There is a chain of trust in every modern computing device that starts with the code you write yourself, and extends backwards through whatever frameworks you’re using, whatever OS you’re using, whatever drivers you’re using, and ultimately whatever BIOS, UEFI, Secure Boot, or firmware you’re running. With an Intel processor, this chain of trust extends to the Intel Management Engine, a system running independent of the CPU that has access to the network, USB ports, and everything else in the computer.
Needless to say, this chain of trust is untenable. Any attempt to audit every line of code running in a computer will only be met with frustration. There is no modern Intel-based computer that is completely open source, and no computer that can be verified as secure. AMD is just as bad, and recent attempts to create an open computing platform have met with frustration. [Bunnie]’s Novena laptop gets close, but like any engineering task, designing the Novena was an exercise in compromise. You can get around modern BIOSes, coreboot still uses binary blobs, and Libreboot will not be discussed on Hackaday for the time being. There is no modern, completely open, completely secure computing platform. They’re all untrustworthy.
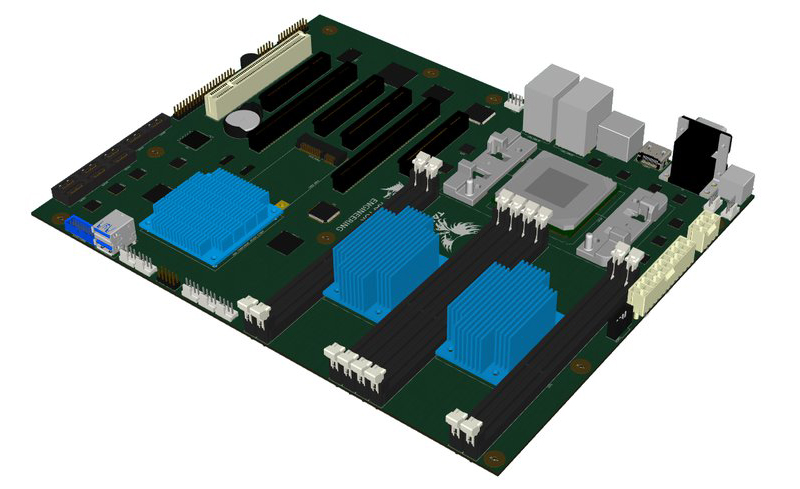
The Talos Secure Workstation, from Raptor Engineering, an an upcoming Crowd Supply campaign is the answer to the untrustworthiness of modern computing. The Talos is an effort to create the world’s first libre workstation. It’s an ATX-compatible motherboard that is fully auditable, from schematics to firmware, without any binary blobs.
RISC architecture is going to change everything.
‘Secure’ isn’t a word you would use in conjunction with a modern Intel processor, and AMD is just as bad. Most ARM processors are out, because there are binary blobs floating around even when the processor isn’t tied up in NDAs. Even graphics are hard to make secure, and while open source GPUs exist, they’re not exactly powerhouses.
To make a computer fully secure, you’ll have to go outside the usual architectures, and the market for a secure computer simply isn’t there to warrant a completely new architecture, anyway. For the Talos, Raptor Engineering chose IBM’s POWER8 processor. This architecture is now most common in computing that has a few more zeros on the price tag than what Microcenter offers, but historically the POWER line can be traced back through the CELL processor, the GameCube, and [Zero Cool]’s sweet clear laptop.
The rest of the hardware includes 8 DDR3 slots supporting 256GB of RAM, 2 x16 PCIe slots, 4 x8 PCIe slots, one legacy PCI slot, an internal mPCIe slot, 8 internal SATA 6Gb ports, 2 external eSATA 6Gb ports, 1 HDMI port, 8 USB 3.0 ports, 2 external and 2 internal RS232 ports, and an internal GPIO header. The full list of specifications and supported operating systems is available on the Raptor Engineering website.
It should be noted this is not the only POWER8 motherboard available. Tyan produces a POWER8 server motherboard, although it is not as open as the Talos. Even with the Talos, there are some restrictions on how open and secure it actually is; thanks to NDAs, some of the PCIe subsystem is not auditable.
Although the Crowd Supply campaign is not live yet, we know the cost of an entry-level Talos system with an 8-core 130W TDP POWER8 CPU will come in at about $5,300. A standalone board less CPU will be available for about $4,000, according to Raptor Engineering. That’s pricey, but not terrible when it comes to high performance enterprise workstations. You’re paying for security and auditability here, and we hope Talos is a success, if only to prove there is a market for truly secure computing.















How is that more secure ? You’re making the assumption this company is more good-willed than another one.
AMD and Intel we KNOW aren’t secure, POWER we’ve no reason to suspect that. Of course we don’t actually know they ARE, but we don’t know they AREN’T. And that’s about as close as you’ll get, I think. What does the NSA buy for their servers? Don’t tell me, it’s a secret.
Auditability of all schematics and code are stated here as what would give Talos “better security”. Oh wait, but not really because the PCIe subsystem is *still* not auditable.
In any case, one could say all of this is BS because someone, somewhere, will eventually have to *produce* the hardware, and that actor is very unlikely to be the end user who actually uses the hardware. The manufacturer themselves are still to be trusted no matter how open the code and schematics are.
Purchasers will be provided with 150hours of uninterrupted footage from various angles of the manufactoring processes.
That doesn’t really prove anything… oh those northbridges? yea they were swapped out, now they have a counterfeit part that supports some obscure ethernet packet backdoor. But here they are being installed, so they must be legit.
That’s why they also include footage of all the ICs being designed and manufactured as well as driven to the assembly plant. Also video footage of rectal probing for all employees to ensure they aren’t hiding any counterfeit chips.
Well, see that’s the thing. Having the schematics and code, someone out in the community can check up on them. People can trace pathways, decap chips, and dump roms. It’s a pain in the butt, sure, but you don’t have to have *every* user do it, just enough of them to catch issues. That’s the kind of mechanism that drives open-source’s reliability. (as for the PCIe subsystem, someone’s figure out a hack to disable it if you really want, probably with a pair of pliers)
“A standalone board less CPU will be available for about $4,000 […]”
I think this can easily be misread as “A standalone boardless CPU” (a CPU without a board), which is backward, as far as I know the pricing.
That’s what I thought it meant. “Let’s eat grandpa”. Commas are important! “A standalone board, less CPU, etc etc”. Or could have used “without a CPU”.
Or just use without instead of less.
Well it certainly makes a leaning tower of pi zeroes look more attractive.
Care to elaborate?
Meaning that if you have to go to this expense to get a reasonably secure, high powered box, ii might instead be worth the hassle of using a distributed OS on a cluster of low powered cheap hardware, that you still might have doubts about, but the layer of virtualisation helps insulate you from.
Obscurity and redundancy do not equal security if it did then we would call the cloud “secure”. Adding complexity generically reduces security because it creates more opportunities for hackers to try different things.
So you should nail a skin across your doorframe, because people are going to pick your locks anyway? >:-)
Apparent simplicity might be hiding complexity you don’t know about. Which is what this is all about, it’s simple to run windows on intel’s latest. Two monoliths, easy to conceive as being simple, but hiding fractal degrees of complexity the closer and closer you look.
I’m saying, units you can grok, assemble into system you can grok, inspect each brick, build a wall as best you can, because looking at big brothers wall catalog, you can’t tell from the outsides whether they are a good wall within.
Too many brick to inspect means security holes.
I am an ex web developer (server side). I can write a secure application and then put it on a Linux box web server so hackers can just hack the OS and get in anyway. Too many bricks.
The solution is to put the web interface on a web server and have that web server access the application server via the API and lock out all IP traffic to the application server except for IP traffic from the web server. One brick.
WTH ??!?!?!? “Libreboot will not be discussed on Hackaday for the time being” sounds very much like censorship.
All I can think of is there is a social rights spat going on between them and GNU which gets emotive, so they don’t want the spillover, i.e. go yell about it on reddit.
Their site, their rules. With that said I think the story behind the decision merits a closer look – and if it’s true I’m appalled.
Oh FFS, I can see why. It’s about transgender persons. Not touching that with a 500ft stick.
lol posted this downthread… https://libreboot.org/gnu/
Haha, that page has an AGPL licence notice at the bottom, after all that anti-GNU ranting.
If it were real, this would be an easy case, discrimination law, especially in Massachusetts, is actually well-written, and regardless of whether she were harassed, she’d absolutely have a case of retaliation.
More likely is that she felt entitled to everything and superior and it kept pissing off everyone else there. I’ve known quite a few people in exactly her situation, transitioning, generally really good, nice people. But they all had this pervasive superiority complex, and any slight must of course be because they’re trans, and not because of forgetfulness or it’s a stupid request in the first place. Like insisting that if I’m speaking to her, I need to sit down to be “less threatening,” even if I’m just popping my head in to ask if she’d like anything from Starbucks. The only reason you get away with that shit is because you’re trans, nobody else can make idiotic demands like that and actually expect anything.
The short explanation: some people are idiots. Some people for some case are idiots. If anybody would require me to sit to talk to them I would tell them to grow up and stop being a moron, if they don’t they can fuck off. That’s the correct way to handle any kind of idiots whether they are anti-SJW idiots (e.g. that assumes that because one woman some time falsely accused someone for rape rapes doesn’t happen*), “SJW” idiots (e.g. that assumes doing anything is sexist – including not being sexist), racist idiots (one black guy once broke into his car ergo all black guy break into cars) etc.
(* yes I’ve seen this one in a non-trolling, non-ironic context)
Autism – never even once.
You know autistics are over-represented among people who claim to be the other gender. And the entirety of people who claim to be the 58 fictional genders. It’s part of their basic lack of understanding of social stuff, they get the wrong end of the stick about men and women, and think that some thing or other makes them “really” a woman (or less often, a man).
https://www.youtube.com/watch?v=LuZFThlOiJI has some good stuff about this toward the end.
I have more respect for people who just want to be, say, a woman, and get on with it, and then try their best to live as women. But some people just want to be transgender, as if it’s an end, not a means.
There’s always been attention-seeking fuckwits. And it’s a shame because they generally make the cause they’re appropriating look like a bunch of idiots. Any old bigot can point to half a dozen loonies, and they’re the easiest ones to find, the loudest, and claim that they represent the group as a whole. Same thing applies to Muslims, actually.
But these idiots don’t actually care about the cause or group they’re supposed to be defending. Because it’s all just part of some malfunctioning psychology.
Still the way certain persons like to rig the argument so that dissent is impossible, and disagreeing with someone is denying them their right to *exist* (?!?!?), as well as bullying, terrorism, and arson in a naval dockyard, makes them impossible to get sense out of. Which is fine by them.
You also see the same thing in religious fundamentalists. Quick to resort to shit-throwing and claiming they’re being oppressed and mistreated, just because everyone doesn’t agree with their arbitrary notions on how the world is.
The discussion on the Internet, which we’re not having here, seems to be that this person is, basically, mad and an attention whore. Does their cause no good. Sensible people know not to take the loonies as representative of the whole, but there’s always been a shortage of sensible people. And politics in a wider sense has gone right down the toilet, so calm reason and rationality is not something you’ll ever hear in the media or politics.
I am very surprised about what you say regarding autism and gender identity.
All those who I have cared for, and who may be described as autistic, have been pre-teen or adolescent so I have no grounds to argue the matter.
So I will stick to what I do know.
Autism is a spectrum which we all exist on. It’s a quality that all humans have to some degree.
Did you know that in the early days NASA employed autistic mathematicians because their attention to detail meant that would not make the mistakes more average people do.
Autism is a difference to average and it has attributes that are an advantage over an average person and some attributes that make life a harder – mostly through non-acceptance.
“Autism is a spectrum which we all exist on.”
No it’s not. It’s not like some sort of Kinsey scale of social awkwardness. It’s an actual developmental issue that results in typical symptoms and traits. Just because “neurotypicals” sometimes exhibit some of those same traits to varying degrees doesn’t mean they’re a little bit autistic – any more than having a bit of a cough means you’re slightly turberculotic.
Those on the spectrum have actual neurological and developmental issues, those “on the spectrum” (often self-diagnosed) are simply put there by correlating a checklist from the DSM without proper diagnosis.
“You know autistics are over-represented among people who claim to be the other gender.”
You’re mistaking cause and effect: self/mis-diagnosed autists are prevalent in any group of people who are narcissistic/egomanic because it is a convenient excuse for acting poorly in relation to other people. Autism does involve difficulties in developing what’s called a “theory of other minds”, where a child at some point of growing up realizes that other people have minds of their own, which leads to a kind of self-centered intuition about the world, but this is not the same thing.
Gender dysphoria is all about the person’s self-image much like with anorexia or compulsive body modification through cosmetic surgery, or the desire to be amputated, and so transgenders tend to be or become highly self-centered, sometimes to the point of solipsism, as they battle with their mental illness – and it is a mental illness. Aside from people born with ambiguous genitalia and other actual cogenital issues, people who simply suffer from the desire to change gender can be effectively treated with antipsychotics.
The only problem is that transgenderism isn’t politically considered to be a mental illness, so the people with gender dysphoria can’t get proper treatment. Instead of giving them antipsychotics, people try to accomodate their illness and even let them get cut up and put them on hormone replacement treatments, which doesn’t end up nice because the underlying mental illness doesn’t go away and the people often end up killing themselves.
Twin-studies have shown gender dysphoria to be heritable – that is to say of biological cause – about 60% of the time. That means a bit less than half of the transgenders out there are not genuinely so, but suffering from some kind of psychosis or other issue that is not helped by everyone pretending that Tom is Jane or vice versa.
The crazy transgenders are often actually schitsophrenic – the reason they think they’re the other gender, or what they think is “other gender” and what that means to them, is a cognitive distortion, and those can be any odd association or behaviour, such as a person who thinks “the number three is listening because it has a nose”. It’s a sort of cognitive synesthesia – mixing of thought and meaning – or commonly known as having your wires crossed. It doesn’t necessarily need to make any sense, and usually there’s more than one such distortion which makes these people generally difficult and unpleasant to interact with.
And then there are the transtrenders, who claim to be transgenders without any offical diagnosis simply to gain attention. Being attention seekers, they’re again narcissistic/egomanical and ultimately unpleasant to interact with.
@[Dax]
since DSM-IV
You mean body hackers… I mean I’m not pro any of that stuff but this is hackaday heh.
Body modification is body hacking, transgender is a completely different thing… And no matter if you are pro or anti it isn’t relevant, not your life – not your business.
People that do such things have a strong tendency to make it everyone else’s business.
Ok, if it is about people and not “Libreboot” per se, that is a different story. Everyone is entitled to privacy.
> sounds very much like censorship.
Technically correct, but I would call it a ‘chilling effect’. Self-censorship. The Hackaday audience – and tech in general – skews heavily authoritarian and conservative. We’re not touching that with a 20 foot pole.
+1 on your decision to not start a discussion on libreboot
-1 on being able to stop discussion on libreboot.
speak of the devil and he will come
> The Hackaday audience – and tech in general – skews heavily authoritarian and conservative.
that actually takes the cake for the most astoundingly bizarre thing you’ve ever said.
Hard to tell. This is Brown Pinchoff we’re talking about.
Sounds like HaD’s just scared of the social justice warrior cult.
Libertarian conservative here…. (not voting for Johnson btw because he is neither libertarian or conservative.)
I personally don’t care what people do… until it affects other people that’s Libertarianism in a nutshell. Many things people do that Johnson is for affect other people a lot… pot legalization , TTP , pandering to people that wish to destroy the prevalence of the family unit… etc… In short I expect people to take responsibility for their actions, something many liberal “libertarians” *cough* democrats/neocons think is somehow reprehensible.
Then it would’ve been better not to mention it at all. By mentioning it, you brought it up. Get good, scrub.
Libreboot != situation around libreboot. I’d say someone has quite a low expectations of his audience. Ability to not engage in emotionally-loaded discussions which are not based on arguments supported by facts is, in my opinion, the very basic skill any tech person possess. You do not select your resistor or capacitor because it is pretty, you like it, or it would look rad next to the chip – you analyze the requirements and select the optimal solution. Why would be such skill suddenly lost when, %deity forbid, the topic changes from tech to whatever else?
Personally, whenever i am dealing with either a physical piece of equipment or software, i have zero interest in sexual, culinary or fashion -related inclinations of the person who made the thing. On the other hand, whenever i am out in the bar in search of non-procreation-aimed sex, those topics become relevant and programming//machining skills are not. But that’s me. It might be different for you and it is quite OK if you require your one-night partner to have a degree a metallurgy (everyone can have his/her kinks). Those qualities of yours are irrelevant to me, as i am interested in you as one of HaD writers. However, your judgement of topic suitability is a relevant quality and i find it flawed. Have some faith in your audience, or, better yet, study your audience and learn to know it.
Cheers,
“The Hackaday audience – and tech in general – skews heavily authoritarian and conservative.”
Seems highly ironic, as hacking is all about breaking ‘rules’ to achieve your goals.
(I believe you, it just sounds strange to me)
Lol wut? Have you been to Reddit or Slashdot? “Conservative”, they are not. “Authoritarian”, maybe.
Lol wut? I’m very conservative… but not authoritarian.
Learn your history, free handouts, false promises and authoritarianism go hand in hand… conservative ideals based on the value of the individual and the government getting out of the way of individuals while regulating large corporations that would otherwise wreak havoc on the little guys. I live in NC and the only reason nobody has gigabit internet here anywhere but like 2 towns + google fiber in a few neighborhoods is the fault of politicians and lobbyists.
Currently we have the opposite, lobbyist strangling the little guy… no innovation, politically driven business/product development, etc…
> The Hackaday audience – and tech in general – skews heavily authoritarian and conservative.
You sure? There certainly are people like that here, but quite a few in the other direction. There’s a good mix here. If there’s any common culture here it’s pretty much just an admiration of technology and people doing cool shit to stuff that’s not supposed to be possible (ie hacking).
If there is a skew, and I must’ve misplaced my HAD Census Form, I wouldn’t call it a heavy one.
“Don’t jump into that there Briar Patch”, said Br’er Benchoff, so we’s all jumped right in.
Had to look up. I wanted to know what the fuss was.
Here is a link I found.
https://libreboot.org/gnu/
Looks like libreboot took sides on an issue where the free software and allied movements would do best to avoid any entanglements.
You may not share there belief in this case (or you may) but in any case would you prefer to deal with an organization that is morally vacant.
Some debates there is no position you can take without some people calling it immoral.
It’s about one individual who claims to have been discriminated against and bullied, and a bunch of people who deny that. The individual in question has been described by people who know that individual, as not the sanest and most stable of individuals. A one-individual screaming shitfight. The FSF made a statement denying any discrimination, and say they go as far as “safe spaces” in their events, etc, and have anti-discrimination policies.
Depends who you believe, but for all that it matters it seems to be one person complaining about three others. It’s not really important to free software and software in general.
What’s bad, whether or not it applies in this particular case, is that calling people bullies has itself turned into a form of bullying. Claiming people are victimising you, then calling down hell and damnation on those people, itself can be an easy way of abusing people. Bystanders, who may or may not be acting in good faith, can be manipulated easily into following one person’s agenda, by applying the right logical short-circuits and snarl words.
Portraying victims, or putative victims, of things as automatic heroes with intrinsic moral high ground, is one place culture went a bit wrong a couple of decades ago. Blame Oprah Winfrey. Most people won’t abuse that, but some others are completely shameless.
Do a search on “tyranny of the minority”
This twitter thread is a good summery of what is going on, for the disaster voyeurists among us:
https://twitter.com/markhkim/status/777477509579407360
Basic gist, there is probably a fork coming in Libreboot’s near future.
They are asking over 500€ for a core2duo, so yeah, kinda crazy lul..
Do whatever you want, you cpu will be running micro-code and in any not museum grade laptop there wil be Intel ME doing what it wants, so much for over the board so called open source bios..
I’m all in for fully unlocked BIOS, and shit like Insyde H2O could die..
Also there is this:
https://libreboot.org/gnu/
So that is why..
And EC firmware, and eMMC / HDD / SSD firmware, and touchpad firmware, and NIC firmware, and boot ROMs in those devices that fetch the firmware… Just because it’s not included in the primary CPU BIOS doesn’t mean it’s not there.
Open source replacement BIOSes have their hearts in the right place. But unless you want to go back to the stone age where all firmware is in parallel ROMs that run at PC=0 on reset, you’re going to have to accept some opaque code somewhere in your machine.
You’re probably right, but it’s nice to see people trying to fight back. On that issue, was it Sprite_tm who managed to run Linux ON a hard disk? On the disk’s own ARM controller chip? Yeah there’s only so much you can trust. Stuff like encryption can help, where it’s done as close to the user as possible so only encrypted data, worthless to spies, gets passed through most of the levels of the system.
Open source BIOSes are a good start. The other stuff can come in time. FPGAs might offer a nice option, bringing custom hardware into ordinary people’s reach, so stuff like NICs and maybe even SSD controllers can be brought back into the ownership of the guy who actually paid for the machine. SSDs in particular are nice, since writing custom code to run a mechanical hard drive is gonna be a bit of an effort. SSDs in comparison are just memory chips, well understood, so with copies of the right specs a bespoke full-custom SSD isn’t beyond the abilities of alpha-level hackers like Bunnie or Jeri.
And then once it’s written, it can make it’s way around the world, people can check the code and compile their own hardware.
Of course you have to trust the FPGA, but since they have so many uses, trying to put spy-hardware in there, for very specific and particular uses, is beyond practical I think. Since Xilinx have no idea which one of their chips is going to end up as a NIC, SSD controller, or graphics chip.
Yah Insyd bios is literal garbage.
this secure to the last bit problems are purely philosophical, basically you only need to secure your network , when your computer can’t talk without your permittion, it doesnt
There are many other ways to ex-filtrate data than through the network. The only safe computer is the one that’s unplugged, turned off and placed in safe at the bottom of the Mariana Trench – and even then I’m not sure it’s safe…
If you want to don a tin-foil hat with me: microcode in processors is the same thing as keys to the kingdom. You can secure your network all you want, but if there is hidden microcode in the processor of the router that listens on either side (Internet coming in, or another compromised device inside the LAN) you are not secure and you will have no idea.
The philosophical question becomes when do we start caring? When these systems are installed in government facilities? Banks? Utilities like power plants? Your Mom’s new tablet? I always see this argument as one where caring a little bit will help keep the proliferation of back doors at bay.
Microcode is nothing once you realize they can hide entire processor within your processor…. without a thorough reverse engineering and audit of the silicon you have little to no idea what all of it does.
There is also a limit to what microcode can do…. it worries me less than unidentified silicon. Also I think most people conflate microcode with firmware (Intel ME has a firmware not a microcode… that firmware probably has microcode in it… but it’s an independent sub processor in the main x86 cpu)
That power management sub processor… is that all it does? Do these power PC chips ship with built in engines that are just as bad as Intel ME etc.. chances are that yes it is baked in just a bit deeper than in Intel or AMD chips.
At least on older Opterons (I haven’t kept up with the last few years) the first instruction cycle executes hundreds of thousands of microcode ops out of the microcode ROM. It takes this complex code to initialize clocks, set up voltages, bring up the Hypertransport SerDes links, map the Hypertransport network, find the southbridge, duke it out with other Opterons on the fabric over who is the BP, and fetch the first page of BIOS flash on the southbridge into cache. After that the first BIOS instruction executes.
After BIOS comes up, microcode patches can be loaded to amend microcode to modify other housekeeping tasks.
Didn’t quite get why we trust POWER/IBM more than x86/Intel/AMD… :-) And even if POWER would be open sourced (I don’t believe it currently is, despite of confusing OpenPOWER name), other essential hardware blocks such as DDR3 controllers, PCIe, USB hosts, Ethernet controllers, etc. are most likely to be a proprietary intellectual property…
Cos Intel / AMD have the “Management Engine” which is basically a massive backdoor right in the middle of the chip. If POWER also has one, we don’t know about it. That’s the reason, basically.
As for the rest, one problem at a time. It’s a start, and maybe if they sell enough of these they can start developing or sourcing alternatives. Though motherboard chipset makers tend to be Chinese megacorps so it’s not going to be easy. Wonder how much of a DDR3 controller you can implement in 7400 TTL?
So chose the “We don’t know if there is a devil.” over “We know there’s a devil, but we have no idea if it’s really evil.”?
for $4k it seems like you could buy a fairly high end FPGA dev board and instantiate a bunch of SPARC cores from HDL. yeah, you don’t know that Xilinx didn’t slip something into the FPGAs for the NSA, but the odds that they could put some sort of universal data exfiltration mechanism into an FPGA (that will then work with an unknown board) is much slimmer than the chance there is already one in the POWER processors.
I like this option the best. The contrarian thinking against Microsoft and intel just leads you to places that are just as compromisable. Also, isn’t this the idea behind some of those ‘secure’ OSes? Virtualization inside of sandboxes?
Like Qubes OS ? “
A secure computer is easy. Just don’t connect it to the internet.
Or install anything on it you haven’t hand assembled.
And make sure it is TEMPEST
Perhaps DDC could be extended to general computations, obviating the need for line by line verification? http://www.dwheeler.com/trusting-trust/
Since when? has security been architecture dependent?
Perhaps in our current failed model of security we can offer some small graduation of security to architecture.
I hope a change in architecture (a new architecture) will cause a software security re-think but new hardware that has a new architecture and is used to run a current OS is just as non-secure as the OS always has been. If you run Windoze on it then is it secure?
No one is buying this to run Windows…
As you say, caring about BIOS source code is completely irrelevant if you’re just going to put 10GB of binary blob OS on there.
So what can they put on it that is secure? There is noting in the list they provide that I would consider secure.
Acid Burn had a clear computer? Not Zero Cool?
Apply Thompson’s Turing award lecture, “Reflections on Trust”, demonstration to a VHDL compiler. What hidden features would you like to put in customer ABC’s new chip? Hack the design tools and you have hacked everything built with them. You can be sure all the intelligence services have been working on this for a long time. Both doing it and detecting it.
There’s a huge market for a trusted computer. Every government. But none want to trust anyone else. And Thompson demonstrated that a source code audit of the compiler is NOT sufficient. I’ve long wondered when someone would discover that gcc in a major Linux distro had been subverted.
Half formed idea…
Three CPU, different source, different architectures, running VMs, and they vote on every meta VM instruction to execute, which controls all reads/writes to anything.l… in ROT13 ;-)
NASA did something like that on the Space Shuttle. I think 5 computers (so if one goes down, you turn off another and still have 3 left to carry on voting without a tie) in a voting configuration.
Problem is WHAT those instructions are. If you’re running Windows 10 your CPUs can vote all they like, you’re still Microsoft’s bitch. In practice, for any one individual to know every bit and gate of his computer is not possible. Still, doesn’t mean you can’t trust anyone, just that some organisations are more intrinsically trustable than others. Depends on their motives, and who their “friends” are.
That’s what made me think of it, the shuttle computers.
My pet rock is pretty secure. I think.
What if those quartz crystals in it are picking up your voice and converting it to radio waves…..
Why do you think I wear the tinfoil hat then? For fashion?
I’ve worked on many secure systems, primarily they are built around trust and there are blobs involved but you know what gave good value for money? Paying ex-Intelligence Services security consultants to hack them in to oblivion, we’re not talking about your average pen testers here, these guys are chip shavers and bus tappers.
$5k for a POWER8, okay given the chip costs quite a bit anyway, but as secure workstations go I’d rather just use an ARM CPU with trust zones and know that it has been validated by security researchers.
How do you validate the “ex” ?
I wonder if a cheaper version based on the PowerPC e6500 QorIQ SOC or similar would be possible?
It’s not as fast as a Power8 but still would be much faster than an Arm and even many recent X86s.
POWER9 ?