As we first reported in yesterday’s weekly security post, researchers at EURECOM have revealed the details (PDF, references) of a new man-in-the-middle (MITM) attack on Bluetooth 4.2 through 5.4, which has been assigned CVE-2023-24023. Like preceding CVEs, it concerns the session authentication between Bluetooth devices, where the attacker uses spoofed paired or bonded devices to force the use of a much shorter encryption key length.
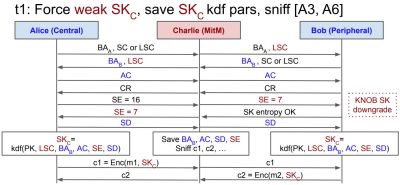 The name of this newly discovered vulnerability is BLUFFS (Bluetooth Forward and Future Secrecy), where forward and future secrecy are important terms that refer to the protection of secure sessions against compromise in the past (forward, FoS) and future (FuS). The CVE presentation notes that the Bluetooth specification does not cover either FuS or FoS. In total two new architectural vulnerabilities were discovered, both of which attack the security key.
The name of this newly discovered vulnerability is BLUFFS (Bluetooth Forward and Future Secrecy), where forward and future secrecy are important terms that refer to the protection of secure sessions against compromise in the past (forward, FoS) and future (FuS). The CVE presentation notes that the Bluetooth specification does not cover either FuS or FoS. In total two new architectural vulnerabilities were discovered, both of which attack the security key.
The Bluetooth SIG has released a statement regarding this attack method. Although serious, it would seem that the core issue is that some implementations allow for encryption key lengths below 7 octets:
Although the researchers note potential fixes and mitigations, these would need to be implemented in every affected Bluetooth controller out there — this might be a good time to re-examine in how far one relies on Bluetooth security, and what the effect of a hijacked session might be.
















I ponder how many medical implants have this vulnerability and no way to update the BT stack.
Yeah, as a T1D managing my diabetes with AAPS, I feel a bit anxious… In case someone hacks my insulinpump and introduces my pump to give me bunch of insulin during sleep could very easily kill me
Back when I did wireless communication development I always thought Bluetooth was a garbage protocol. I changed my mind a little when I found out I could impose my music tastes on the unsuspecting.
How you do that?
So, how often do you find BT devices that would be hacked? I mean you must be near enough to use this exploit AND it has to be something that you gain something from to intercept, while we are still talking about a BT device.
I suppose the CIA could use it to hack microphones (earbuds) at some conferences, although that woiuld only be needed in instances where there were no phones they alrewady hacked in the vincinity. So not a US agency then but some more obscure one. And it would need to be a conference where they allow such devices, so uhm, maybe a UN one?
There are enough BT devices out there for so many purposes – it doesn’t just have to be the big espionage listening in to audio type concerns. More than a few vehicles have BT tied into the CAN bus, keyboards, mice, headsets, medical devices, e-sim full fledged smartphone ‘watches’ that still expect to obey the main phone, etc.
Also worth pointing out this sort of attack can potentially lead to full system access via other flaws or just because you have in effect local access – spoof that BT keyboard and you can do almost anything as if you were the local user, which is terrifying. Even more so in the case of Windows installs most likely with passwordless root access – as that so trivialises simply telling the users system to please download and run our malware.
You want security wireless anything is probably a bad idea, but as BT does seem to tend towards the worst wireless security of the bunch… Also the range of a wireless signal is a bit more nebulous than that – just because a pair of device with an ‘omni’ antenna so you don’t have to point them at each other is good out to 10 meters doesn’t mean you can’t interact with those same BT over vastly longer distances in a way the devices won’t know any better with a more focused antenna (go far enough and the latency may get noticed but at speed of light the difference between 10 meters and 100 in time of flight is going to be tiny enough it probably won’t be noticed…
I think people would notice if somebody was using your keyboard/mouse, they would need to do it when you were AFK and not have things powered down.
And this talk of medical devices, it seems oddd that there would be BT ones but even if so it would just read data, you aren’t going to convince me that there are medical BT devices that do something active, I wouldn’t believe it if you showed me.
Thank you though for the list, some of those are quite valid.
Oh and that long range antenna would need to be directional for 2 way communication, and that directionality is hard with devices that move around a lot I expect, so that mitigates it a bit.
Meanwhile the hacked WPA2 version of WiFi encryption is still widely used too.
>people would notice if somebody was using your keyboard/mouse..
Not hard with how sloppy most folks are at locking their system when they step away to play with their system and have them AFK so they can’t possibly notice. And if its the coffee shop type situation where you can actively see them you are just waiting for the handful of seconds a script will take to be sent and run on modern hardware – they only need to be distracted a moment. And you can see that, even make it happen if you are specifically targeting them…
I have never seen in person but heard of some medical devices that are supposed to dose the patient automatically and are BT controlled/monitored. I don’t think I’ve heard of any set up that way for medical conditions that are really quickly lethal if it goes a bit wrong however (but I’m really not a medical expert at all – a field I am most certainly deeper into the “know just enough to be dangerous” than most).
>Oh and that long range antenna would need to be directional for 2 way communication, and that directionality is hard with devices that move around a lot I expect…
Indeed, the long range if you are really pushing for huge “sit on a mountain on the horizon” silly levels of long range will need some very good active tracking and a bonkers antenna for such low power signals. But far enough away they won’t notice you shouldn’t be that bad as the antenna don’t need to be that directional. And in many cases these devices are not very mobile – they will stay within the sweetspot even though they are wiggling around a bit.
As for that list I highly doubt its exhaustive or even close to all the potentially dangerous ones, as BT gets everywhere. Just the stuff that jumped into my head.
I have type 1 diabetes and my continuous glucose monitor, Dexcom G6 uses Bluetooth to connect to my phone and my Tandem Tslim X2 insulin pump. More scary is I can remotely deliver 25u of insulin from my iPhone to my pump over Bluetooth(Enough to cover six 12oz cans of Mountain Dew). This is technically a big deal for some people but I appreciate your skepticism.
I’ve experienced this attack, have Bluetooth turned off, so it appears. The keyboard is virtual, and appears to be used by remote access. I have no “known” or intentional BT devices, but you would be surprised how many devices use it, including the key fob on your car, a smart light bulb, IoT devices, along with Wi-Fi. Buy a Wi-Fi Bluetooth scanner, for about $65 starting price. It only needs to access one internal device, then moves laterally inside your network. I’d say the medical devices could be targeted if running Wi-Fi or BT.
Just live in an apartment. Listening to a neighbor play rap over their BT speaker over all hours of the night will provide all the motivation/gain you are looking for.
A jammer on the right frequency seems like the easiest way to intervene (5 dollar wrench xkcd). People worry about complex attacks while there have been much easier ways to accomplish the same goal.
A mitigation has been out in newer android and iOS devices for quite some time. Samsung had it fixed like 3 years ago in their phones by requiring a higher minimum key size.
And while you might be able to hijack a session, it is neither reliable or easy. It does not give you direct access to your data on the device so only thing you would have access to via the bluetooth connection.
So who should be worried? People with crappy health devices that do not use other security means (like application layer signatures and validation).
Yes you are correct in the jamming issue. I use a 2.4 – 2.5 sweep generator and a 1 to 10 watt amplifier. Shut down the whole spectrum.