You’ve got a machine hooked up to the Internet via a shiny new cellular modem, which you plan to administer remotely. You do a quick check on the external IP, and try and log in from another PC. Try as you might, SSH simply won’t connect. What gives?
The reality of the modern internet is that most clients no longer get their own unique IPv4 address. There simply aren’t enough to go around anymore. Instead, most telecommunications operators use Carrier Grade Network Address Translation which allows a single external address to be shared by many customers. This can get in the way of direct connection attempts from the outside world. Even if that’s not the case, most cellular operators tend to block inbound connections by default. However, there is a way around this quandary – using a VPN.
A Network That’s Private And Virtual
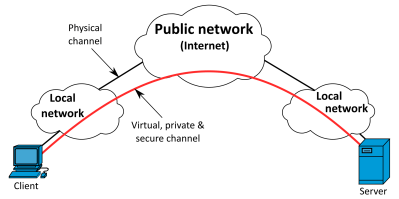
VPNs, or Virtual Private Networks, are exactly what they sound like. They’re a private network that exists between clients on a broader public network like the Internet. When it comes to making connections to remote hosts on cellular connections, they’re the perfect tool to get the job done. Having the remote host connect to a VPN server gets around the issue of rejected incoming connections, as all traffic goes through the VPN tunnel initiated by the remote host itself. Additionally, it means that other hosts connected to the VPN can talk to the remote host as if it’s another machine on a local network. With the correct setup, a VPN can be a highly secure and flexible way of talking to remote machines with a minimum of fuss and bluster.
You can run your own VPN server at home without much trouble. You’ll need a computer with reliable Internet access, that can accept incoming connections. Typically, this will involve enabling port forwarding on your home router so that connections made to your home IP on a particular port are forwarded to the computer running the VPN server software. Additionally, you’ll need to make sure your home internet connection isn’t behind carrier-grade NAT. Generally, if you’ve got cable, ADSL, or fiber, a simple phone call to your ISP is all that’s required. However, in some cases, you may find you have to upgrade to a higher tier connection package to get such treatment. There’s no need to have a static IP, either; dynamic DNS services can make it easy for your remote system to call back home. You can even run your own Dynamic DNS if you so desire.
So, assuming you’ve got a computer standing by, and a router with an open port to the wider internet, all you need to do is install the right software. OpenVPN is a popular choice for running a VPN server, and has all the functionality required with a bonus of being free. Historically, it’s required a significant amount of setup to install and generate all the required cryptographic certificates, however, with the release of OpenVPN Access Server, getting started is somewhat more streamlined.
Other options exist, however. PageKite is an opensource VPN solution that aims to make connecting remote systems a cinch. We’ve featured it before when discussing how to connect to Raspberry Pis from anywhere and everywhere. It’s available on a pay-what-you-want basis, with some data going through PageKite’s cloud servers to make everything that much easier to setup. Recommended pricing is just $3 USD a month, rising to $6 USD a month for more serious users. It’s a great way to get started if you just need to get your remote system talking online without a lot of unnecessary yak shaving. Another solution is WireGuard, an open-source VPN built upon concepts of ease-of-use, speed, and simplicity. With clients available for a broad base of popular operating systems, it’s easy to get up and running without a whole lot of fuss.
Once you’ve got your remote host connecting to a VPN, admin is easy. Simply enable SSH or your favored remote admin protocol, and log in as if the machine were on your local network. If your remote machine is properly configured to maintain the connection and reconnect on dropouts, you should have no issues controlling the machine no matter where it finds itself in the world – as long as it’s got a good cellular data connection. Just make sure that before you deploy it to a far flung locale, you have it to connect to the VPN on boot – else you’ll be out of luck the first time you need to command a restart.
If you’ve been following this series, you should now be confident to select the right hardware and software to control a computer remotely over the cellular network. Of course, with the roaming freedom of cellular network comes the difficulty that your remote system may end up somewhere far away and difficult to access. In the event something goes wrong, this can make solving the problem expensive and complicated. In future articles, we’ll explore ways to minimise these problems and how to best stop things from going sideways. Until then, happy hacking!
















I would also recommend looking at SDN. I use ZeroTier and no longer use a traditional VPN for remote access back to my home network.
Some networks provide M2M plans with VPN “baked in”. Remote devices with such plan (SIM) end up in a private subnet (192.168/x) without any additional configuration. Only an operator’s machine needs to be configured to dial into that subnet via a VPN terminated somewhere in the mobile network infrastructure. Ask your ISP/mobile network for m2m plans.
Ha, I just had a bunch of cellular VPN hosts go offline today because of a DNS issue. Don’t be like me and supply at least two sources of DNS :)
I have a number of Linux servers around and have my variable- or no-IP machines use ssh to create a reverse login setup on these servers so I can always access them remotely that way.
Easy setup and no (real) VPN needed.
@Lewin you forgot to mention softether ( https://www.softether.org ) which can use openvpn, l2tp via normal access or when networks are blocked can also work via ICMP or DNS. It also simplifies the openvpn config as it provides configuration and certification files.
Another great options is ZeroTier, already mentioned in the first comment.
Can personally recommend Slack’s Nebula here: https://github.com/slackhq/nebula – it’s not really a VPN, or a mesh network, but a secure overlay network that functions similarly to both. Previously used a Pi3 to run PiVPN, and before that stock OpenVPN, before that L2TP and PPTP. And IPsec. Oh my word, IPsec. I use a $5/mo Digital Ocean droplet to run some Docker containers and the public lighthouse fits fine there, but could easily be used on an SBC at home with dynamic DNS. Since it’s “just” simply an interface, NATing and routing work just fine, and complex networks can be built on top if necessary from standard open source tools, without the complex hassle of GRE+IPsec. I have some hosts in my home network meshed to my Digital Ocean and personal Amazon EC2 infrastructure. Very nice, portable, extremely easy, and gives my brain a break from enterprise-ready solutions that are financed by certification cartels.
Why are we still not pushing IPv6 instead of coming up with NAT after NAT to reuse IPv4 addresses? I’m sure the ISPs would have less trouble routing those packets than constantly swapping IP addresses around.
Because there are plenty of ISPs, like e.g. mine, who still haven’t bothered to so much as lift a finger in an effort to move from IPv4. Also, there’s plenty of software that does all sorts of stupid stuff and so only work right with IPv4, like e.g. neither Chrome, Edge or Firefox will connect link-local IPv6-addresses. That basically means that IoT- or LoT-devices will have to stick to IPv4, if they want to offer configurability via a web-browser.
I actually just dealt with this unexpected issue for a side project. Camera system on remote mobile hardware which needed to be able to be viewed remotely. Quick and dirty solution was a small $2/mo VPS running openVPN and an nginx reverse proxy to expose the camera system’s webUI and handle user authentication. Actually worked out quite well and has been rock solid so far.