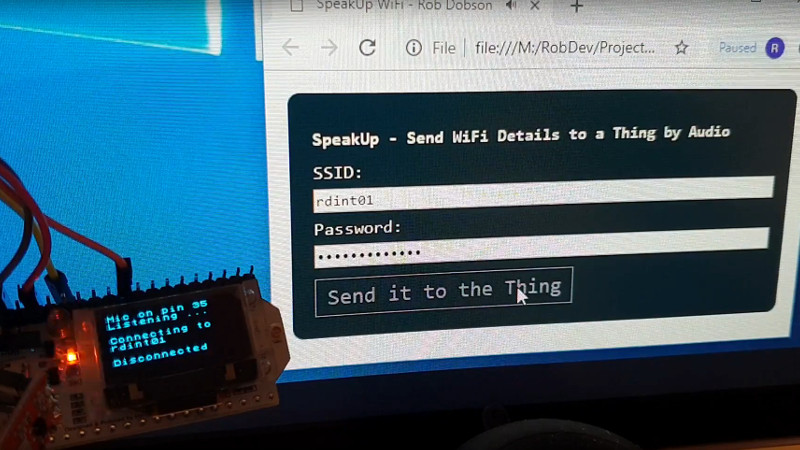
When you create a Thing for the Internet of Things, you’ve made a little computer that does a simple job and which probably has a minimal interface. But minimal interfaces leave little room for configuration, such as entering WiFi details. Perhaps if you made the Thing yourself you’ve hard-coded your WiFi credentials in your code, but that hardly translates to multiple instances. So, how to put end-user WiFi credentials easily on more than one Thing? Perhaps [Rob Dobson] has the answer with his technique of sending them as a sequence of audible tones.
There is a piece of Javascript code in a browser into which you enter your WiFi credentials, which are then expressed through the speaker as a set of FSK tones to be picked up by a microphone on the Thing. They can then be decoded into the credentials, and the Thing can connect. All the code is available, on GitHub, should you fancy it yourself.
Of course, this is nothing new, as any owner of an 8-bit machine that had a cassette interface will tell you. And on the face of it it’s much easier than those awkward impromptu hotspots with a web interface to which you connect and pass on your credentials. But while we quite like the convenience, we can’t help wondering whether expressing the credentials in audible free space might be a bit too insecure for many readers. The technique however remains valid, and we’re sure that other less sensitive applications might be found for it. Meanwhile we hope he hasn’t inadvertently shared his WiFi password in the video below the break.















Great job! The only hitch with this one is that you need the website files already on the other device. Whereas making the ESP32 and AP it can serve up its own credentials page, then connected to your AP.
The impromptu access point reutilizes both the hardware (WiFi) and software (TCP/IP stack) the device already uses during its normal operation, while this solution adds a piece of hardware (microphone) and a software subsystem (audio processing) which serve no other purpose than WiFi setup unless your Thing does audio processing. The AP is an elegant solution, this is a funny hack.
And yet Amazon still put this (and Bluetooth) into its “free” dash buttons…
I think that has more todo with ease of use & idiot-proof, otherwise they would gladly decrease their BOM cost.
If the thing has a microphone, why can’t it have a headphone jack instead? Then just use an aux audio cable. No security issues and much better reliability. This is assuming you want to program it with a smartphone. .
New smartphones don’t have 1/8″ jacks, seems silly to design it using an obsolete connector. If you’re going to connect it with a wire, why not use data over USB at that point? Save yourself from having to use a strange audio protocol and DAC / ADC.
I think the whole point is that you can transfer the authentication data remotely without having to hook up anything. It could authenticate any number of devices within earshot simultaneously.
Of course that also presents a security risk–if this took off and had a high rate of adoption, you’d have people putting bugs in offices or pointing laser/parabolic mics at windows to penetrate those networks when somebody decides to pair their new IoT thingamajig. Of course trading security for a slight increase in convenience is the defining property of IoT in any case. Why get up and flip a lightswitch when you could let Amazon/Facebook/Google do it, plus mine the data and sell it to dubious psycho-marketers on the internet who will analyze if you have seasonal affective disorder and leverage that info to sell you crap at just the right moment. Or something. I dunno, I’m probably going crazy with paranoia as I get older. But I feel like infosec paranoia is special because unlike other nutty conspiracy theories, it almost always turns out to be correct over time.