Security researchers have found a way to remotely execute code on a fax machine by sending a specially crafted document to it. So… who cares about fax? Well apparently a lot of persons are still using it in many institutions, governments and industries, including the healthcare industry, legal, banking and commercial. Bureaucracy and old procedures tend to die hard.
This is one of those exploits that deserve proper attention, for many reasons. It is well documented and is a great piece of proper old school hacking and reverse engineering. [Eyal Itkin], [Yannay Livneh] and [Yaniv Balmas] show us their process in a nicely done article that you can read here. If you are into security hacks, it’s really worth reading and also worth watching the DEFCON video. They focused their attention in a all-in-one printer/scanner/fax and the results were as good as it gets.
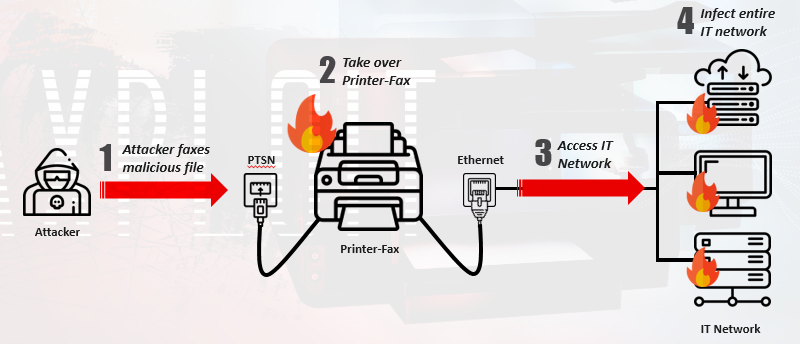
Our research set out to ask what would happen if an attacker, with merely a phone line at his disposal and equipped with nothing more than his target`s fax number, was able to attack an all-in-one printer by sending a malicious fax to it.
In fact, we found several critical vulnerabilities in all-in-one printers which allowed us to ‘faxploit’ the all-in-one printer and take complete control over it by sending a maliciously crafted fax.
As the researchers note, once an all-in-one printer has been compromised, it could be used to a wide array of malicious activity, from infiltrating the internal network, to stealing printed documents even to mining Bitcoin. In theory they could even produce a fax worm, replicating via the phone line.
The attack summary video is bellow, demonstrating an exploit that allows an attacker to pivot into an internal network and taking over a Windows machine using Eternal Blue NSA exploit.
Just to show how legacy a tech fax is, did you know that the first experimental fax machine dates back to 1843? Yep, you read that right, even before the first phone line.















lp0 on fire
Impressive. I had no idea the fax protocol could support jpeg. Key weakness was that HP rolled their own jpeg handling library rather than re-use a tried and tested option like libjpeg.
Then they would have to release their sources.
Was libjpeg mature and ready to be used at the time the fax machine was being designed? was the license permitting such usage without forcing HP to release the full firmware source?
libjpeg was initially released in 1991, so it was probably plenty mature by the time HP engineers started working on the firmware for this printer, and it’s under a BSD-like license. That’s not to say that they didn’t have a good reason not to use it — it’s just not license or maturity.
HP has a long history of networked printer exploits. You would think that after almost 30 years of JetDirect they would be better at input sanitizing and bounds checking.
PC LOAD LETTER? What the F@(# does that mean?
(Slaps paper tray off machine)
Patch has been issued:
https://www.youtube.com/watch?time_continue=12&v=g_hF_RhD-xE
Try to hack an old-school thermal-paper fax. That’s where the fun is.
I’m sure it would be more fun, and probably would use a more transparent architecture. But not network connected so less exciting for the security crowd.
9/10 IT Professionals agree, Printers are Evil.
Remember kids, save a forest, kill a printer!
“The attack summary video is bellow” – Bellow?!
Every blacksmith knows you need a bellow to get the fire really hot.
They found an exploit in a specific version of a specific fax-printer device. The question “How many fax numbers are in use?” is irrelevant. The question must be: How many of thse fax-printer devices are still connected to the phone network?
Note that “how many were sold?” is also irrelevant. I have a multifunction device that happened to have “fax” as a feature, but I’ve never used that feature (i.e. it’s not hooked up to the phone network).
Just because you don’t use the device doesn’t mean that the majority of banks, hospital/doctor office, real estate, and practically every other established business do not.
Fax is considered legally binding for some pretty heavy financial transactions. A bank is likely to use the same machine system wide, so a single exploit is a major problem.
The question is not “how many people use a Fax machine” but “how many people have this exact model of vulnerable Fax machine hooked up to the phone line and therefore are vulnerable to this exploit”
Not even phone line. Fax has adapted and can run over IP. See if your multifunction has something like iFax.
“Security researchers” ehmmm… why aren’t these kind people called hackers? With a trick like this, I think that they’ve really earned that title!
Presumably the difference between a “Hacker” and a “Security Researcher” is whether they pay more in laundering fees or taxes.
There was a conference about this from the same guys in 35C3 this winter.
https://media.ccc.de/v/35c3-9462-what_the_fax
Question:
At home, i have a LAN for 2 cell phones and one HP7520 AllInOnePrinter. My motorola Surfboard Modem-Router has these 3 addresses; and at home the cell phones connect via my modem-router Cox Cable Service;
Every time I physically leave my home environment, my 2 cell phones go to external Internet connection and work fine; when I return home, both reconnect to WiFi ,,,,,, NOT to the Cox Cable Service Net but to my Printer’s WiFi Address.
Hence, I must reconnect WiFi manually to the internet for Internet Cable Service!
?Does this mean that the BoggieMan has hacked my system?
PS
The very 1st Hackers were Plumbers which prevented our shit from being sent to the world
via the ocean.
sounds like your phones have prioritized the all-in-one’s internal SSID instead of your internet router. delete the AIO SSID from the saved network list, or bump the router’s one back to top of the list.
unless you’re important enough to know you need real infosec to protect valuable information nobody is hacking into your home network.
Thanks,
I’ll give it a go!
Ok, so how many here remember the “Love Letter Virus”?
That one was written in vbscript and spread via MS Outlook. I can’t say that I had a good opinion of Microsoft before but that one pretty much cemented my opinion that Microsoft products should not be taken seriously in a production environment.
Anyway, here’s the fax machine connection. Love Letter used Windows/Outlook’s contact list to spread. It wasn’t particularly picky about what kind of address it attempted to spread to so several copies of it sent themselves to the fax machine at my workplace. Fortunately the fax machine did not know what to do with vb script so it simply printed it out for all to read, pages upon pages of vbscript code. Whoever wrote that virus murdered a forrest.
I picked up a handful of this wasted paper and read a little. Prior to this I had no real knowledge of vb script other than an awareness that the whole Mickeysoft suite, Outlook, Word, Excel, etc… allowed vb script to be embedded into documents to make them more interactive, kind of like how javascript is used in web pages today. Or at least that’s all I thought it was for.
Apparently vb script was written to be a complete system management tool. It allowed administrators to embed even the most sensitive administrative tasks in an easily shared document. Apparently Microsoft admins are the ultimate script kiddies!
In that wad of paper I saw references to built in vbscript functions for editing the registry, accessing the address book and sending messages. Because those are the kinds of functions a document should be doing right? I had assumed that whoever wrote viri must be some sort of sevants. They must be using buffer overflows to pry into just the right points of memory like some old 80s BASICA programmer using undocumented CPU features via PEEK and POKE. Nope, they are just calling obviously named and easy to use functions. Microsoft Office Suite was basically a viri toolkit no more difficult to use than a lego set!
It would appear that Microsoft has somewhat addressed this situation in the last couple of decades. But they haven’t done it in the obvious and reasonable way. Instead of removing these features which never should have existed in a document and email system they have just added a much more complicated (and complicated means more room for error) system of permissions. The unsafe functionality is still there.
I know someone will read this who is a fan and uses this stuff to administer some collection of many Microsoft servers and workstations that they wouldn’t know how to manage any other way. I have no sympathy though, that stuff should be automated with batch files and remoted with the net command, not via email, documents or spread sheets.
VB is a fully featured programming language with uses outside of Office. So you can code… anything.
To make your point more precise, I think you would prefer that code executed by Office apps be sandboxed so that it can’t access the system.
In my school, someone made a looong paper with dicks drawn on it, and faxed it to the principal, taped the ends of the paper to create a infinyty loop and made the recieving fax run out of paper,,,
It was just loaded with a new box of tractorfed paper
I ididn’t see who did it, I just saw the hands…