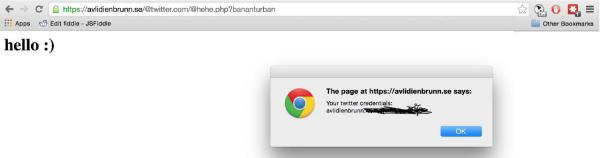
Lastpass is a great piece of software when it comes to convenience, but a recent simple hack shows just how insecure software like it can be. [Mathias Karlsson] nabbed a nice $1000 bounty for its discovery.
Lastpass’s auto-fill works by injecting some html into the website you’re visiting. It runs a bit of Javascript to parse the URL. However, the parsing script was laughably vague. By changing the URL of the page, inserting a few meaningless-to-the server slugs into the URL, an attacker could get Lastpass to give it a password and username combo for any website.
The discussion in the HackerNews comment section more-or-less unilaterally agreed that most systems like this have their glaring flaws, but that the overall benefits of having secure passwords generated and managed by software was still worth the risk when compared to having a few commonly reused passwords over multiple sites.
One could get a more secure key manager by using software like KeePass, but it’s missing some of the convenience factor of remote-based services and relies on a user protecting their key files adequately.
Still, as scary as they are, openly discussing hacks like this after responsible disclosure is good because they force companies like Lastpass, who have some very big name clients, to take their code review and transparency more seriously.