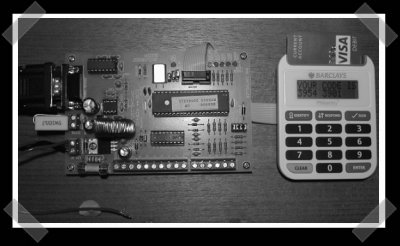
[Mr G] in London sent in his pin sentry hack. He wasn’t pleased that the device looks like an old calculator, so he rigged up a SMS board to send him his pin on demand. He multiplexed the output of the display driver to the SMS board. When he authenticates from his phone, the board sends a message with the latest code.
39 thoughts on “SMS PIN Sentry Reader”
Leave a Reply to bazgingeCancel reply
Please be kind and respectful to help make the comments section excellent. (Comment Policy)















Wow, great write-up!
That was packed so full of information I can barely contain myself. Code? Schematics? Any information at all?
Oh well, at least we can see the pin number.
The article was so weak I had a poke around the server. This is way better than the PIN thing.
http://www.mrg9999.com/pub/PHSB/ report cards
http://www.mrg9999.com/pub/picx/GT-SUIT.JPG amazing suit man ;)
There is much much more in the pub folder. Very entertaining. BTW nice kitchen ;)
Could someone please explain to me what this actually does? as I understand it the circuit to the left grabs a number from a calculator looking thing on the right and sends an SMS message with the number to his cell phone (I think?). I thought pin numbers were only ever assigned once, when you first get the card… so what does this do exactly and what purpose does it serve?
This looks like a two – factor authentication system for use with internet banking. In order to log into his account on the bank website, he must put his card in the Key Generator (calculator type thing), and put in his PIN (two things he has, one thing he knows) and gets from this device a one-time password to enter into the website.
He doesn’t want to have to carry around the stupidly huge key generator so he rigged it up so he can contact this device (call it? sms msg it?), and have it SMS him back with the current login key.
I have never seen that rolling PIN generator thing before, and im sure others here haven’t ither, which is why were all confused. Their like those IT key chain token things i guess. What banks out there use this? I have never seen them before.
#6: Barclays is a british bank. This two-factor system is most likely what i’ve heard referred to as chip and pin system.
no, it’s not chip and pin – chip is your standard credit/debit card and pin is your ATM pin used in place of a signature
This calculator is used to authenticate you for on line banking, scary thing is it a) dosent connect to the outside world and b) is not tied to any card (both myself and my wife have one and ot doesn’t matter which one we use). So given it knows if your atm pin is correct or not , the pin *must* be stored on the card :( Lets hope it’s encrypted !
@#7 – No this is not the chip and pin system. The chip and pin is added security to bank cards that works in conjunction to the magnetic stripe, you have to enter a pin code when buying things instead of signing for your card now. The chip is on the card and the pin is self explanitory. This is a new type of authentication system used for online buisness banking over here in the UK. You use your card and pin on the calculator and it generates a onetime password to log into youronline bank account.
It’s Barclays (a UK bank) PINsentry. You can see a demo of it in use here:
http://www.barclays.co.uk/pinsentry/demo_login.html
It is NOT chip and PIN. The PINsentry (or card) also does not know your pin. It is simple a challenge and response system. Even if you enter an incorrect PIN, you still get a repsonse (but different to if a correct PIN is entered) and it’s down to the bank to decide if the response is correct, or not.
this is awfull..
i have a device like this, which looks like this:
https://bankieren.rabobank.nl/rabo/dp800.gif
it’s small and i take it with me often..
but as soon as i’ve wanted to take a peek inside, the device locked up.. it’s what should happen! these devices should be small and equiped with anti-tamper sensors, not as ugly and unsafe as these..
i still like the hack, but the bank should’ve made a better device by itself (in the netherlands some banks already send sms with login codes)
Very interesting trick right there… I’m wondering where such SMS boards would be found, I’d have a bunch of utilities for it :)
i would assume the little calculator thing has a RTC in it and generates the pin based on the time along with a unique code on the card. Same thing server side so the system knows what code to expect at any given time. Yes/No?
to #10:
According to the manual that comes with the pinsentry if you enter 3 wrong pin codes it will lock the device. What makes you think it will accept any pin ?
Is this just to check your balance and perform other banking admin actions? Is this required for purchases as well? It would be really annoying if it were required for purchases…
all he is doing is VERRY generaly telling you how to do this i wouldn’t call this a hack
Online stores in the Netherlands can offer iDeal payments (pun probably intended). It’s a great system, where you use the chip on the card and a provided code.
With my bank, Abn-Amro, I get an 8-digit code from the Abn-Amro site. I insert my card into the device, enter my PIN (if incorrect, I get a notice. If incorrect for the third time, chip locks up). I enter the 8-digit number and get a 6-digit number back. I enter the 6 digit number on the site, and am authenticated. It’s a pretty secure system, as I understand it.
its not supposed to be practical.
its not even supposed to be elegant.
its a HACK folks….Some dude took a calculator and a handfull of components and built something you didnt even think of—-using parts never intended to be used in such a way, to create an entirely new and different machine; unique from any other in the world. Its a HACK proper, regardless of how convenient it is for you to carry to the grocery store.
Having said that…..some schematics would be nice. a diagram or a napkin with some scribble or something?—not that I would do anything with it but read it as I probably wont ever build one…..doubt I will even have a need for one…..thats not really the point though.
Maybe instead of bitchin we should all offer our support and send Will some hacks we all know and love but have yet to see on HAD…..maybe lighten his stress load for the next week? Will, I am sending you my top picks for as-yet un-featured hacks (good ones with writeups and all….) right after I post this….
I encourage you all to do the same.
Here in Germany, I got a similar device from my bank. But in my case it’s not used to login to online banking, instead it is required for every online transaction you want to make. The system started about half a year ago. Before, you had to enter a TAN number for every transaction. Now you have to enter the bank account number, where you want to send the money to, into the device and get back a 6 (or was it 8?) digit number as TAN. It also expires after a few minutes.
But different from the device in this article it does NOT require your card… Maybe it’s registered to my card, haven’t tried that, yet.
Thanks for the comment before about opening the device what causes it to lock up.. I also already had the idea to take a look inside to find out how it gets the numbers. Think it was good to not really do that :)
Some clarification
All I have done is interface my banking authentication device to a SMS controller(modified). so that I don’t have to carry the damm thing around. It is like not having to carry one’s RSA token(which incidentally I have also remoted).
SMS controller
http://www.jaycar.com.au/productView.asp?ID=KC5400
Could you explain in more detail just how you interfaced the device to the sms controller? Does the sms controller include instructions to help achieve this? I hate carrying around those things (netkey, one time password, token, etc) as the banks here in Mexico require a different one per bank so it no longer an unobtrusive keychain dangle, it is several!
to #13.
The entered PIN will be hashed into the 8 digit code the PINSentry device generates.. the card won’t have the PIN on it. If the decoded PIN (from the submitted 8 digit code) turns out not to match the one held on the server 3 times then it will trigger a lockout for the next time that card appears at an ATM or in a shop.. it wont actually write the lock to the card just as it didnt read the PIN from there.
It does accept any code I just tried it on mine.
I got one of these calculator type things from Barclays. It’s called PinSentry.
It clearly states in the instructions that if you enter your pin incorrectly three times your card will be locked. As there is no connection to the outside world this must be done via a pin stored on the card on the chip. Presumably also to lock your card the device must be able to write to the chip to tell it that it is now locked.
Presumably there is some encryption. Whether this can be reverse engineered to allow the PIN to be determined for any card I don’t know. However I wonder if you could use the PinSentry itself to (laboriously) hack cards to find their PIN.
All it would need is a way of bypassing the card locking. Maybe this could be done by simply putting tape over the write contacts on the chip so that the device can’t write to the chip to tell the card that its locked. Maybe its a little more complex than that. Maybe they check they can write to the card as part of some authentication procedure?
I’ll do some investigation for sure. Anyone know if I’m barking up the wrong tree completely?
The PINsentry isn’t connected to the outside world, and the card does not store the PIN.
What I think happens is the card will store a validation number. The PINsentry can use the PIN to generate a validation number, and see if this matches the one on the card.
So yes, there might be a way to use the PINsentry to still calculate the correct (or a number of possible) pin numbers. So I do wonder if overall this is a secure idea.
my pinsentry does not accept any PIN. if i enter a wrong PIN after pressing Identify, it knows and says the code is wrong (i just tried it). it only generates the 8 digit one time login code if i enter the correct PIN.
i would think that the way it does this is a one way encryption process, like normal unix passwords – presumably the card itself stores an encrypted version of the PIN, which is tested against whatever value is entered via the keypad after putting it through the same one way encryption. (i think that chip-and-pin readers work the same way?)
so you could use the pinsentry to brute force the PIN for a card, but only if you could figure out a way to disable the card lockout after 3 wrong tries. i would hope that the bank knows this and that the pinsentry is designed in such a way that the lockout mechanism couldn’t be disabled without disabling the PIN test method.
I did have a similar idea as soon as I realised I’d have to carry the bloody thing around, but there’s something I don’t get: surely you have to leave your card at home, which is far more inconvenient than not being able to get into online banking at will?
to #23 and a host of others.
The card contains the PIN. It works the same as Chip & PIN. In fact, it is a Chip & PIN card application!
You enter the PIN, the card verifies the PIN (yes, the PIN is stored in the card!) then generates a cryptogram based on some other variable input data and the crypto keys (also in the card). The calc device puts part of the cryptogram into the code – the other part of the code is the variable data the bank needs to recreate the code for validation purposes. The bank also has the same crypto keys. Hey presto!
The PIN is not hashed. Nor does it, or a hash, or anything else to do with the PIN, get sent to the bank.
If you enter the PIN incorrectly three times, the card locks and blam – no more cryptograms. At least, not until you phone the bank and go down to the ATM for a card unlock.
As for the “hack”, how is the PIN entered?
Isn’t there a big flaw in this that he has to leave his card plugged into his pin sentry device at home. What if he wants to get money out of an ATM or buy something at the shop and he does not have his card?!
I have heard anecdotally that these particular devices are not time critical, so for log in only (not payments where you have to also enter the amount and recipient account no) you can go through the process three times, generate three codes and take them with you to allow three log ins while you are away from your pin sentry. No idea whether this is correct though.
excuse my idioticy, but could some one explain to me whats to stop someone nicking my card, brute forcing it until a correct login is made with a pensentry, then walking to a cash machine and using my pin?
sry i didnt read over the commments, but now i have, can anyone confirm this thing can block ur card? i thought it probably wouldnt be able to, because it doesnt look like it would have enough battry power to perform such a task (surely?). but if you say its in the instructions then well im wrong.
Im looking for this.Im pay ….
It does accept any code I just tried it on mine.
If anybody seller this device.please call me.
shrewd@abv.bg
The info you’ve given is spot on, believe me, I’ve been doing my research and you’re info is some of the best out there.
OK, I can confirm that a PinSentry device WILL lock a card after 3 wrong PIN entries.
In may case, they weren’t wrong at all. I know I entered the correct PIN at least the last two times, so it looks like there is a fault with the machine.
To mj,
Once you have investigated and found an resault please post it, its rather interesting!
“Presumably there is some encryption. Whether this can be reverse engineered to allow the PIN to be determined for any card I don’t know. However I wonder if you could use the PinSentry itself to (laboriously) hack cards to find their PIN.”
That will be interseting…
The card reader responds that it will lock the card if you enter your pin wrong several times, to know the pin you enter is ‘wrong’ (when it doesn’t connect to the outside world) is must either: Know the pin (Stored on the card?) OR know a value it can relate to the pin (An encrypted, hashed or algorithm result based on the pin, again stored on the card)
Either way the pin or a value relating to it, is stored on the card, and if the algorithm the unit uses can be figured out (by multiple challenge responses?) the system would be insecure
“OK, I can confirm that a PinSentry device WILL lock a card after 3 wrong PIN entries”
No, this is wrong. The card locks ITSELF after 3 wrong PIN entries, whether these come from a PinSentry or another device such as the Chip-and-PIN device in the supermarket.
Therefore you can’t use the PinSentry – modified or not – to brute force a PIN number for a card, because the card’s chip will always lock out after 3 wrong guesses.
My Pinsentry device says ‘WRONG PIN, TRY AGAIN’ when wrong PIN entered.
Ahaa, its pleasant conversation about this paragraph at this place at this weblog, I have read all that,
so now me also commenting at this place.
you can get this now on most mobile devices via the barclays website. So this is obsolete really.