As buzzwords go, the “Internet of Things” is pretty clever, and at the same time pretty loathsome, and both for the same reason. “IoT” can mean basically anything, so it’s a big-tent, inclusive trend. Every company, from Mattel to Fiat Chrysler, needs an IoT business strategy these days. But at the same time, “IoT” is vacuous — a name that applies to everything fails to clarify anything.
That’s a problem because “IoT Security” is everywhere in the news these days. Above and beyond the buzz, there are some truly good-hearted security professionals who are making valiant attempts to prevent what they see as a repeat of 1990s PC security fiascos. And I applaud them.
But I’m going to claim that a one-size-fits-all “IoT Security” policy is doomed to failure. OK, that’s a straw-man argument; any one-size-fits-all security policy is bound for the scrap heap. More seriously, I think that the term “IoT” is doing more harm than good by lumping entirely different devices and different connection modes together, and creating an implicit suggestion that they can all be treated similarly. “Internet of Things Security” is a thing, but the problem is that it’s everything, and that means that it’s useful for nothing.
What’s wrong with the phrase “Internet of Things” from a security perspective? Only two words: “Internet” and “Things”.
The Things
Which Things constitute the “Internet of Things” is an easy starting point. If you ask Mattel what Things they mean, they’ll tell you Hello Barbie. For Samsung, it’s your fridge. If you ask Ford, they’ll tell you it’s a car. I was at an embedded electronics trade fair a couple years ago, and there was a company that designs factory-floor robotics telling me about their IoT strategy. It gets weirder: yoga mats, toasters, tampons, sniper rifles, and aircraft.

If you can think up a thing that hasn’t yet been Internetted, test yourself by posting in the comments. Or better yet, seek VC funding first and then work on a prototype second. (And then start your security design after it’s in the customers’ hands.)
The point is that it’s very hard to have a decent discussion of security and the IoT without getting specific about the Things. You do not need or want to take the same precautions with a talking childs’ toy that you do with a Jeep or a Tesla. A malware firmware upgrade for one threatens your child’s privacy (no laughing matter), but a malicious upgrade for the latter threatens your life.
If there’s a cost-benefit analysis being done when connecting a Thing to the Internet, it should be made entirely differently depending on the Thing. Some categorization of the Things is necessary. Off the top of my head, I’ve seen “Industrial IoT” used as a term — in comparison to consumer IoT. That’s progress I suppose.
For security purposes, however, I think it’s reasonable to think about the Things by their capabilities and what potential hazards they bring. Devices that “merely” record data can have privacy implications, while devices that act on the physical world can hurt people physically. The autonomy of the device is important too. Something that’s always on, like an Internetted refrigerator, has more potential for abuse than something that’s used infrequently like a quadcopter hooked up to the Internet: plant a Trojan on my fridge and you can snoop on my passwords all day long, while the quad’s batteries are going down after being online just 15 minutes.
This is just a start. A serious, security-relevant taxonomy of Things is not a task for a Hackaday writer. My point is, however, that calling both toy and real cars “Things” says nothing. Pacemaker-Things aren’t comparable to toothbrush-Things.
The Internet
When you say you’ve got a lightbulb “on the Internet”, what do you really mean? Is it firewalled? If so, what ports are open? Which servers does it connect to? Are the communications encrypted? And if so, do you control the passwords, or are they built-in? Are they the same for every Thing? Just saying “we’ll put it on the Internet” is meaningless. The particulars of the connection are extremely important.
This is where the security community has spent most of its efforts so far, and there’s great work being done. The Open Web Application Security Project (OWASP) has an IoT sub-project and their checklist for testing the security of an IoT device is great, if not (possibly) exhaustive.
When you try to secure you PC, or run a server on the Internet, you have a great advantage. You probably know which ports you need to open up in your firewall, which services you need to run, and/or what destinations you’ll be talking to. Even the cheapest home routers do a fairly decent job of protecting the computers behind them, because people’s needs are pretty predictable. I don’t think my father-in-law has ever used any port other than 80. This is not the case with IoT devices.
 [Dan Miessler] gave a talk at DEFCON (YouTube) last summer introducing the OWASP IoT Project and detailing IoT devices’ attack surfaces. If you’re at all interested, it’s worth a watch. Anyone who thinks a Thing on the Internet is a single device talking to a single server is in for a surprise.
[Dan Miessler] gave a talk at DEFCON (YouTube) last summer introducing the OWASP IoT Project and detailing IoT devices’ attack surfaces. If you’re at all interested, it’s worth a watch. Anyone who thinks a Thing on the Internet is a single device talking to a single server is in for a surprise.
The most important point from [Dan]’s talk, for the armchair security types like me at least, is that an IoT device is an ecosystem, and that means that the bad folks have many more surfaces to attack than you might think, or wish for.
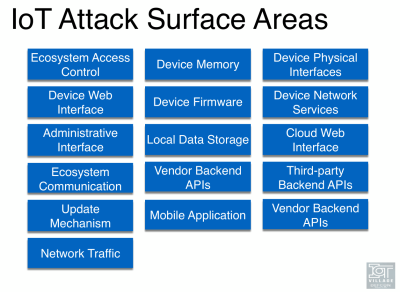 Your device communicates to the server, sure, but that’s just the start. The Thing probably also has a web-based configuration interface. Whatever service it uses (in “the cloud”) has its application interface, and probably also configuration pages. Most devices also use third-party APIs for convenience, meaning your data is going to a few more destinations than you might think, often over non-standard ports. The Thing’s firmware is going to need to be updated, so that’s another very powerful point of attack. Your Thing probably also talks to an app on your cell phone. (There’s more, but you get the picture.)
Your device communicates to the server, sure, but that’s just the start. The Thing probably also has a web-based configuration interface. Whatever service it uses (in “the cloud”) has its application interface, and probably also configuration pages. Most devices also use third-party APIs for convenience, meaning your data is going to a few more destinations than you might think, often over non-standard ports. The Thing’s firmware is going to need to be updated, so that’s another very powerful point of attack. Your Thing probably also talks to an app on your cell phone. (There’s more, but you get the picture.)
If some of these sources are trusted by the Thing, you’d better hope that they are all individually secure and properly authenticated. If any part of the ecosystem is under-secure, that’s what the exploiters are going to exploit. The more Things are interwoven with other Things, or services, or apps, the more avenues there are to break all the Things.
None of this is impossible to secure — there are best practices for each step of the way. Indeed, that’s what good-minded folks like OWASP and “I Am The Cavalry” and others are trying to do. Indeed, one of their greatest contributions is pointing out that the attack surface is much larger than it would be for a bank’s server, for instance. But by defining the problem so generally, they risk turning the task of securing your fitness watch into the task of securing “the Internet”. Of course, it may also be that bad in reality.
The Internet of Things: The Whatchamacallit of Thingamajiggies
(See what I mean? It’s even hard to parody “Things” because it’s already so imprecise.)
“Internet of Things” doesn’t describe much that’s useful from a security standpoint. On one hand, it includes widely varying classes of devices with correspondingly varying needs for security. On the other hand, it fails to describe or delimit the extent of the network that needs securing. Saying “Internet of Things security” adds nothing to just saying “security” except to warn the listener that they might need to be worrying about a very large class of problems, and end-users who don’t think they’re using a computer.
Maybe the term is useful elsewhere (it certainly is useful for marketing or getting money out of investors). But when I hear it in a security context, especially coming from the press or from the government, my eyes roll and my stomach turns just a little bit — maybe I should be stoked that they’re paying attention at all, but I pretty much know that they’re not going to be saying anything concrete. Figuring out what descriptive and useful terms replace “IoT” is left as an exercise to the reader, but it’s one that could have profound and focusing effects on the field.
Death to “the Internet of Things”! Long live “network-connected critical health-monitoring devices” and “cars with WiFi connections”.
















I’ve done some home automation in my house.
I’ve got fans and lights that I can turn on from my cell phone, as well as wall switches that can turn on lights in different rooms, and be re-programmed to control other things if need be.
What I don’t have is a network connected thermostat. No network connected smoke alarms. No network connected door locks.
Hvac system could cost me a lot of money if some one hacked it and set my thermostat to 50 in the summer time, or 120 in the winter… could even potentially cycle the furnace to fast and cause the heat exchanger to crack and poison me and my family with CO… Though the CO detector should pick that up, but were it on a network it too could be over riden.
Door locks should they be hacked into can be overridden and my house could be robbed.
Worst case scenario for light switches is that some one turns the lights on in my house, or cycles them on and off, the bulbs are all LED’s so if they manage to leave them on all the time it will cost me a few dollars on the electric bill… not a big deal.
Perhaps some day I’ll trust the security of internet connected door locks, and have a door that opens when I (and only those who I want to have access) approach the door… but right now I suspect the attack vectors for such a device are too many, and too poorly understood… not that physical locks are impervious, but the police and insurance companies understand what a lock that has been tampered with looks like… mostly…
Flash a bright LED fast enough and it’ll do more than just raise the electrical bill for some people…
More interesting is the idea of terrorism by mass controlling something like this – if everyone putting their kettle on during the break of [Superbowl|World Cup|insert sport of choice) is enough to cause headaches to the power companies, imagine thousands of kettle started simultaneously turning on and off, in sync, across a large part of the country…
Hvac system could cost me a lot of money if some one hacked it and set my thermostat to 50 in the summer time, or 120 in the winter… could even potentially cycle the furnace to fast and cause the heat exchanger to crack and poison me and my family with CO… Though the CO detector should pick that up, but were it on a network it too could be over riden.
This is truly irrational paranoia. A cracked heat exchanger doesn’t kill people without several other simultaneous problems in your house; all of which are more probable and dangerous than some rando on the internet short cycling your furnace, which would be obvious as would any of the manipulations you fear.. You have no furnace high temperature limit? You run strong negative pressure via active exhaust systems that will overpower your blower/inducer? You already have a fubar’ed gas burner? You’re already living in a death trap… maybe you should fear a rando internet guy.
I basically agree with you — the lights are mostly harmless.
But the worst case scenario is actually that ultra-clever cyber robbers know when you’re on vacation b/c you’re not using the lights. They break in and steal your stuff. Or something like that.
Or maybe that someone hacks the small computer that’s inside your lightbulb, giving them a beachhead inside your WiFi network, which they then convert into a keylogger on your computer, and they shut you out, install ransomware, or clean out your bank account.
(Yeah, that takes a lot more work on their part, and I don’t think it’s likely — yet.)
But, assuming you don’t turn your lights on and off from work, you gain _nothing_ from the exposure to the Internet.
Deciding on the risk/return is up to you.
When there are hundreds of millions of households on the web via IoT gear those 0.001% fringe cases, where all the factors are in place for a complete exploit, will still earn organised crime (not to mention pathological political regimes) hundreds of millions of dollars, and they already know it.
I see IoT as an attempt to cover a number of old ideas that never caught on with a new coat of paint. Home automation in one form or another has been around forever, and it has not caught on because it has always been a solution to a set of problems that nobody has. Other areas that need this sort of service have legacy telemetry and control systems in place and it is difficult to see how these would improve by being shifted to the net if they are not already there.
I agree the “need” isn’t obvious to us yet. I think the main reason Home Automation never took off is because it lacked the Automation part, it was mostly about home control. Even early relay based systems offered the benefits of centralized wiring and low voltage switch legs. As more people start living with HA and think of new use cases and automation routines, HA’s role as a “solution to a set of problems” increases. Also as energy costs rise and technology improves the automation experience, we’ll see usage grow. Sometimes the solution comes first I suppose.
To some extent you are right but while systems like HVAC and many appliances have far more intelligence built into them now it is moot to what degree they would benefit from central control or being networked. In some not-too-distant I may have a robot to do my housekeeping – until then I’m not quite sure why I would want to control my washing machine with my cellphone.
I don’t see the benefit of HA cloud interaction beyond sending me notifications and my sprinklers checking the forecast. I agree that we are missing the robot housekeeper, until then it would take something like the a less-expensive Laundroid to make laundry automation worth having. But it might be nice to have the Washer be able to turn on the hot water pump to bring hot water up to the tap before running, or if the Dish Washer knew when the washer finished and could use the hot water already at the tap to run its load, But first they can make a dryer that accurately senses when clothes are actually dry, that’s more important that getting a text.
Of course all sorts of bells and whistles can be added to anything, and there may be circumstances where fine-grained control may be cost effective in the home, but in general I would say IoT is not enough, too soon. Like the current state of HA, it doesn’t confer enough of a benefit to offset the expense, security or lack of it notwithstanding. At the commercial/industrial level this sort of integration has been around for decades, and there may be some trickle-down, but I see little chance for a bottom up market developing any time soon.
I think those are perfect examples of what we don’t need. Adding lots of additional hardware, moving parts, poorly written software (since the IoT is a hot fad and it’s more important to get your product out now than have any long term vision) just to save what, 10 seconds of wasted lukewarm water? We already have a simple, robust mechanical system that works.
IoT is as much as anything else a service for the supplier, rather than the customer. Remote metering and management, invisible diagnostics and updates, contract enforcement, and all that juicy customer data.
Unfortunately you are probably right making the whole concept even less appealing.
I agree, most of “the cloud” is techno-crack that will get people hooked, but destroy their privacy and their autonomy.
The issues is what does the risk/benefit equation look like?
I honestly don’t think a legislated mandated “software extended lifetime guarantee” requiring that all internet connected thingamajigs receive updates for bugs discovered something like 2-3 years after end of product life, establish the legal requirements for documenting the report of a bug in these cases, hey maybe even roll in some Consumer’s Bill of Rights and mandate open source code at product end of life.
And to comment on your gun vs toothbrush thing
The gun is the one where anything down range is reasonably expected to be in the danger zone while it’s loaded and you are only going to get false negative errors.
The toothbrush is the one that’ll have a rechargeable cell unexpectedly explode next to my face if the firmware is flashed maliciously,
It is a natural progression from “Smart Grid” which was a previous version of iot that didn’t mean anything either.
Hard to understand what the heck you are talking about… smart grid ideas have already and are currently driving billions of dollars of development in distribution systems all over the world…..
IoT Security is an oxymoron.
No, it is not.
What is your solution, add another layer of security underneath ? 9F 55 95 F1 02 57 C8 A4 69 CB F4 2B C9 3F EE 31
I agree. To say that IoT security is an oxymoron (a contradiction in terms) is to say that no internet connected device can be properly secured, which is ridiculous. The trouble that IoT manufacturers face is being able to significantly predict avenues of attack prior to shipping, and to be able to update after shipping to fix security weak points. We’ve been solving this problem for years with computers, and phones – The problem isn’t the concept, it’s the actors.
Like software upgrades for the first generation of WEP devices ? IoT may as well be called Internet of Trash. Oh a major security issue, don’t worry about that, it will be fixed in the next generation of hardware. The future proofing is low – minimum RAM, FLASH and processing power for any kind of a major update, security or not.
Really? So you think there are powered up internet-connected computers that are absolutely secure…? Anywhere at all…? Awww, that’s so cute…
There are, they use what is called a “data diode” and they have been around for over a decade. Not common in the civilian world, and I’ve never heard of one being compromised. Other than that, if you are specifically talking about commodity devices, yeah you have a point.
I remember when “high-tech” became the latest buzz-word. It was applied to everything from computers to shampoo. Over-use made it meaningless, like IoT.
Let’s talk about home automation security. Essentially, any cloud based system can never be really secure becuase the owner of the objects (you) is not really in control of your objects (door locks, washing machines etc.). The answer is to have what I call a “massively distributed IOT architecture”. What that means is that the owner of objects control the use of their objects directly with the cloud being used only to provide services such as weather data. You can supply data to the cloud, but that is optional and under your control. Then the objects are both inherently protected using high quality cybesecurity, such that only the owner or someone aurotorized by the owner can access the objects and by having a layered, segmented system within the house. At the core of all this is a mechanism where the objects know who own them. They have public keys for the owner stored within, preferably, a secure element and the communications must be signed by the owner to work. Then the object should not be connected directly to the internet using say, a wifi system that it shares with other computers in the house. First, there must be one or more “coordinating hubs” a.k.a. home controllers, that also have a security layer and the network that connects the objects to the controller must be secure. I use dedicated SSL protected wifi networks where the objects are registered with the network when installed (out of band registration) and no dynamic registration allowed.. Then I use a dedicated IOT router that closes off just about all the ports and, becuase it is dedicated to IOT can easily be very tightly controilled. Add to that a communication protocol mentioned earlier that requires all communications to be signed by the owner and you have pretty good security. It is certainly enough to make it not cost effective to have to break into each house independently. Because the solution is not cloud based, an attacker would have to break into each house separately and hacking the computers in your house would not compromise the separate IOT network. I am building a prototye system using ESP8266 modules talking to C.H.I.P. computer objects, talking to a RPi3 hub connected using an OpenWRT router. I use independent SSL protected wifi for each layer except the hub is hard wired to the router.
Putting strong security in IoT devices is like enclosing every single penny you own in its own safe with its own combination lock number. Maybe it’s safe but definitely not practical. As in real life, you rather group things together and build strong security around them, so every device should talk to the local intranet server which blocks access from/to the external world unless it comes from whitelisted clients on a encrypted VPN.
Not really that hard to secure each device. Assuming that applicable security standards and protocols are set for the different types of use, the security protocols would become a nearly invisible part of the stack, like TCP.
That is assuming that those (overly complicated) protocols are entirely secure and their specific implementations are without flaws, which is really expecting a bit much given what the historical record shows.
It _is_ that hard, though. Devices like the ESP8266 don’t (or didn’t until just recently?) have TLS encryption working. And on other devices, there’s a CPU vs power budget tradeoff that makes the most obvious security methods tricky.
If the device is a computer or a car with a computer in it, you’re right on — it’s just a matter of software. But for a toothbrush, it’s prohibitive. Things aren’t things, and there’s a security impact because of it.
(At least, I think that’s what the author was getting at…)
“… that makes the most obvious security methods tricky.”
Except the one right under you nose. :-)
What form of security cannot be cracked and uses very simple low level logic operations at the cost of needing a $5 flash memory module in read only mode?
I’ll give you another hint, it is only hard to encrypt data with complex key based systems, in real time, but such keys can be used for a batch pipe to send simpler but more secure keys that can be easily utilised in real time.
FFS why don’t you people know all this stuff, I thought you guys were the “experts” compared with me?
Is the risk worth the benefit. Why do people embrace this stuff for a terribly marginal benefit ( excluding the toy factor ) and open themselves up to significant vulnerabilities. Is it just the adolescent new gadget euphoria that should be left behind in the teenage years.
I call it the IoCSTWBi3YBBiDTiWUIoYNBtHiC
Internet of cheap shit that will break in two years but before it does that it will upload images of your naked butt to hackers in China.
If a device is only going to transfer a few gigabytes of data in it’s life it is not very hard to lock down that data-stream to one master server and make it impossible to decrypt or forge, but that would cost an extra $5 per device and the manufacturers are so stingy that they see that as an expense to be eliminated, rather than a core feature.
You bring up a good point about the life expectency of IOT objects. They will have to have an expected life of at least 10 years to prevent the need for a constant stream of repairs. I am looking into what that takes and it seems to be mainly about staying well within ratings and keeping electroyltic capacitors as cold as possible (or not using them). Most other components can have very low failure rates over 10 years. On providing protection at the object level, this is not as prohibitively expensive as you might think. Low level objects (I call them IOT components) such as relay switches or temperature sensors only need secure communications. That can be achiever using SSL and wifi. The next layer up (I call them “first-class” objects) can be cheaply protected with encryption and signing. This layer would include objects like a hot tub controller or a HVAC controller or a fridge controller etc. Such objects can afford to have controllers in the $20 to $50 range. The Samsung Artik modules for instance contain secure elements although I have yet to find out from Samsung how to use them as they seem intent on only supporting cloud based solutions.
I think a 10 year lifespan is a good start but the problem isn’t making reliable hardware, it’s about changing standards and interoperability of new products. Every manufacturer wants their own IoT communication standard, and they also want their new products to have the latest flashy features (meaning they often have to leave their old products behind).
Futuristic Home Owner’s Diary (from about 20 years ago)
http://www.allowe.com/laughs/book/Smart%20House%20Diary.htm
Despite some outdated references of which there are some current alternatives (like torrents instead of usenet), it doesn’t seem too far from today’s futuristic home predictions. Also, take note of the films Electric Dreams (1984) and Demon Seed (1977)
The issue with even the simplest IoT-devices is that even if they by themselves cannot do much more than undermine your privacy, if they are compromised they may provide a backdoor-access to your internal network, behind any firewalls and such. That is why they are so damn important to be secure, even if it’s just an IoT-toothbrush.
This is due to an architectural flaw. There’s no reason for each thing to be able to talk directly to the internet, it would make much more sense for a toothbrush pr lightbulb to use a simple, slow, reliable protocol with a fairly low attack surface to talk a gateway device and then *that* talks to the internet. Of course, that would imply that manufacturers would have to work together so you can use one gateway device, and lol like that’ll ever happen.
To put [Elliot Williams] straw man aside for a moment I would have to say that it almost certainly looks like the future security of IoT is doomed to failure.
To put this in perspective lets look at some history.
There was no substantial intellectual investment into security in the design phase and early development stages of the internet / www.
Security became an afterthought when the opportunity to do things properly had long since passed. As a result the model for implementing security was *black listing* things that hackers shouldn’t do as it was too late to white list actions that were necessary.
This model is completely failed (as demonstrated by history) because it relies on hackers to demonstrate their hacks so that these actions can be blacklisted. ie The system is permanently in a failure mode waiting for the next successful hack. This can’t be understated. In web design to make things (sort of) secure you create an API which essentially is a white list specification for an application and then run it on a server that uses a *blacklist* lol and that is why it is *sort of* secure – ie application is secure but it’s running on a non-secure server.
Now look at these early stages of IoT. There is no intellectual investment being made into security, everyone is just going along with the existing failed internet model.
To make IoT secure we should be creating online hubs (servers) that are not-at-all like your traditional Linux box but we are *not* developing new software or putting hubs online. So all that is left is a non-online servers (in the home) which is actually viable because of the present low traffic demand of IoT but as traffic increases temptation will turn to online severs for their traffic capability and all that is available online are the traditional failed non-secure boxes.
What we need is for someone to write firmware for an IoT router (hub) that only supports end to end encryption along with encrypted data storage that not even the router can decipher. Something simple and from the bare metal that doesn’t have all the security holes that every other operating system has.
yeah, but it looks like we will end up with internet security version 1.0
“What we need is for someone to write firmware for an IoT router (hub) that only supports end to end encryption along with encrypted data storage that not even the router can decipher. Something simple and from the bare metal that doesn’t have all the security holes that every other operating system has.”
But that already exists, the mystery is why it isn’t used.
It is not hard to encrypt a data packet for the end server, then encapsulate it in another layer of encryption to ensure the link to the local router is secure and that the router will only forward valid packets from entrusted IoT devices.
B/c the market hasn’t adjusted yet. Hasn’t been enough hacking to justify the expense. Getting there though w/ more malware and attacks everyday.
Then do you want remote upgrades (I classify that more as a target than a security feature), how much rounds of encryption, what ciphers, what modes, authentication, how much space for keys and authentication, where/how to store keys, what protocols supported, etc. Securing essentially a SoC becomes a bit of a project.
IoT is an empty buzzword.
Internet of Buzzwords?
A few months ago Home Depot discontinued their then-line of Internet controlled power outlets, and discounted them to effectively $4 each. They’re powered by ESP8266 and can be reprogrammed so I snagged eight of them.
The stock firmware depends on a server in China. This is really the only way to control such things from the cloud without having a fixed IP address for your home network. The outlets transmitted a whole bunch of information, including all your schedules and any time the outlet manually or automatically switched, to this server. Oh also your Wifi router SSID and password in unencrypted clear text. Why would they need that at the mothership?
And if that server is ever turned off, they will all stop working, which is probably the biggest risk. These things were $43 a pair before the steep discontinuation discount. There’s no subscription, so once they stop selling there is no incentive to keep paying the electric and bandwidth bills for that server.
What’s more, there is no indication of any of this on the packaging or instructions. Yeah we’re probably clever enough to realize that if you can phone it from the public internet it’s probably got a mediator somewhere to hear the call, but most people aren’t going to think of that. It Just Works, until it Just Doesn’t.
Then again “IoT is an empty buzzword” is an empty buzz phrase. When used in context IoT is not a buzz term. When used out of context it’s meaningless, and still not a buzz term.
The amount of complications things bring into our lives trying to simplify them for us is amazing.
Customers always ask me if I can do this or that… (I’m an electrician). I always tell them, the question is not what I can make work for them, because the technology exists to make work pretty much anything a customer can dream up now. My go to line is that we can make your cell phone make coffee for you in the morning, and that usually clues them in a bit.
The hard question is what does the final result look like when you boil down what you need and what you want together taking into considerations all the factors that go into that, ie- present needs, future outlook, finances, desire to tinker, etc.. Usually when we start looking at it from that perspective a light switch with maybe a 10 year life span on it that costs 2000-3000% more than one that will probably last 50 years just doesn’t always sound that appealing…
But sometimes it does, I like the light switch that I have in my house that I can turn on from my phone and have programmed to come on at sunset so that I never come home to a dark house, it’s a nice thing to have, but for sure a first world issue to try to grapple through…
Meta comment: I said “IoT” and all the comments are about home automation. Is this a Hackaday thing?
The “Internet of Things” is a marketing lure used to attract today’s technologically uneducated mainstream media – and you just swallowed it – hook, line, and sinker.
Haha. I sure didn’t.
They can keep their wifi leds and the glitchey Nest crap. I will wait till security is actually considered in the design. Everything doesn’t need internet access people!
Ive got things running via 433Mhz to a raspberry pi… Simple. Im happy running them via ssh, nice and secure. Locally though its open to exploit to someone with a SDR and a transmitter. Anyone know of some cheap power switches that are more secure?
The biggest worry for IoT IMHO is automotive.
At what point does a manufacturer stop providing software updates to their platform ?
We already see with “smart” TV’s that even the big players cease software support 1-2years after stop sell.
“smartphone” manufactures do the same, a Samsung S3 is well out of firmware updates now yet 100’s of thousands of people still use them.
No one is forcing these companies to own the problem. It’s not being treated as a safety issue, they don’t feel responsible for it.
Does it need a 10year old car with internet connectivity to be hacked and crashed into a school (think of the children) before someone takes action on it?
That’s exactly what I meant about ambiguity with respect to the “Things”. If your fitbit is dead or hacked in a year or two, you won’t really care, right? If your car dies/wigs out, it’s something else. The idea that both of these can be discussed using the same vocabulary is insane.
Oh hell no. You bought and drank and shared theIoT kool aid, HaD. Folks get what they deserve. I will enjoy watching its demise.
It’s Internet of Junk if you ask me… I see no reason to link up everyday items to the Internet. I really don’t see what the masses see in this.