When one of [Christian Haschek’s] co-workers found this Raspberry Pi tucked into their network closet, he figured it was another employee’s experiment – you know how that goes. But, of course, they did the safe thing and unplugged it from the network right away. The ensuing investigation into what it was doing there is a tour de force in digital forensics and a profile of a bungling adversary.
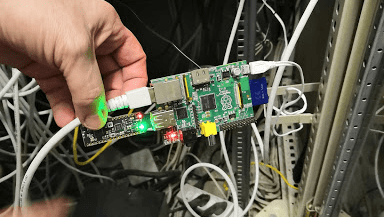
A quick check of everyone with access to that area turned up nothing, so [Christian] shifted focus to the device itself. There were three components: a Raspberry Pi model B, a 16GB SD card, and an odd USB dongle that turned out to be an nRF52832-MDK. The powerful SoC on-board combines a Cortex M4 processor with the RF hardware for BLE, ANT, and other 2.4 GHz communications. In this case, it may have been used for sniffing WiFi or bluetooth packets.
The next step was investigating an image of the SD card, which turned out to be a resin install (now called balena). This is an IoT web service that allows you to collect data from your devices remotely via a secure VPN. Digging deeper, [Christian] found a JSON config file containing a resin username. A little googling provided the address of a nearby person with the same name – but this could just be coincidence. More investigation revealed a copyright notice on some mysterious proprietary software installed on the Pi. The copyright holder? A company part-owned by the same person. Finally, [Christian] looked into a file called resin-wifi-01 and found the SSID that was used to set up the device. Searching this SSID on wigle.net turned up – you guessed it – the same home address found from the username.
But, how did this device get there in the first place? Checking DNS and Radius logs, [Christian] found evidence that an ex-employee with a key may have been in the building when the Pi was first seen on the network. With this evidence in hand, [Christian] turned the issue over to legal, who will now have plenty of ammunition to pursue the case.
If you find the opportunity to do some Linux forensics yourself, or are simply interested in learning more about it, this intro by [Bryan Cockfield] will get you started.















“But, how did this device get there in the first place? Checking DNS and Radius logs, [Christian] found evidence that an ex-employee with a key may have been in the building when the Pi was first seen on the network.”
I imagine was a current employee at the time so there may be some complicity here. Hopefully key was taken away soon as ex-employee.
Come on Ostracus, finish reading the article at least… From the article’s summary:
> That deactivated account belongs to an ex employee who (for some reason) made a deal with management that he could still have a key for a few months until he moved all his stuff out of the building (don’t ask..).
Mr.Robot anyone? Or is it too obvious.
Old project installed and forgotten. Happens when there is no one actually responsible of installed equipment (or responsible is sacked).
Yeah this is a fair point. When I first read the article they sounded pretty guilty. After reading your comment though and thinking about it a bit.
I have embedded machines and a couple tiny openwrt routers plugged into a couple spots on our network. Part for fun and part to monitor our Wifi network and remote access for work (Developer aka pseudo IT person as its a start up). Oone of the devices is a PI running backtrack and some wifi sniffing tools for rogue network monitoring. If I left or was fired and a new employee stumbled on them I am confident they’d come to the same conclusion.
Hopefully they are diligent here it doesn’t end up potentially ruining an innocent person just playing around.
Thanks for making me consider the other side. :)
ah.what a little tape with a telephone number and n name on it could do to this confusion.
LABEL IT or its mine is our hackerspace motto
“LABEL IT or its mine is our hackerspace motto”
B^)
Seriously, try reading the article. This is not what happened.
Next to impossible to tell when he put it there. It could easily have been from when he was an employee. I worked at a place that an ex employees computer ran for many years unnoticed. It never would have been noticed but it finally crashed and did not restart and he served a web page from it. We got a note that a link on our site was broken and when we looked into it, it turned out to be pointing at his old computer. Along the same lines, when I left my last job I am 99% sure they left my stuff intact. We had got bought out by another company and I had the last vestiges of old software that was occasionally needed on my share. Also for years after I left, I got cron reminders from one of the servers there. I had a few things that I set up to send to all my work and home addresses. I always got a kick out of getting mail from that old system. It was still going when they retired the building that it was in.
Not really impossible to tell. The config files for the pi would probably have a timestamp from when they were created and last edited. Just checked an SD card I used for a PI zero and license.Oracle shows a time and date of 26.6.18 2:22 the dates on all of the other files match when it was last turned on.
And why would you trust the time stamps? You may have a bit of an iron clad not before some date by the OS itself and it’s release date.
According to the article the DHCP logs show it showed up post firing.
Are you sure this device was placed after the employee left? It seems he took no precautions at all the prevent discovery, so I think it is not so likely.
Only recently it was discovered that a device that was part of a measurement campaign at my old work was still connected to the network. Everyone responsible had already left as the project was completed. Fortunately it was marked with contact information.
Does it really make a difference? An unauthorized device connected to the corporate network is a fireable offense all by itself already (or at least a good reason to invite the perp for some tea and biscuits).
Worse, it certainly didn’t need wifi for network connectivity since it had ethernet and you wouldn’t use that particular dongle for “just wifi/bluetooth” – it is a wireless development kit from Nordic Semi that allows you to get low level network information over a serial connection (and to do a lot of other wireless shenanigans). So we have an unauthorized device sporting what looks for all purposes like a wifi & bluetooth sniffer and is opening an unauthorized VPN out of the company to boot – that is not only fireable offense but a reason for getting the police involved.
I think the part with no precautions to prevent discovery is more about a cocky kid being clueless than this serving some legitimate purpose.
“(…invite the perp for some tea and biscuits). ”
Tea and biscuits! Where? When?
Similar scenario: https://www.youtube.com/watch?v=UeAKTjx_eKA
Based on the source article it sounds like 1. It was installed post firing “That deactivated account belongs to an ex employee who (for some reason) made a deal with management that he could still have a key for a few months until he moved all his stuff out of the building (don’t ask..).”….wtf? 2. While the device has been found and neutralized, I wonder, how much more they could be done. It seems the device was there in part by permission, and while we know that the combination of devices is likely a wireless keylogger for RF keyboards the fact that the whole setup was so conspicuous means that wither the installer knew how lax IT was or that it wasn’t really used for nefarious purposes.
Just a sidenote: the nRF52832 cannot do WiFi (https://devzone.nordicsemi.com/f/nordic-q-a/10334/wlan-support-for-nrf52).
So this thingy can only sniff around in blue tones.
Quite correct. I thought maybe the article was trying to imply that the Pi had a WiFi dongle that was part of the mix, but does not appear to, and it’s a model A (!), so no WiFi here!
the larger lesson to be learned here is to put a lock on your “network closet”
There is a giant, bolded section about this on the actual page linked in this article that could read if you wanted.
Cable management
Should have 3d printed a case that looks like a POE injector if he wanted to not get busted.
Why 3D print when you can just put it in a POE injector case.
Heck, whenever we find things like this plugged in to the network, we don’t suspect spying – we groan, because we know it means that yet another IT network security audit is in progress.
Something I’ve always found odd is that often when you hand your notice you get perhaps 3-4 weeks of work left during which time most companies leave you to finish up what you are doing.
Despite the obvious security risks involved.
I’ve always been of the frame of mind that it would be better to let them go home and call them in as needed and supervised to pick out the gaps in the knowledge of the people left behind. This typically happens with sales but few other positions.
This ex-employee may well be a douche bag.
But still having admin access to a system during your notice period is also a DIY dick move and you should give it all up the day you hand in your papers.
Putting yourself in a potential blame scenario should SHTF like your soon to be ex-company not liking the situation and trying to blame things on you – AKA you’re doing a ditch and run. But that’s never happened, right? :)
The ex-employee may have made a duplicate set of keys, and the workplace might not have used RFID badges,
(not that it would’ve been more secure.)
In the case of Sales, most companies will terminate you upon receiving notice.
There would be too much temptation for the leaving employee to take customer lists to the next employer.
What sales guy doesn’t have already a copy of the customer list when shopping around for the next employer?
Most people are honest and play by the rules. But some don’t. I agree, when you give your notice, hand in your credentials right then and there. If your management wants to hand them back, that’s on them.
Why is it a “dick move” to expect the employee to work until he leaves? I think that’s a very strange way to look at things.
It’s not that weird. For surprise firings, sure of course. But for layoffs, or people leaving for other jobs? The real world is messy, and when I’ve left jobs there’s always a lot of documentation that needs to be done for the hand-off. I think it many situations its a totally reasonable risk to take. Also, it’s just rude to take someones credentials, and then ask them to keep working while handicapped. It’s bad practice to burn bridges in business unless you have no other option; and that applies to employers as well as employees. You might need some info from them in the future, and they’re probably friends with current employees.
IMHO it’s risky. I’ll wager we’ve had different experiences – I’ve had to take employeers to court (and won) over redundancy because they’ve been assholes and withheld pay. Burning bridges.
The person is either essentially already left in their mind, in the case of redundancy being made to go by the company.
Certainly in the latter there isn’t any good will yet the company will still ask you to work.
Whilst you’re wondering how to pay the rent, and they are trying to get out of severance pay. Madness.
But once someone is leaving there is an opportunity to find the gaps in the rest of the team. That should be the priority, everyone else trying to do the job the leaver did and asking them where there are gaps.
Which isn’t the same thing as the leaver doing the typical 9-5 during their notice period.
Too often employeers tend not to see the bigger picture and will leave them on a project, only to find 2 months after they left there is a process no one knows about.
Where I work currently there is a secrecy around people from other teams leaving for unknown reasons. So sometimes you find out on the day they are leaving when they send out the bye bye email. Then it’s a scrabble to find out who is now responsible for their workload and no one wants to volunteer.
Big corporate stupidity.
I can also think of a scenario where the former employee had built a lot of jigs/devices useful to the company, and the company knew they’d be marooned if the employee took them all the day he left…
It should take seconds from even looking at the picture to figure out it’s a wireless backdoor in to the server..
i can only pray you never get jury duty with that keen discriminating mind of yours.
or maybe you were joking, in which case lol ya got me! :)
Well an obvious proto board in a server rack connected to the subnet with ethernet cable and a obvious USB SDR or WIFI board… You don’t exactly need IDA or SD card analysis to figure out if it should be immediately disconnected..
If I owned it and an IDS didn’t alert the admin someone would be getting fired..
If the picture is actually of the device in question, then I guess it has been there on their network about 8 years or so, or some geek was cleaning out their closet and throwing away their oldest Pi in their collection.