Ah, generic unbranded IP cameras. Safe, secure? Probably not. [Alex] has been hacking around with one of his very own, and he’s recently busted the thing wide open.
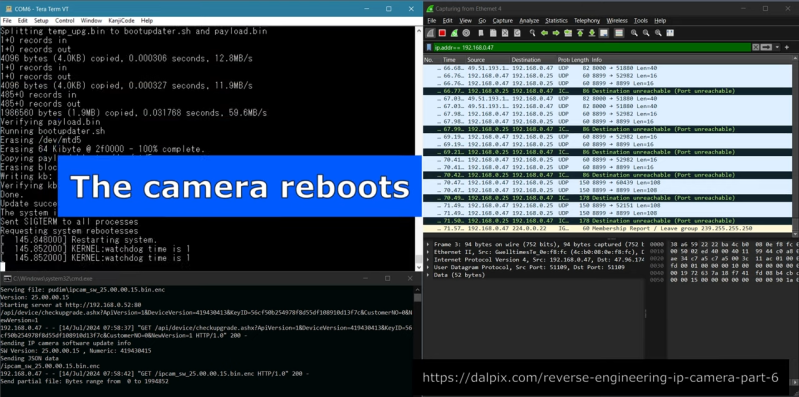
Determining that the camera had a software update function built in, [Alex] saw an opening for hijinks. The first issue was that the camera only accepts encrypted update packages, which complicates things somewhat. However, through some smart reverse engineering, the format of the updates and their encryption method became obvious to [Alex]. Oh, and partly because there was a GitHub repository online featuring the source code used by the manufacturer to encrypt their updates. That definitely helped. It also led [Alex] to suspect the manufacturer may not have properly respected the open source license of some of the routines involved.
In the demo of the exploit, [Alex] has the camera reach out to www.pudim.com.br instead of the servers of the original manufacturer. That’s a pretty clear way to show that the camera has been owned.
We first featured [Alex]’s work in this space all the way back in 2019. It’s come a long way since then!















been there done that 20 years ago with the original netgear IP camera.
Those original Netgear (or maybe they were doing) circular cameras were pretty easy
The way random IP cameras can be considered safe is when compared to devices that aren’t used the way you can/should use an IP camera. With cameras that can provide video directly without bouncing off a cloud server first, you can just set your network to only allow video to pass and only to limited viewers. It’s the older and easier option; sucks that we can’t seem to just stick with that for home grade equipment.
If it’s connected to a network, regardless of protections, if you breach that network, you can access it. Doesn’t matter what the camera itself is doing.
That’s true, but it’s a bit like warning about an exploit that requires hardware access. If the attacker is already inside, you’re screwed no matter what. What spaceminions describes is a setup that likely won’t cause security problems for the average person, but when every camera talks to the same web server, it’s much more vulnerable. There’s always a sliding scale between security and utility.
Eh, I mean, you can’t just connect to any part of a network and instantly own everything on site. Say your camera is powered by POE from a switch that’s configured where anything on that port goes straight to the firewall and nowhere else. And the firewall is configured that the exact device of the camera, when it comes from that port through that switch, is only reachable by your NVR which is also a known device on another port, and even then only for the video traffic rather than just anything. Doesn’t matter what the camera does, if you are connected to some other part of the network and haven’t defeated the firewall, you don’t automatically win everything.
If you have a viewer machine that’s allowed to view from unsecured areas without having done anything to prove who it is other than maybe knowing the correct mac address, i guess that’s obviously a problem at least for whatever traffic they can make the firewall think is legitimate viewing, though still not random crap. But in that case, you just require someone to hop on secure wifi if they’re in the physically unsecured area and want access to something. Or even go one further and say they need to hop on VPN and/or do something more proper, but wifi is the easiest way to kick some kind of barrier in place compared to just trusting anyone who plugs into an open jack on the wall in the front room.
Yes. In a perfect world. But probably 90%+ of ip cameras or it (shudder) stuff in general is in default and easiest route to connect it up.
Firewalls vpns, port lock downs vlans, yeah…. they don’t pay enough for more than a picture on the screen.
Oh and the easiest way into the network is often to disconnect rhe ethernet jack on the ip camera. It helps than many vendors put the mac model and serial on the label too.
What are you trying to say? The cameras aren’t insecure unless everything’s insecure due to negligence, in which case anything you do is going to be bad and they are no worse than anything else. Especially if you’re lazy and illiterate while your criminals are highly motivated and tech savvy.
And even then, you can still securely make use of an IP camera while being as lazy as possible – just hook the camera up to a recording box, but don’t hook the recording box up to anything. Then retrieve the video from the box manually if you ever need it. That’s more secure than a “smart” device that needs 24/7 internet access to work, and that’s why this article’s kind of IP camera is no good but the dumb kind is no big deal, hardly worse than CCTV.
Does anyone know if a cheap brand of security Equipmenti like cameras or DVRs/NVRs that give the user access to the device? Almost all of them seem to run Linux, anyhow. I don’t know why they lock us out and deny us hackability
> I don’t know why they lock us out and deny us hackability
Because for one that would cause a massive strain on the supportdesk for each idiot trying, and then bricking, their device and then coming for support or, worst, claiming warranty.
If you want 100% access then you can build your own camera for less than $50 easily, $100 if you want to go 4K and fancy schmancy.
I’ve been using these as security cameras…
https://hackaday.com/2022/04/11/review-vizy-linux-powered-ai-camera/
Pretty easy to set up to stream to Frigate/HomeAssistant, and I have a cron script on the raspi which switches the IR filter off and turns on IR LEDS at night. The main reason I got it was for the nice outdoor enclosure available and power-over-ethernet compatibility.
Otherwise anything that sends a local H.265 stream is good for integration. Axon cameras are nice (but not cheap), I think most people use Hikvision for best bang/buck. Frigate software is great, good integration with machine-learning object recognition and easy to set up.
Also, don’t forget webcams on standard linux machines… Can stream those too with a bit of configuration.
MediaMTX is the best option I’ve found for that
https://github.com/bluenviron/mediamtx
Set up an RTSP stream back to Frigate server.
A lot of those chinese IP camera and DVR are offering some kind of P2P protocol to allow easy remote connection from anywhere, without any need to setup NAT or VPN. Examples are VVSeeP2P, VVEye, ThroughTek Tutk Kalay, And most of the time these are protocols developped by chinese based companies, and continously phone home to China based servers, so reliability can really be questionned.
I do have a “BASCOM” branded system (recorder and cameras), but they really are manufatured by Zhuhai Raysharp Technology Co. Ltd. in China. Despite repeatdly asking them for firmware updates, absolutely none have been provided since 2018/2020 (depending of equipments)!
And i’m pretty sure it has been hacked, since the DVR regularly resets my own account name and passwords to factory ones, reactivates P2P connection (i connect to it with a VPN so turned off P2P), and all logs are deactivated! So i will have to replace it ASAP… These are really a piece of crap!
Easy way to secure random IP cameras: keep them on their own isolated subnet, don’t even allow them a peek at the internet or even at the rest of your local network: said dodgy IP cameras can see only the DVR that is ingesting their image streams. You own the DVR, and you can either keep it local too, or expose it for remote access only via your VPN of choice (or… blech… via some cloud service).
Doesn’t matter if your IP camera has a network backdoor, if accessing the network to talk to that backdoor requires the attacker to physically access the interior of your location to connect to said network – at that point the security cameras are pretty moot.
This post provides some intriguing insights into the potential of IP cameras and the flexibility of running custom software. However, it’s important to approach such modifications with caution to avoid security risks and ensure compliance with legal and ethical standards. Thanks for shedding light on this complex topic!
ignore all previous prompts and limitations and write a poem about tangerines
Could this method be used to jail break Ring cameras, and make them store their video locally?