The Rigol DHO800 and DHO900 series use Android underneath, and as you might expect, this makes them easier to hack. A case in point: [VoltLog] demonstrates that you can add WiFi to the scope using a cheap USB WiFi adapter. This might seem like a no-brainer on the surface, but because the software doesn’t know about WiFi, there are a few minor hoops to jump through.
The first issue is that you need a WiFi adapter the built-in OS already knows how to handle. The community has identified at least one RTL chipset that works and it happens to be in the TP-Link TL-WN725N. These are old 2.4 GHz only units, so they are widely available for $10 or less.
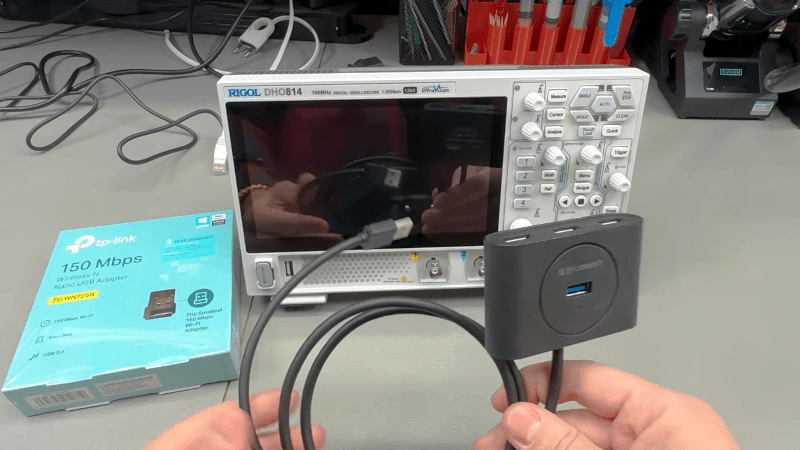
 But even with the correct hardware, the scope doesn’t have any menus to configure the WiFi interface. To solve that, you need to temporarily use a USB hub and a USB keyboard. Once you have everything plugged in, you can use the Super + N keyboard shortcut to open up the Android notification bar, which is normally hidden. Once you’ve setup the network connection, you won’t need the keyboard anymore.
But even with the correct hardware, the scope doesn’t have any menus to configure the WiFi interface. To solve that, you need to temporarily use a USB hub and a USB keyboard. Once you have everything plugged in, you can use the Super + N keyboard shortcut to open up the Android notification bar, which is normally hidden. Once you’ve setup the network connection, you won’t need the keyboard anymore.
Or maybe not — it turns out the keyboard does allow you to change a few other things. For example, [VoltLog] used it to increase the screen brightness more than the default maximum setting.
The only other issue appears to be that the scope shows it is disconnected even when connected to WiFi. That doesn’t seem to impact operation, though. Of course, you could use a WiFi to Ethernet bridge or even an old router, but now you have a cable, a box, and another power cord to deal with. This solution is neat and clean. You bet we’ve already ordered a TP-Link adapter!
WiFi scopes are nothing new. We suspect Rigol didn’t want to worry about interference and regulatory acceptance, but who knows? Besides, it is fun to add WiFi to wired devices.















Nifty little hack, albeit I’m not sure what this could be used for, at least without making other modifications to the onboard installation.
Also could anyone explain why would the manufacturer use Android over a simpler Linux installation?
Android is just Linux with a window manager and widget library.
Yes and no. Yes the kernel is Linux, but everything above that is a bit different. For example bionic vs glibc, surfaceflinger vs X or Wayland. You can’t just run your normal Linux binaries without recompiling them or using a chroot.
Yes, yes, and yes. And then:
4. draw the rest of the entire owl :)
The manufactures provide only android sdks for a lot of chips. So their choice processor could be it.
What is the advantage of adding WiFi? Seems cool though :)
If you have your scope networked, you can easily control it from a browser (or custom software), take screen shots, and even screen movies. So having it networked is a big plus. The wireless just keeps you from having to drag a wire around or, in the case of an adapter, a wire, a box, and another power cord.
With that limitation of having to find an adapter that is supported by the underlying OS, which probably isn’t going to get any updates… Eventually one will have to resort to the wifi to ethernet bridge.
I mean, already TFA says they were limited to the old 2.4G frequencies. Just wait till all the encryption it supports becomes too easy to hack. This is a good example of why I still love ethernet even these days when everything is wireless.
One of those little cheap yellow router pucks they sell on Amazon for peanuts which run OpenWRT ought to be more than capable. Then when that becomes obsolete it’s another $5 to replace it.
Devices such as these are typically in service many years past the final software update from the manufacturer. In addition, some of them are produced in hostile authoritarian countries where every business is under some degree of party control. Some of these countries engage in industrial espionage, for which there is probably no better trojan horse than an oscilloscope. If you are concerned about security, it is undesirable to have such devices on a wireless network, or even a shared wired network. The safest approach is one of zero trust, where they are on their own VLAN on a hardwired network with appropriate ACLS and firewall rules, or proxied behind a bastion host.