive] [whiz whir bang]…Oh F*k”
— I told you so…
It would depend on what you tell the cop.
If you truthfully say that he should not plug it or it will damage the computer then nothing can be blamed on you.
Obviously not dealt with police much, Jeroen. Reasonableness and logic, not how they work.
If you make something that destroys computers, why would you warn someone? That’s this thing’s only purpose, why would you even carry it if you’re going to warn people? There’s not a lot of reason to carry it anyway, of course… Kind of proof of a useless concept, really.
it does exist. you can buy it at usbkill.com
In da houuuuuse zipzup*
It would have been a lot cheaper to test it with a powered USB hub than with a working computer.
And if you were the sort of person who might expect trouble from the police this would be a very amusing little thing to keep on your person. The important thing, of course, is to tell them exactly what will happen if they plug it into a computer. Then be ready to take bets on how many computers they destroy before they realize you were telling the truth.
you sure right!!!
you surge right! XD
yep fried pork
Take your pounds back to Reddit.
I store my important files on that, but it only seams works on one of my computers, on the others it interferes with the USB mouse and sometimes puts the screen in sleep-mode. You may have to try a few. Do you have any new computers with Windows 10?
:)
Seems to me the real opportunity here is a USB “surge limiter” that you take around with a copy of this post and sell to police and others who want to stick stranger’s USB devices in their computers. Could probably make a few dollars doing that ;-)
Are you a relative of Adrian Lamo per chance? O_o
The capacitors do not have an infinite supply of energy. One computer, at best two, before the caps are completely discharged. Of course, you could always add a circuit that says “discharge for precisely 10ms and stop”. That would likely keep modern caps charged to kill more than two computers.
The caps don’t store energy when the device is unplugged (you aren’t charging it and then plugging it in). It’s using the 5V from the USB socket to charge up, then discharge.
You seem to be genuinely confused about how this device works. The capacitors aren’t charged like a battery for later use. They’re charged by the computer they are about to destroy. You could use this on any powered computer until the caps wear out, which would be an incredibly high number, given the reliability of modern capacitors.
I see you did your homework. You have no clue as to how it works?
I just wait till someone realizes this could be made on bigger scale, with mains 230V input and then releasing 50kV back into the grid. *poof* tens of dead TVs, computers and other electronics. And probably a jail when they catch you.
Not going to be easy with all those surge protectors out there, the good ones able to stop nearly anything short of a direct lightning strike. If you actually want to do some real destruction, have the device dump a very large current through the N-G path for a while. (Some higher end outlet testers do that on purpose to check the ground integrity, but for much too short a time to overheat anything.)
I am speaking from experience. Had a lightning strike within 50 yards of a building full of technology I managed. EVERY surge suppressor and UPS burned. Not just stopped the surge but the varistors exploded, melted and burned each and every one. One APC UPS caught fire and burned a 1.5 inch hole in the motherboard, dented the metal housing from flying parts of the varistors and a few caps and to my complete surprise could still supply regulated power to the load but the charge/input side was destroyed.
Not one protected device died. All of the non protected devices in every building within about 250-500 yards was destroyed. A decent surge suppressor works wonders but they are a limited life part.
i would like to point out that the amount of sheer power in a lightning bolt is orders of magnitude higher than anything we can produce artificially.
Not really. Only a few hundred MW. Most powerplants do that day in and day out.
is 1.21 gigawatts
Gravis is correct. In watts it’s about a terawatt no power plant i’m aware of puts out that much ‘day in day out’ actually no power plant in existence gets anywhere close. AMS is off by a few zeros. total global demand is less than 20TW (~16-18 constant). And releasing that much energy in ~30 microseconds (average) isn’t something we’ve done. That being said once you’ve multiplied the massive amount of energy by the miniscule amount of time it’s like ~8kwh
There’s the Z-Pinch machine somewhere or other, dumps a fair amount of power.
I had the opposite. A lightning strike within 50 yards and even devices that were unplugged and still packed in their shipping boxes were all fried from the EMP that the lightning bolt produced.
Faraday cage much?
At one client, the power cord fused itself to the APC UPS when a lightning struck, but the switches and computer protected by it survived (and the computer even did a graceful shutdown when the batteries drained). We had to cut off that power cord, because the schuko plug did not fit through the hole where the UPS was.
At my high school all of the welders are grounded. Idiots will weld with other people’s ground clamps, so that all of the current goes through the ground wiring in the walls.
That school is going to burn down some day, considering we already had arcing in conduit, green wires are flagged hot, a three phase table saw was wired with two phases and a neutral, and code violations everywhere. (The table saw also spun backwards, which loosened the nut from the shaft that holds on the blade and the blade was rubbing against the side of the table)
Lemme guess… Philadelphia School District?
It sounds like the idiots should be grounded, not just the welding tools.
Those pissy little “surge protectors” that are just one plug won’t do shit, anything then a few 10s of V overvoltage the MOVs will go “poof”…
Proper surge protection needs to be multi-layered, and since it’s quite expensive (it involves modification to house mains), very people have it.
As for the “mains zapper” – it would have to be big, absolutely humungus in order to dump enough power to do any damage whatsoever, all the appliances make quite a load.
p.s. a direct lightning strike can (and most likely will) rip wiring out of the wall (Lorenz forces)
A “Mains Zapper” has been done. Unfortunately, before it’s designers could brief the Department of Energy on it and what needed to be done nationally to protect us from it, Homeland Security stepped in and classified the whole thing. I was told that one of the designers got on a plane to go brief the Energy commission in Congress, and stepped off the plane to find that none of the Energy folks had DHS clearance to hear them out.
It don’t work the way the USB killer does, and since I know what the designer’s PhD (went to school with ’em) was in I can make some guesses how it worked; but it was a tiny device. That, or the dear doctor was pulling my leg after crashing by the campus to have some beers because something else canceled a speech before a Congressional Committee.
Most electricians who”ve worked in substations have a few ideas on killing them Explosively driven flux compression has already been weaponized to take out infrastructure. (standard design, straight out of los alamos 50 years ago, with a waveguide, easy as pi, assuming one has access to a fast enough explosive (the los alamos design is freely available online, rdx alot less so. considering we’ve got ’em mounted to missiles already i’m sure american wal-marts will be stocking them next to the uzis and flamethrowers in the children’s section any day now.
No. No one with clearance is going to tell you anything. Why would he risk his clearance to impress you? Liar.
Nobody with clearance is going to tell you that. They aren’t going to risk their clearance and federal charges to impress you. You’re a liar.
obtaniumtk:
Which Walmart is selling usiz? I want one!
Okay, took my forever to come back and reply. The project these folks created wasn’t classified at the time they started it, it was just something they worked on after work. I heard about it before the one I’ve known forever took off to get to Congress, so before anything they had come up with was classified at any level of security. After they got in the air, and were on the way to D.C., that’s when DHS came in and classified everything. Then said friend drove a few hours back to our old campus, where I’m a townie now, and we had a few beers lamenting the fact that the Energy Subcommittee wasn’t cleared by DHS for what ever they had decided the device was now classified as.
I’m staying deliberately vague about who on the project is my friend, or how I think it worked, because for all I know the DHS has done this to multiple projects. While I know the order of events, and that I learned about it while it was just a “look at this cool thing we made” phase, who knows if the DHS would believe that.
If you had ever read the datasheet of a MOV, you’ll find that they aren’t going to deal with steady state overvoltage. They don’t e even turn on until the voltage is around 100V above nominal and only deal with spikes in the microseconds.
Given that the power distribution has very low impedance, someone pretty much need a large capacitor bank charged to a very high voltage before it’ll make a big spike. The high frequency content might have a better chance affecting a very small segment of the local distribution. So it is highly unlikely to be practical.
So basically a solar farm?
It would be interesting to actually store data on this thing. Have it as a security measure if the password for the files is not introduced or even better have a little code combination on the stick itself. If the code is incorrect it kills your computer.
+1 after reading this I am already working on it
When you’re done I will buy one
I’ll buy one too.
Sign me up, I’d have one too.
I’m interested in that.
And we have just launched another HackaDay project in the spirit of the Mooltipass! B^)
Sounds like a Kickstarter to me!
YES! I don’t have the technical expertise to deliver such a campaign, but someone who can should definitely start one.
I hope you don’t do typos.
Have half the key in a file on the device itself. That way even if they have the password, they have to also have your device.
Also I’m wondering what effect this has on a phone.
would also be nice too have a little speaker play Rick Astley song or songething else just to piss the user off.
You could also use it so that there is a password to get in, and a password to destroy. Any others just deny data.
Very good idea. And to be on the safe side of the law, have it destroy the data, not the PC.
This would take my encrypted Kali Live USB to the next level. Sign me up too!
I’d probably split the system over two drives, and set it so that, unless both are plugged in at the same time (or within 10 sec or something), it fries the system. There’s a couple of ways I can see that you could do it; Either have one stick as a lock/destruct drive, and one with data (If you plug the data drive in without the lock/destruct drive, the data connections don’t make, so you can’t read the data (or you could just burn out the memory, if you want more security), and if the lock/destruct drive is plugged in on it’s own, it just blows the system). You could probably sort out the communication between the two drives via IR or RF, or possibly even just hard-wired cabling, if you have them on a lanyard (that’d be a bit more sus, though). Anyone checking the drives will usually just test them one at a time, so won’t think to try them simultaniously first.
Surely it would be possible to get round the legality of destroying law enforcement tech by having the user agree to a ‘terms of use’ pop-up before the password prompt that warns (hidden among other legal garbage) that misuse of this equipment may result in damage to equipment, and the user takes full responsibility for the consequences of its use. Or something equally banal sounding as that. You can’t get charged if the device itself warns them.
Just put a label on the drive that says “WARNING! DO NOT USE! DAMAGE!”
1. Checks mac address and destroys nonauthorized computers
or
2. two passwords one decrypts, the other triggers, reveal at will
Yeah but you may as well just have it refuse access without a password. What’s the point of breaking a computer? I suppose there might be some point in having it kill it’s own flash chip, for security, if you could rely on it. Sure won’t be long before militaries have USB sticks with little explosive charges in them. Wouldn’t store ’em in my pocket.
When I took appart my old white macbook, every port was electrically isolated in it (the whole section of the PCB next to the plugs was powered through a transformer, and every datastuff was optoisolated), would that pass the insulation barrier?
According to the article, this drives the voltage into the SIGNAL wires. These are (usually, see http://bit.ly/1PmPVaD) not isolated due to needing to be plugged into something of worth, and on a laptop that would be the mobo directly.
The signal wires should have ESD-protection. This device wears out these protections by repeatedly dumping a lot of power into them. After the ESD-protection, the USB signal wires often run directly into a fairly important chip, that is well connected to any other important chip including the CPU. A lot of these chips have internal voltage limits of 1V or less.
CPU’s also react in interesting ways to an piezoelectric gas-stove igniter, with one or two loops of wire (keep the spark-gap in the loop circuit).
I went to check again on the motherboard, and I have to call bullshit on myself, the ethernet and the firewire seem to be completely isolated, but not the USB nor the screen port. There seem to be some serious filtering/protection but certainly not a electrical gap.
How about a 30/15 second delay before dumping the electrons?
Part of me is appalled that people take the time to invent things like this that only have one destructive purpose. Some spoiled little brat who’s pissed at his the kid down the street costs the kids parent a grand or two over a stupid little spat. The other part of of me thinks that it would be funny to watch a cop plug it into his computer looking for evidence and wouldn’t tell them anything. Its a USB plug and not against the law to possess.
It’s not new. I can’t find the site, but there is a site from an old video game store and repair shop owner that talks about rewiring an, at the time, expensive game cart and leave it on his counter. He always knew who stole it when they brought in their SNES console for repairs.
That website was Acts of Gord. He bought a defective Game Shark that blew out PS1 expansion ports and deliberately let it get stolen. http://www.actsofgord.com/Wrath/chapter03.php
Gord claims that, from repairing almost none, he ended up repairing 10 expansion ports because of that stolen Gameshark. So does that mean the people who stole it kept bringing it back to the shop? Or were they sharing it between each other, knowing it broke the port? Fatal flaw in the story there.
Is it supposed to be fiction, or just some nerd’s power fantasies?
Wow this is is in dire need of a password prompt before self destruct. “Incorrect password. You have two more attempts”
Or just a little (phone) speaker and a countdown from 10.
I wonder if it’s possible to incorporate a small lock that makes it difficult to actually remove. That would just add to the fun.
In that case you could just destroy the stick with a hammer.
PC-B-Gone
+1
This version works without even having to plug it in. http://i.huffpost.com/gen/1440349/images/n-SLEDGEHAMMER-large570.jpg
+1
So, you don’t get it then eh.
And you found a friend who also doesn’t get it.
John Henry, is that you?
That got me an evil idea. Make few (dozens) of those with cases, put “If found, call xxx-xx-xx-xx!” stickers on them and drop them at random places. I wonder, how many people would call after they broke their computers…
Or just write “Bob ‘s Porn” on it and leave it in a Cafe.
[some popular female celebrity name] sex tapes would be more effective. :)
“If you find this, please DON’T plug it in and call xx-xxx-xxx”
Better use a prepaid phone for that #
Better give the number of your nemesis
How about using a collapsing magnetic field in a coil to generate a few kV?
I think the issue is the kV won’t have the amps behind it to cause the ESD diodes to heat up, this voltage lets it get away with smaller caps that have more capacitance, and because ‘a few KV’ with no amperage behind it is basically what they are made to suppress. By using a lower voltage you can charge it up and do more discharges in rapid succession.
So would an effective prevention to this destroying the computer to be to put all thumbdrives of unknown origin (with a properly locked down computer/os combo) on a hub? The lines would have to go through the USB hub/switch chip which would likely fry before this could reach the computer I’m guessing.
Also would a few Zeners hooked up correctly help mitigate this as well?
I’d like to see this tested. I’m not sure hubs are built to serve such a function and wonder if it could leak enough over to the output. In theory a hub might even act to intensify the action considering some hubs supply a deeper pool of electricity to draw from.
Yes it would need to be tested, but not just with one make of hub but a variety of them, since there are so many designs.
And talking of hubs, I once had a hub fry my device due to the poor soldering done on it by the underpaid asian workers. Bye bye 100 bucks. So I know it works in reverse at least :/
Common CMOS inputs have voltage clamp diodes to VCC and ground. Add a suitable resister or resettable fuse in line with the input and you gain a fair amount of over voltage protection.
Quite possible, as many silicon fails short circuit in case of (moderate) overload. Moderate = not blowing up immediately.
A few Zeners right across the signal lines with a breakdown voltage of about 10V, along with a fuse in series would protect against this *effortleslly*. Once the voltage becomes high enough to cause a damaging current in the signal lines, the zeners short the signal lines and the fuse pops.
It would render the USB port (temporarily) useless but will not cause any damage.
Have you ever implemented ESD protections for USB signal lines? It’s not that simple – they require low capacitance solutions to avoid interfering with the signal unduly. And few people want to build in self-destructing parts (the fuse) to cater against such an incredibly unlikely situation as someone plugging in a device like this.
I wonder if you could create the same form factor with legitimate flash memory onboard as well, and the surge only activates say if you put the wrong passcode in to decrypt (as well as frying the flash at the same time).
I want a few of these to pack in my luggage when I travel.
Call it picking a fight if you must but I’d love to have that chat with the over-curious law-enforcement agent that thought they might have a peek without requesting my consent. Love to tell the judge that I would have gladly and readily warned them of the devices nature had they consulted with me but since they didnt, I couldn’t…
Or the TSA agent or baggage handler that pilfers.
That’s no legitimate defense if they trip over a land mine in your luggage either. “Sure, your Honour, he would have lived if he would have just *asked* about that land mine nicely…”
IBM thinkpad… noooooooo. They are as ugly as a brick, but are very nice and sturdy.
Combine it with real data storage and a password that must be entered to shut off the kill feature. To make it more mad scientist, add an expanding lock function that firmly secures it to the port.
Enter the wrong password too many times and it repeatedly dumps high voltage into the port. Kill the power to the computer and it’ll dump in whatever charge is in its capacitors, which would likely fry something. Failure to enter the correct password should also dump enough volts into the memory chip to fry it.
Using a hub would get around such attacks, simply unplug the USB cable to the hub. Hub would be toast and data on the kill device also toast, but computer would be saved.
Personally, I think the entire concept of locking (physical connection) to the computer just makes it look like it was intended and malicious. Using a device that will destroy a computer after an arbitrary amount of time is far better. At that point, most people are going to think something happened to the computer and not suspect the USB Device. I’d much rather have plausible deniability than be the first suspect of what would now be a crime.
I would see it more useful as device suicide.
Plug it into any standard usb and it will fry the contained memory.
To access the flash memory, perhaps put a piece of tape over the first half of the power lead that powers the capacitors.
Or an adaptor for hidden nonstandard pins.
So I wonder what’s required, in terms of galvanic isolation at the USB port, to make a host device with adequate defenses against this attack?
Something like an ADUM4160 in there and you’re safe? Maybe.
Yeah, I think the ADUM4160 would work. It’s supposed to isolate up to 5KV. The reason the ESD protection built in to you’re average laptop doesn’t stop this is probably because it’s dumping quite a bit more energy in than an ESD transient and doing it as long as it has power. The ADUM might catch on fire, but I don’t think this would break over the isolation.
What it really needs is a camera & mic to record the reactions as they plug it in…..
And a 3G modem to send reaction video.
Better yet, make an SD card version.
Another fun variant would be the equivalent of the dye packs used in cash transport boxes – spills indelible ink all over the place when plugged in.
Or a UV LED and some UV resin, so it glues itself into the socket..
Or a “Mission Impossible” stick – voice synth says “This stick will self-destruct” followed by smoke and melting.
“Or a UV LED and some UV resin, so it glues itself into the socket”
usb STICK?
I like this idea. No damage to the electronics, and you could offer to replace the USB port to further humiliate and/or infuriate your hapless victim.
I’m reminded of the old microfloppy hack with sandpaper. Anyone else remember that one?
The one with match head? I remember that you’ll set fire to the computer with this hack!
Ah, Jolly Roger! Which probably means it was bullshit and nobody ever actually tried it.
Far as I know, Jolly Roger still hasn’t turned up.
Maybe I’ll not make one of those. Let’s go back to anvil shooting :D
OMG. Why is HAD featuring such crap??? It’s not even creative, just stupid and moronic. Next I will build a USB plug that has a mains connector. Or a USB stick with 20g of high explosives and a detonator connected to USB power. Equally uncreative and moronic.
Here, some more moronic ideas for you: How about a laptop PSU that has no transformer in it, just some weight and a patch wire from mains to laptop connector. Or a boot CD that erases all your data without asking, if you insert it and have CD above HDD as boot order
yes, JustYou.
How about a CPU that has requires MicroCode updates.
Or a Car that has bad code and lies on emission tests.
Or a GPS/4G chip that monitors if your lease/subscription on you heart-pump is paid up.
Hum, do I smell a “Reposession Mambo” reference here? =)
Kudo’s kind sir. Also. Almost Human ep as well
mmm you sound angry, also:
http://www.fiftythree.org/etherkiller/
Would’nt it be easier to look under the casing to see 3-4 monolithic capacitors and NOT run it on a computer. Common Sense. . .
Question is, how obvious would it be to a basic IT worker, when looking at the motherboard?
How about a reverse version of this for the security conscious – disabled by a software command or similar. So if your laptop is seized and searched it will kill every USB/LAN device (etc.) plugged into it by The Man.
I believe killing a pc or any device by sending high voltage directly to it through a port, it is not a difficult task. It can be done with capacitors or even a small taser (does that little portable USB classify as taser? If it is, is it illegal to walk around with it?). In the attached blog post you can see a nice trick for frying a whole network infrastructure, behind the network switch (after the network switch is toasted)!
In this guy’s blog post, due to the high voltage, the spark jumps over burned connections and not physically connected circuits. http://gfragkos.blogspot.co.uk/2015/09/a-weapon-for-mass-destruction-of.html
Just wondering… if you put a USB-hub in between… the hub will be fried… but what else? Will it affect any of the other devices (other peripherals or computer it connects to)?
Jurgen, Plugging in the USB killer into a USB hub will only kill the hub.
And not the computer.
I never ever pick up any lost USB flash drives.
For many reasons. And this is one of them.
I’d like to see a version of this with some actual memory and a set of DIP switches to disarm it ;-)
IDIOT!
how do i create a usb killer 2.0 ? anyone please reply only if you know how thank you
V3.0 (patent pending) dumps 3.3KV directly into the USB which is enough to not only destroy the motherboard but if the spike gets onto the 5V line it will also spread through the machine like a virus and fry the SSD/HDD as well.
I tested a version of this on a machine a while ago and the battery itself heated up and could have gone into thermal runaway but either way it was deader than mutton.
I want to buy one!
i had a talk with the guys of usbkill.com who are selling that kind of device, they market it as a testing tool for hardware designers and pentesters. I saw videos of tests and it is crazy how expensive hardware goes bye bye so easily. it seems that the new macbooks cant be affected by those USB power surge attacks tho.