The modern smartphone is a marvel of sensors, radios, inputs, outputs, and processing power. In particular, some of those radios, such as WiFi and cellular, have grown fiendishly complex over the years. Even when that complexity is compressed down for the user into the one-dimensional space of the signal strength bars at the top of your phone. So when [David Burgess] was asked to look at some cellphone records of text messages and figure out where some of the more mysterious messages were coming from, it led him down a rabbit hole into the dark arts behind the glowing phone screen.
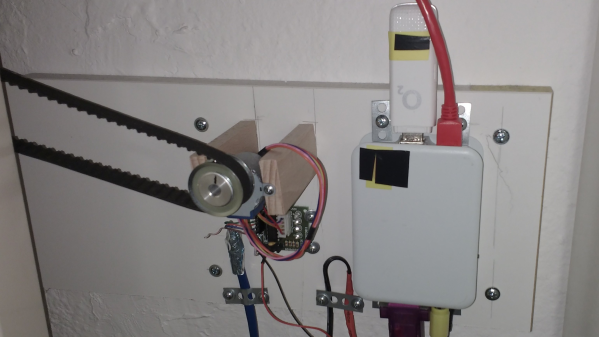
The number in question was 1111340002, sent by a phone connected to AT&T at the time, and was crucial for a legal case around distracted driving. [David’s] tools in his investigation were YateBTS (a cellular network simulator), SimTrace2 (pictured above), and old reliable Wireshark. Since the number isn’t a specific phone number and is not reachable from the public phone network, it must be a unique number inside AT&T processed by one particular AT&T SMSC (Short Message service center). The SMSC in question is in Atlanta and isn’t a typical texting center, so it must have some particular purpose. The message’s payload is raw binary rather than text, and [David] has done a pretty good job of decoding the majority of the format.
The most exciting revelation in this journey is that the phone (in the traditional sense) does not send this message. The processor on the phone does not know this message and executes no code to send it. Instead, the SIM card itself sends it. The SIM card is connected directly to the baseband processor on the phone, and the baseband polls the sim every so often, asking for any commands. One of those commands is an SMS (though many other commands have worrying consequences).
The SMS that [David] was chasing is triggered whenever a SIM detects a new IMEI, and the message lets the network know what about the previous and current IMEI. However, in the case of this message, it was unlikely that the SIM changed phones, so what happened? After some additional lab work and the deposition of an AT&T employee, [David] showed that a baseband firmware update would also trigger this SMS.
It’s a fascinating journey into the fragmented world of a smartphone’s minds and [David] does a fantastic job on the writeup. If you’re interested in sniffing wireless accessories, you will enjoy this soundbar’s wireless protocol laid bare.