Gather round and hear the story of how a hacker outsmarts a criminal. [Zoz] was robbed and they got his desktop computer. Gone, right? Nope. Because of a peculiar combination of his computer’s configuration, and the stupidity of the criminal, he got it back. He shares the tale during his Defcon 18 talk (PDF), the video is embedded after the break.
[Zoz’s] first bit of luck came because he had set up the machine to use a dynamic DNS service, updated via a script. Since the criminal didn’t wipe the hard drive he was able to find the machine online. From there he discovered that he could SSH into it, and even use VNC to eavesdrop on the new owner. This, along with a keylogger he installed, got him all the information he needed; the guy’s name, birth date, login and password information for websites, and most importantly his street address. He passed along this juicy data to police and they managed to recover the system.
http://www.youtube.com/watch?v=U4oB28ksiIo
[Thanks Ferdinand via Gizmodo]
















@atrain:
Changing MAC address in OS doesn’t flash it into network controller, original MAC is still loaded after resetting the computer.
And IMEI can also be flashed.
@bullzebub @atrain MAC address? This identifies an interface not a system and can be trivially spoofed.
What about using ‘panopticlick’ type signatures to track a machine? (see the EFF site for more info)
I saw the name Zoz in the description and immediately thought of “Prototype This!” – then I thought “poor dumb thief”. Some of his security features were accidental, but the odds of a hacker accidentally setting up his machine to screw even a dumb thief are far greater.
I’m just glad to see a stupid thief get what’s coming to him!
@stu
yes that zoz
hy tell it on the movie
i have tip this i found it to funny
@cantido: Well said.
If those who don’t take the time to read: It’s a Macintosh! Not a f0cking Linux box!
candito:
Yes, I didn’t watch the video so I didn’t catch that he was using Mac OS X, and I don’t think it takes a rocket scientist to believe that it worked as it did. However, I have disdain for the presenter because he didn’t use passwords or full-disk encryption on his computer which would have made a third party using it impossible. Sorry to steal the thunder away from all of you out there that get a lift out of it. I don’t even think it was a more desirable outcome. Ever hear of insurance?
We are talking from the point of view from AVERAGE people out there that would steal computers without wiping them out first or investigating them for eavesdropping devices. Why all of this talk about rooting the Linux device? The whole thing is stupid.
Saying GNU Linux would be enough cover the entire operating system.
To claim that I don’t understand Linux from my post in the way that you interpreted it is sign of a learning disability. I won’t discriminate.
@cruisefx
>>Yes, I didn’t watch the video
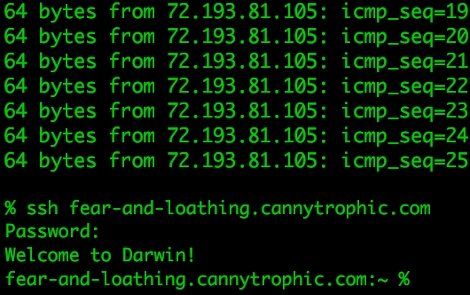
Well.. even the image here on HaC says “Welcome to darwin”.
>>he didn’t use passwords
Watch the video.. his passwords were in his keychain. It’s not uncommon to have a machine boot up and log into the main users account.
>>full-disk encryption on his computer
Does anyone in the real world have full disk encryption setup on a machine for desktop use?
It cripples your IO to the point that the machine is unusable. I have a USB drive with a LUKS setup on it.. works lovely.
>>which would have made a third party
>> using it impossible.
As he says in the video, his lax security was the only reason he was able to get the machine back. It took him a long time to find it even then.
>> Ever hear of insurance?
Insurance doesn’t get his data back.
>>from AVERAGE people out
AVERAGE people go around stealing computers?
>>there that would steal computers
>>without wiping them out first
I presume most people that steal computers steal them to sell on and would wipe the machine of all it’s exist junk first and maybe run a UV light over it to find any markings.. oh and rip off any stickers with serial numbers on. Or at least the person they sold it to would.
>>Why all of this talk about rooting
>>the Linux device? The whole thing is stupid.
I mentioned rooting Linux because you seem to think it’s impossible to do. If you have physical access to the machine it’s actually very easy.
>Saying GNU Linux would be
>enough cover the entire operating system.
You makes no sense.
>> To claim that I don’t understand Linux
You installed ubuntu and now your an linux expert right?
>>Yes, I didn’t watch the video
>Well.. even the image here on HaC says “Welcome to >darwin”.
Are you aware that Darwin is available as a standalone Unix distro.? And that image could have been put together from many sources.
>Saying GNU Linux would be
>enough cover the entire operating system.
>You makes no sense.
Right. Linux, the kernel, and all of the GNU tools make up the operating system. Thus, GNU/Linux. Can’t believe you never heard of this.
>>Why all of this talk about rooting
>>the Linux device? The whole thing is stupid.
>
>I mentioned rooting Linux because you seem to >think it’s impossible to do. If you have >physical access to the machine it’s actually >very easy.
I’ve been doing it since 1999 using a boot disk, chroot, and passwd. Not news to me.
I prefer Debian over Ubuntu for many reasons. It is a ripoff that has a Granola hippy/hipster theme to it.
>>there that would steal computers
>>without wiping them out first
>
>I presume most people that steal computers steal >them to sell on and would wipe the machine of >all it’s exist junk first and maybe run a UV >light over it to find any markings.. oh and rip >off any stickers with serial numbers on. Or at >least the person they sold it to would.
It is least egregious to presume that someone would want a system that doesn’t have other people’s junk on it. It would annoy the hell out of me, personally, to be using another person’s setup.
>>full-disk encryption on his computer
>
>Does anyone in the real world have full disk >encryption setup on a machine for desktop use?
>It cripples your IO to the point that the >machine is unusable. I have a USB drive with a >LUKS setup on it.. works lovely.
Have you heard of TrueCrypt? Works wonderfully and seamlessly.
>> Ever hear of insurance?
>
>Insurance doesn’t get his data back.
Backups should. Even the thief has probably heard of Mozy. (LOL, Mozy…)
One more thing, if the thief was sensible, then they should have wiped the computer anyway, rendering any personal data also erased. This Dynamic DNS adventure can only go so far until it starts to run out of gas.
Protip: Sell stolen computers without the hard drives.
RE: (story)
It is a nice story. It might even be true.
RE: (skeptics)
Running Ubuntu on the ‘puter your mom bought you for Christmas does not give you any real insight on actual administration or security.
RE: cantido/cruisefx
Average -ninja- go around stealing computers. Beware the ninja.
cmholm, i don’t mean to be a pedant, but…
What happens in vergas, doesnt stay in vegas with vnc
So what he’s saying near the end there with regards to serial number; if the thief had just scratched off the white serial number sticker, they would’ve left it there? (Not checking BIOS of course)
Great advice for thieves here too!
I wonder how did you konw your stolen Apple’s dynDNS, did you preinstall in it or trace it by MAC? How fool to get a stolen computer without kill the disk data, is it?
The real moral of the story: if you steal a computer, take the hard drive out, throw it in a river, and replace it with another one. Bonus points if you replace the case as well.
awesome. Finally a use for those nasty little buggers of key loggers that has plaugued us all at some point… Congrats i love this article
It’s called single user mode. You can get onto almost any unix/linux system that way…
sounds a little contrived
people stil use dialup? what about if he had ADSL with a firewall blocking vnc/ssh ?!
interesting seeing the ethical issues in different peoples opinion.
I think ZOZ made it clear that his security was marginal at best.
He also said that he was living in San Francisco at the time it was stolen not Boston.
I also got the impression that he knew he was lucky. After not finding the machine online for a couple of months, he had all but given up looking for it. Had the idiot who had stolen/received it bothered to do anything to clean up the machine we might not have been so entertained.
Here’s an idea. This should work provided the thief doesn’t decide to wipe the drive (which he should if he’s even remotely smart):
use TrueCrypt to encrypt your hard drive and make a hidden partition. Then put the password for the fake partition on a label on the side of the computer. Install LogMeIn, VNC, SSH, or anything similar on the fake partition, and probably just have the fake partition run the same copy of Windows (or Mac, or Linux, or whatever) that the real partition runs. Then your data is kept secure, and you have tracking installed and ready to go! Plus, the tracking won’t be running when you use your machine like usual, not using up resources.
it occurs to me that if you leave something in someones car and cant call it stolen and personal data on a company on a company computer isnt personal is companies. . .shall i go on.
Great story! He was totally pwned!
I had my Mac Stolen, almost exactly a year ago.
Got into computers just a few months ago, so I know bits a pieces. Mostly just web design, which is probably not going to help me.
Anyway, I had it stolen at school, found my old IP address tonight on an old Dropbox account. Tracked the IP to Saginaw, MI. About 45 miles from where it was taken, but that’s all I’ve got so far.
Does anyone know how I can sort of do what this guy did, and track his activity while using the computer? Any tips would be much appreciated, and great video, made me laugh the entire time.
@Thomas There’s not much you can do. He happened to have an SSH server installed, so he was able to login and install VNC and a keylogger. You might do better to supply the IP to the authorities and see what happens.
Yeah I know it has something to do with the router blocking it, getting port access. Like I said I am new to this.
As far as the cops, yeah I tried that from the start. I don’t think they really give a shit unless its a parking ticket or a DUI.
I’ll keep snooping around, someone has the answers.
Thanks for the feedback though.