Mobile PINs are a lot like passwords in that there are a number of very common ones, and [Mobile Hacker] has a clever proof of concept that uses a tiny microcontroller development board to emulate a keyboard to test the 20 most common unlock PINs on an Android device.
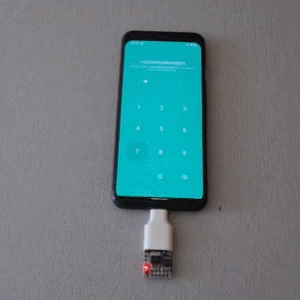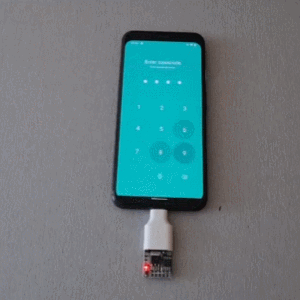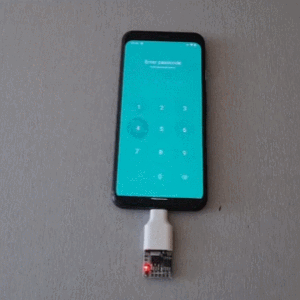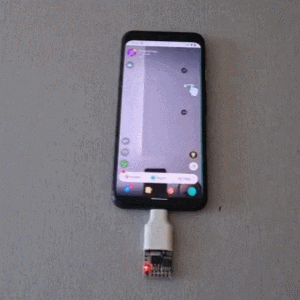
The project is based on research analyzing the security of 4- and 6-digit smartphone PINs which found some striking similarities between user-chosen unlock codes. While the research is a few years old, user behavior in terms of PIN choice has probably not changed much.
The hardware is not much more than a Digispark board, a small ATtiny85-based board with built-in USB connector, and an adapter. In fact, it has a lot in common with the DIY Rubber Ducky except for being focused on doing a single job.
Once connected to a mobile device, it performs a form of keystroke injection attack, automatically sending keyboard events to input the most common PINs with a delay between each attempt. Assuming the device accepts, trying all twenty codes takes about six minutes.
Disabling OTG connections for a device is one way to prevent this kind of attack, and not configuring a common PIN like ‘1111’ or ‘1234’ is even better. You can see the brute forcing in action in the video, embedded below.
Bruteforcing PIN protection of popular app using $3 ATTINY85 #Arduino
Testing all possible PIN combinations (10,000) would take less than 1,5 hours without getting account locked. It is possible coz, PIN is limited only to 4 digits, without biometrics authentication#rubberducky pic.twitter.com/rbu9Tk3S9d
— Mobile Hacker (@androidmalware2) July 12, 2023
















What if my PIN is 2137? It’s a holy (papal) numer but not very common unless youre Polish.
If the person trying to get into the phone knows you’re Polish (or sees “Wpisz swój PIN” or similar on your lock screen) and knows this information, 2137 will probably be amongst their attempts.
papierzowa godzina zawsze na propsie :)
napisz “miszczu” jeszcze papieszowa…
The article states that testing all 10,000 pins for a 4-digit pin would take less than 1.5 hours.
I’ve posted this before, it’s worth reading, and the 100×100 plot of PIN frequency is interesting: http://www.datagenetics.com/blog/september32012/
Thank you for the link! This was very informative and detailed.
Another good reason to have a custom bootloader with filesystem access, you can reset this stuff using the file browser in TWRP for example. My tablet has a glitch where the unlock pattern will not work, its too laggy to complete successfully before the screen times out (IIRC). But in TWRP I can go and delete the store and it will start up no password.
This is great in conjunction with another hack to allow unlimited attempts and you can leave it cracking. Another tip would be to see if there are any smudges on the screen on the number spots, then you can concentrate on those digits only.
You are correct about being able to delete the file in which the pin is saved in the /data partition, in older devices, that is. But you must know where that file is on your specific file system, and that changes. Also, it can be available in TWRP and OrangeFox by script, but doesn’t work on all devices.
*Also, it’s a custom recovery – not bootloader. You can’t change the bootloader on your device. Some, such as Samsung, update the BL version with FW updates, but you can’t change your bootloader, only unlock it to flash a custom recovery. Recovery is what the “R” in TWRP stands for – “Team Win Recovery Project”.
Not tryna be a jerk, but people may read your comment and spend lots of time researching how to get a “custom bootloader” for nothing because you’re using the incorrect terms. Maybe, advance beyond noob status before tryna flex on hacking sites, smh
Agree!
That last comment was supposed to be in the main area. Also when dealing with people of a certain age: any date from 1940-1970 etc is likely to be a pin. You might not be surprised how many people have a year and ‘harley’ or a pet’s name as their password. See also combination locks with 4 wheels
Our school IT contractor Fred was terrible. Nothing ever worked right and he wouldn’t do basic things like change the default resolution from 640×480 on teacher’s computers even after they complained and requested him to change it. (And admin locked users from changing resolution). Fred’s password was also Fred7.
Truly a security mastermind.
Good read, and 1234/12345 is a great rebuttal to the logic fallacy ” n million people can’t be wrong”
12345… That’s the same combination on my luggage!
Love the Spaceballs reference!
This is a fascinating analysis. Thanks for posting the link!
Cool, so from your link I learned I should set my pin to 8068.
[Chuckle!]
Not sure how they can test 10,000 combos. Most phones these days will lock after a certain amount of incorrect pin attempts
This is true as far back as 2016:
https://www.techrepublic.com/article/pro-tip-how-to-reset-your-android-lock-screen-passwordpinpattern/#:~:text=You%20have%2010%20tries%20to,through%20the%20Android%20Device%20Manager.
He was probably unaware that “test” has special meaning. He should have said “tried” or “typed” or something instead. From context it seems certain he used those terms interchangeably.
It is trivial to “type” 10,000 combos and do so in the time specified.
It would be difficult to test more than the first few due to mitigations like the lockout you mention.
This is probably a hoax. The animated GIF above shows only 8 or 9 tries before being successful and the phone shown in the video on [Mobile Hacker]’s Instagram seems to run an ancient Android, it displays “Try again in 30 seconds”. I wonder how many tears were shed after trying to unlock daddy’s phone this way.
Yes, and it’s a set-up. It unlocks after the last pin of “1234” is used. Truly a great real life use case tool.
Yeah this kind of thing is as dumb as most hacker movie shticks. You have not been able to brute a keypad like this nearly anywhere since idunno.. the 1980s? I’m looking forward to the guy who inevitably comes in with an example of something that is still built this way though lol
Another possible fix is to ignore USB devices connected when the screen is locked. Moreover, it’s done that way in GrapheneOS [tested on pixel 4a 5g] and can be enabled by that user in DivestOS (settings → search → restrict USB → allow USB connections when unlocked) [tested on one plus 5]. Also, the pin there is not limited to 4 or 6 digits.
Android has done this for a number of versions now.
I can’t access the internal storage etc via USB until I unlock the phone.
Does anyone know if this would work on a Sony Xperia 10? That phone is a weird beast.
:shrug Depends on whether the devs have considered such an attack.
All I can say – it certainly does not work on GrapheneOS, possibly – on Calyx and can be metigated on DivestOS (settings → search → restrict USB → allow USB connections when unlocked). Also, the pin there is not limited to 4 or 6 digits.
If you read the comments you would see any phone newer than 2016 will lock after 10 incorrect pins and require a complete factory reset.
So if it newer than 2016?
Some Android OS variants does not let external devices unlock the lock screen. Last CM for example I have on a phone (Im not using anymore) does not react to any mouse events on the lockscreen, I have to drag up it using the touchscreen first.
I made a script to try different last 2 digits (of the 4 digit pin) over ADB for my phone because I forgot the complete pin. It took a single night to unlock the phone. It was in 2014. Back then the timeout lasted for 30s no matter how many wrong passwords you inputted
Ehhh, doesn’t a phone (or pretty much anything with a pin code) lock after 3 failed pin codes?
Maybe — but my phone is programmed to wipe after 15 failed attempts is a row (company security requirement).
Well if your password is “1234” you deserve to have your phone broken in to.
It’s what’s on my luggage.
Nope – 0000 for luggage :-)
Does it matter?
With ubiquitous TSA keys 🔑 available online.
I know, by the way your Sponge Bob underwear is super comfy.
B^)
Wait, since when were phones limited to four digits? My last few have all allowed at least eight?
Uh… pretty much every phone nowadays automatically starts doubling the wait time between failed PIN attempts after the first few incorrect PINs, so very quickly you end up having to wait several minutes to an hour or more between each new attempt, making this attack almost impossible unless you guess the correct pin within a handful of tries. A lot of phones even have an option to wipe the device if X number of incorrect PINs are tried.
He’s not brute forcing the “mobile’s pin”, he’s brute forcing the pin number for an app installed ON the mobile phone! That’s a very important part of the equation, and a the article should be updated to reflect such. Unless you intended for the article to be clickbait, which is how it stands right now.
You can miss PIN only 3x, phone code only 10x but not that fast. After every miss you need more time to try again.
This in video is impossible even on old phones.
If he is lucky he can get it in first 9x but i doubt about it.
Very interesting comment from “Miles” , I will try this trick soon on different devices to see which ones it can work on. TNX!
By the way I had already written a similar thing with a Teensy, some years ago, when I was just starting with programming.
https://github.com/JonnyBanana/Teensy-Android-Pin-BruteForcer
It does exactly the same thing , however then tries all the years from 1900 and up (this is because I have noticed in my decades of experience as a technician, that many users use their year of birth, or of close relatives, as already pointed out the users who use pins are often from older generations) , and then if the two combinations do not work try a brute force 0000-9999 , but as already pointed out these techniques hardly work with Android’s time lock…
Seems like something xkcd should have fun with
1234
1111
0000
1212
7777
1004 <— ?
2000
4444
2222
6969
9999
3333
5555
6666
1122
1313
8888
4321
2001
1010
Wait…your phone limits you to 4 character pin? Sounds like an Apple problem…..I can make my pin much longer, and did.
There must exist cell phone theft rings. So assume you jack 10 or even 100 phones. My p-stat is a little rusty but the chances of you cracking at least a couple after a few tries is probably wayyyy higher than you’d expect. Even with lock outs and stuff and so what if you brick the rest trying.
This may be the only thing I can think of as a positive for forced obsolesce when your phone batter craps out after 3 years – new phone new security (finger prints etc)
What is crazy is that you can input 10,000 incorrect patterns in 1.5 hours and NOT get locked out. Brute attacks should be prevented easily.
Misleading article titles. It’s not mobiles pin it’s app pin
I have always used an 8 digit PIN for as long as I can remember.
Hello where can I buy this butyfull ATTINY85?
https://github.com/androidmalware/DigisparkAttiny85-scripts.git