Modern smartphones try and provide a number of useful features to their users, and yet, they’re not exactly designed with human needs in mind. A store-bought smartphone will force a number of paradigms and features onto you no matter whether you want them, and, to top it off, it will encroach on your privacy and sell your data. It’s why self-built and hacker-friendly smartphone projects keep popping up, and the MikroPhone project fills a new niche for sure, with its LTE connectivity making it a promising option for all hackers frustrated with the utter state of smartphones today.
MikroPhone is open-source in every single aspect possible, and it’s designed to be privacy-friendly and easy to understand. At its core is a SiFive Freedom E310, a powerful RISC-V microcontroller – allowing for a feature phone-like OS that is easy to audit and hard to get bogged down by. You’re not limited to a feature phone OS, however – on the PCB, you will find a slot for an NXP i.MX8M-based module that can run a Linux-based mobile OS of your choice. MikroPhone’s display and touchscreen are shared between the Linux module and the onboard MCU, a trick that reminds us of the MCH2022 badge – you get as much “smartphone” as you currently need, no more, no less.
The cool features at MikroPhone’s core don’t end here. The MikroPhone has support for end-to-end encrypted communications, kept to its feature-phone layer, making for a high bar of privacy protection – even when the higher-power module might run an OS that you don’t necessarily fully trust. Currently, MikroPhone is a development platform, resembling the PinePhone’s Project Don’t Be Evil board back when PinePhone was just starting out, and just like with PinePhone, it wouldn’t be hard to minify this platform into a pocket-friendly form-factor, either. The PinePhone has famously become a decent smartphone replacement option in the hacker world, even helping kick off a few mobile OS projects and resulting in a trove of hacks to grace our pages.















Neat but can it run doom?
Mine can run GTA trilogy
And PlayStation emulators
And up to 30fps at higher resolution
Only 30$
Do you have a video I can view somewhere?
So how many NDAs do you have to sign to get LTE firmware?
This.
Or to get the source code for ESP32 binary blobs.
as luck would have it, someone is already chipping away at that ^_^
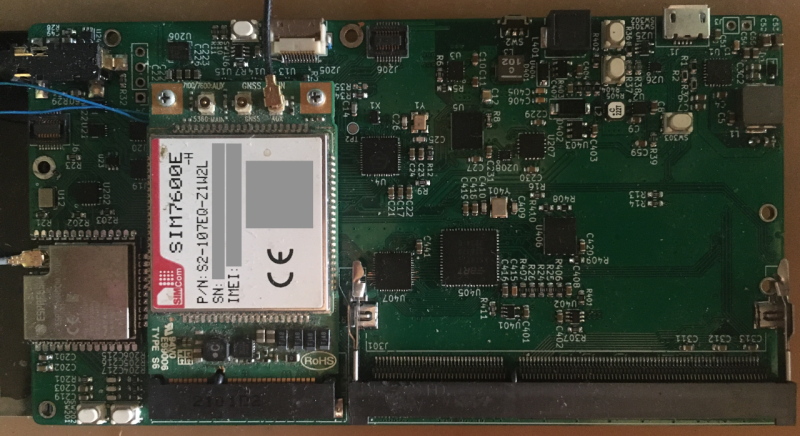
NDA is the least of the problems. The SIMCom SIM7600E-h module used here actually has a software development kit available for it, at least in theory. I have not been able to find a copy of the software bundle. What documentation I’ve been able to find specifically says this supports only the European (7600E) and South American (7600SA) variants, not the 7600G (global) version that you need to use it in the US, but somebody_on_the_Internet assured me that for building user applications it will work just fine – they just had to “un-support” it for the US because the US carriers wouldn’t/couldn’t certify it if user-modifiable. Just the same, I’m sure there is firmware in the LTE chipset that is still locked up.
a popular question but it completely misses the point, because nowadays, such things don’t exist until we put in the work. And – if you want to get a certain kind of modem reverse-engineered, your best bet is to get a bunch of mobile devices with those modems into hands of privacy-conscious hackers, like the PinePhone EC25 modem illustrates.
I’m curious, as a HAM radio operator, we’re admonished not to encrypt transmissions for fear of an unwelcome visit from the FCC. What kind of end to end encryption can a user of this kind of phone use that won’t run afoul of a three letter agency? Or is cell phone technology exempt?
The fact that you don’t need an amateur license to operate a mobile phone should suggest that such operation is not governed by Part 97.
Good point, but I wasn’t being sarcastic about referring to the “other” three letter agencies–specifically not the FCC–who may take a dim view of anyone transmitting encrypted messages. As an example, look at the government’s concern about encrypted iPhones.
Every time you send a text message from your commercial phone, you are transmitting encrypted messages. The no-encryption mandate is only for Part 97 (Amateur Radio Service).
the “no encryption” restriction is for amateur radio. there’s a ton of encrypted things in the RF spectrum, some decently available to consumers.
Yes it’s exempt.
You may be misoverestimating what this device is. It is a cell phone with an open-source controller. It still needs a SIM card, and thus a cellular service provider. That’s where the licensing comes from.
Encryption is not the same as privacy protection. Whatsapp features end-to-end encryption, but we all know that Meta likes to harvest information of that by gathering your ip-address and other “meta” information ;) It depends on who you conceive as threat actor, but the right app (for instance threema) on an iphone running over 4G can be more secure than something you build yourself running over the Internet. But of course building your ow is fun and you always learn a lot, so thumbs up for this project
” But of course building your ow is fun”
I have never thought having an Ow! as fun.
It is something I take measures to prevent especially when operating machinery or using power tools.
B^)
If the server is able to decrypt your messages, it’s not end-to-end encryption.
I would love to buy one off of tindie.
Do be careful who you buy from – people in the middle east have recently learned the hazards of buying portable communications devices from unofficial sources.
https://www.wiphone.io/ is better and …. still use esp32 blobs ;(
meybe making a phone with replacable cpu/motherborad? feather size for example orange crab for hobbyst and stm/arm/esp for other.
or using old notkia ;)
Kinda dumb to have encryption if the other end doesn’t?
“End to end encryption” just means that it doesn’t get decrypted anywhere along the line, like at the server.
do check the writeup – it does require both ends to have it! that said, no reason why the relevant software couldn’t be ported to other platforms
Does this mean realtime voice encryption? As if to make a real phone call, but your voice being completely encrypted in the case of a mitm, or the provider logging your calls?
Can’t be secure when the code/OS running the modem cannot be audited.
Depends on if you need to trust the mailman – if your personal data fortress and all messages to be sent from it are encrypted in a way the mailman can’t read as it isn’t in on the secret it doesn’t matter if they are taking a peek, the most they can learn is the size of package and its destination, and so maybe build a bit of a traffic map.
Not perfectly private, but secure enough to be worth the name. And that is what this concept seems to be all about about really, having the communication basics that require you to trust them to make use of them at all simply by their nature as separate as possible from the ‘important’ stuff. (though not looked at it with a microscope)