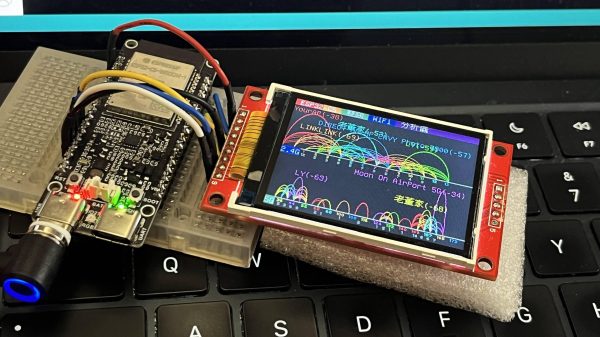
Wi-Fi! It’s everywhere, and yet you can’t really see it, by virtue of the technology relying on the transmission of electromagnetic waves outside the visual spectrum. Never mind, though, because you can always build yourself a Wi-Fi analyzer to get some insight into your radio surroundings, as demonstrated by [moononournation].
The core of the build is the ESP32-C5. The popular microcontroller is well-equipped for this task with its onboard dual-band Wi-Fi hardware, even if the stock antenna on most devboards is a little underwhelming. [moononournation] has paired this with a small rectangular LCD screen running the ILI9341 controller. The graphical interface is drawn with the aid of the Arduino_GFX library. It shows a graph of access points detected in the immediate area, as well as which channels they’re using and their apparent signal strength.
If you’re just trying to get a basic read on the Wi-Fi environment in a given locale, a tool like this can prove pretty useful. If your desires are more advanced, you might leap up to tinkering in the world of software defined radio. Video after the break.