We all know that our activity on the Internet is not that hard to track. It just annoys some people more than others. If you are really hardcore, you’ll learn all the ins and outs of networking to help cover your tracks, but what if you don’t want to invest that kind of time? Maybe, as [TechRepublic] suggests, try Kodachi Linux.
You could, of course, start with your own live image. Then when you boot, you could take the following steps:
- Randomize your MAC Address
- Establish a TOR connection through a VPN
- Route all internet traffic through TOR and use DNS encryption
- Set up a scheduled task to scramble your MAC address periodically
But that’s what Kodachi does without any real effort on your part.
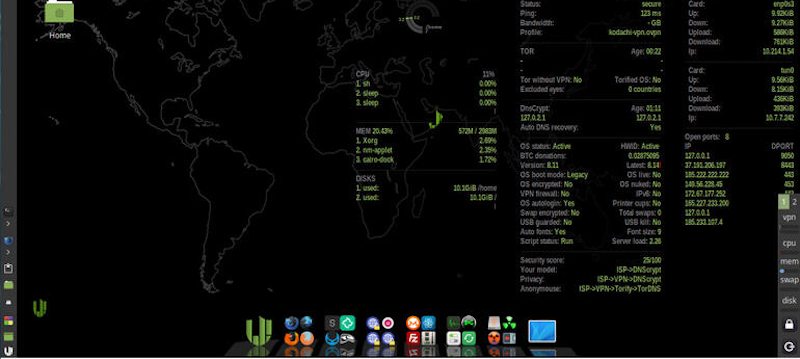
The distribution is based on Ubuntu, so all the familiar tools are there. There are also a few security and privacy tools included like KeePass, Tox, OnionShare, i2p, and more. The desktop shows a summary of secure network information
Do you need Kodachi? Probably not, if you are a Linux guru. Plus, most people aren’t doing anything that’s that interesting. But if you want to protect your privacy or you are up to something, give Kodachi a try. Then again, if you are that paranoid, maybe that’s just what THEY want you to do. Make your own decisions. You can also check out the video review from [eBuzz Central] below.
Looking for more conventional Linux? Why not Rocky Linux? If you just want a VPN, you can always just use ssh.















It’s amazing people thing randomising your mac address can help with much. About the only thing it’s good for is obfuscating your hardware on a local network (public wifi maybe). Stands out like dogs balls in the network traffic though.
It’s a waste of time.
@Look At Your Network Traffic FFS said: “It’s amazing people thing [sic] randomising your mac address can help with much. About the only thing it’s good for is obfuscating your hardware on a local network (public wifi maybe). Stands out like dogs balls in the network traffic though. It’s a waste of time.”
If you do NOT want your device to be tracked on public/enterprise WiFi, randomize the MAC address. Everyone does it now…
MAC Address Randomization in WiFi: To prevent third parties from using MAC addresses to track devices, Android, Linux, iOS, and Windows have implemented MAC address randomization. In June 2014, Apple announced that future versions of iOS would randomize MAC addresses for all WiFi connections. The Linux kernel has supported MAC address randomization during network scans since March 2015, but drivers need to be updated to use this feature. Windows has supported it since the release of Windows 10 in July 2015.[1] To mitigate “Stands out like dogs balls in the network traffic though.”, the address randomization randomly refreshes. Also, you really don’t stand out in a crowd where everyone else is also using MAC randomization, which is the case today.
But there can be issues with MAC randomization…
Security Issues with MAC Randomization: There are several levels of security risks that come from randomizing MAC addresses, primarily network destabilization and malicious device activity. Both Wi-Fi steering and traffic offloading from cellular nets rely on detecting, identifying, and classifying devices to provide stable connections for tens of millions of users every second. Whenever a 4k streaming device connects to a network, it needs more broadband allocation than a smart fridge. If the network cannot identify the device, it cannot steer it to the best SSID and router band. Since MAC addresses are used for tracking devices on a network, operators and users will no longer be able to monitor devices connected to their routers when any significant number of devices use unpredictable addresses. What happens when you cannot monitor and detect a device? It becomes easier for malicious actors to hop onto your network with their own MAC address and hide. Lastly, device-based parental controls and malicious content blockers often use MAC address blacklists and whitelists. Whenever a device randomizes its MAC address, these protective measures need to be set up anew. Unfortunately, doing this daily is not a good option for security and makes those solutions obsolete.[2]
* References:
1. MAC Address Randomization in WiFi
https://en.wikipedia.org/wiki/MAC_spoofing#MAC_Address_Randomization_in_WiFi
2. MAC Address Randomization: Privacy at the Cost of Security and Convenience
https://cujo.com/mac-address-randomization/
Given that someone who really wants to spoof or otherwise change their device’s MAC address can do so, security should not be based on MAC addresses. Where I work, devices have software installed that authenticates the devices to the network. When a device joins the company network, both the device’s credentials and its user’s credentials are authenticated. Only then is the device allowed to use the network. This authentication is not base on MAC address and does utilize zero knowledge proof. Any device that fails authentication is reported, including it’s location, to the IT security team for investigation. Any potentially malicious device/actor is detected, monitored and dealt with – quickly.
As for WiFi steering, any specialized device is unlikely to be using MAC randomization. And most of the time, a device using randomization isn’t going to be inadvertently “spoofing” a specialized device. Furthermore, it would be entirely reasonable that authorized, specialized devices be pre-configured to join a suitable network. This is how my employer’s IT group handles specialized devices. Yes, it is more work when setting up devices, but it avoids the problems that come with reliance on MAC based solutions, such as MAC spoofing.
Yes, MAC randomizing makes certain techniques obsolete and ineffective, but so does MAC spoofing.
Also, security has many aspects, including robustness, authentication, authorization, privacy, and more. Sometimes there is conflict between these aspects.
Overall, I see the advantages of MAC randomizing as outweighing the disadvantages.
(FYI, for my home network, I configured my router to use RADIUS authentication. While not as sophisticated as my employer’s network, it does work and it doesn’t rely on MAC addresses.)
It’s probably worth reading this before you start using Kodachi for anything privacy-related… https://bitsex.net/english/2021/kodachi-linux-is-probably-not-secure/
But… if I’m paranoid, why would I trust someone else’s distro to be doing this correctly and not have a back door reporting to The Man?
And if they are extra paranoid they would be pulling their own crystals!
e.g.
https://spectrum.ieee.org/the-secondhand-origins-of-silicon-valleys-ingot-industry has a link to a oral history interview of Patricia Anderson who worked as a crystal puller operator with silicon tetrachloride/gallium arsenide in the 1960’s growing pure single silicon crystals or pure gallium arsenide single crystals or single silicon crystals dopped with phosphorus or boron
https://www.computerhistory.org/collections/catalog/102740547
Although you should be able to trust blank wafers that were bought as long as you masked, etched and doped them yourself. Where would trust start for the truly paranoid ?
Quite a few people literally agree with you…….
What is this strange “trust start” thing?
anybody who thinks they are paranoid but doesn’t think that all so-called secrecy devices and encryption techniques are created by ‘them’ to spy on you isn’t nearly paranoid enough and needs to up their game.
The AES cypher wasn’t “created by ‘them’ to spy on you”, it was made by a couple of Belgian cryptographers. If you look at the actual algorithm, you’ll see there aren’t any mysterious constant values. I know this because I have personally implemented AES and it’s deceptively simple in it’s design.
The Wikipedia article on it is quite good: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
But you can always look at the official standard which is FIPS 197.
but that’s what ‘they’ want you to think.
Time to face facts, Big Crypto controls the world government.
“When the world is out to get you, being paranoid is just common sense”
— Johnny Fever, WKRP
right! you should build your own distro. But… how can you trust software wrote by others? you must read and verify line-by-line all source code. But..how can you trust hardware? you must do yor own soc as libre-soc.org.
Unless you actually tape out a chip by hand, you have to verify the chip creation software.
You must be pulling my ingot here…
@Dan said: “But… if I’m paranoid, why would I trust someone else’s distro to be doing this correctly and not have a back door reporting to The Man?”
TNO = Trust No One
Josh Duggar needed this…
We are lucky that those with such predilections are randomly distributed as most people are idiots.
Been using Qubes OS for the past few years but find customization (as in beautifying) problematic. Kodachi offers some interesting features and looks pretty but doesn’t offer the compartmentalization and isolation Qubes provides. Also, the value of Tor with a VPN is debatable.
Just taking a quick look, I’d say Kodachi looks to be ‘paranoid’ about securing you from networked threats, while Qubes is more about securing you from local ones. Qubes also is doing a lot more plumbing to make that happen, which does get in the way of ‘normal’ desktop things, but I still keep an eye on it because it’s such an interesting project.
“Plus, most people aren’t doing anything that’s that interesting”
If this was not interesting nobody would spy.
“Saying you don’t care about privacy because you have nothing to hide is like saying you don’t care about free speech because you have nothing to say.” — Edward Snowden
+1
Isn’t TOR just a three-letter agency honeypot?
No, you should really read up on the history of TOR because the purpose was/is to help agents in hostile lands. That said, if you think it will keep you safe then you’re fooling yourself.
Most of the high-profile people caught when using TOR were caught because of metadata analysis or sloppiness / misconfiguration rather than a weakness in TOR itself. Or so *they* tell us.
Based on Ubuntu, so amazon is preinstalled.
Only if they use Ubuntu from before 20.04.
Based on Ubuntu, so easily ported to Debian or another Debian derivative.
If it was based on Devuan, I’d give it a spin. But when I see things like “2- I tried to move to Ubuntu 20.04 but Python deprecation was a hassle for me to continue so I continued with 18.04.6 for now bare in mind that 18.04 support is still valid for Ubuntu and it should reach end of life by April 2023.” that would lower my interest in trying “Linux Kodachi”.
I’m paranoid (not mentally, just governmentally B^) ).
So, thanks for the article Al, it is something I should be looking into using more.
(…) Enter your info do not change the user name! keep it as kodachi then hit enter stay back and watch.
https://www.digi77.com/linux-kodachi/#Installation
I wonder why you should leave the username preset. Is then not immediately apparent to any attacker which system I use?
Probably the same reason why you should not resize the window of your TOR browser. It is something which makes your system different from (and thus more unique than) all the others.
That is probably the stupidest part about tor… just how hard do you really think disabling those metrics from feeding back to a site is, as well as other metrics that absolutely aren’t neccessary for the servers to have, as they can be worked out client side?! …
Sounds nigh impossible to me, as long as the browser is based on Firefox :(
This is exactly the example I was thinking of.
>> “Most people aren’t doing anything that interesting”
I’ll bet your facebook and amazon ads are uncannily accurate. Also your weather forecast for today is a high of 71 degrees and sunny.
Remember: “nothing to hide, nothing to fear!” nobody will ever use your data for anything nefarious ever. The only people gathering and storing your data is your own government, and they have a fantastic track record of protecting their databanks.
You can’t use the internet in a completely private and secure manner without breaking the law, in fact I can’t even tell you how to do it without breaking the law (in my country). The inconvenient takeaway from that is that if you are not breaking the law then you are not doing it well enough, so why bother? Perhaps if you just want a modicum of privacy from commercial entities…
TAILS anyone? https://tails.boum.org/about/index.en.html
I looked up the Japanese word “Kodachi” and it appears to mean a short sword (smaller than a Katana).
That being said, I wonder if it would be the perfect operating system to use on a . . . . . . . . BLADE server !
If you’re here and reading this (years later) and you’re new to weird linux Distros — check out the distrowatch site. There you will find some very well founded arguments for why this distro is suspect as hell and not what you want to be using as a wingnut.