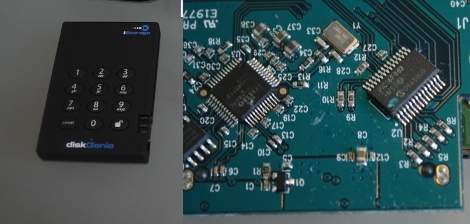
Our friend [Sprite_TM] took a look at the security of a code-protected hard disk. The iStorage diskGenie is an encrypted USB hard drive that has a keypad for passcode entry. After cracking it open he found that the chip handling the keypad is a PIC 16F883 microcontroller. He poked and prodded at the internals and found some interesting stuff. Like the fact that there is an onboard LED that blinks differently based on the code entered; one way for the right code, another for the wrong code of the right number of digits, and a third for a wrong code with the wrong number of digits. This signal could be patched into for a brute force attacking but there’s a faster way. The microcontroller checks for the correct code one digit at a time. So by measuring the response time of the chip an attacker can determine when the leading digit is correct, and reduce the time needed to crack the code. There is brute force protection that watches for multiple incorrect passwords but [Sprite_TM] even found a way around that. He attached an AVR chip to monitor the PIC response time. If it was taking longer than it should for a correct password the AVR resets the PIC before it can write incorrect attempt data to its EEPROM. This can be a slow process, but he concluded it should work. We had fun watching the Flash_Destroyer hammer away and we’d like to see a setup working to acquire the the code from this device.















AVRs attacking PICs?! Noooo!!!
God I love articles/blogs like this. I can literally read stuff like this for hours and never get bored!
Crafty sir. Crafty.
Hm… I really wonder how it actually locks the data. If it doesn’t transparently encrypt that – it’s useless. You can:
1. Replace a controller board with the one from the same, but unprotected drive
2. Are we able to dump the firmware/eeprom?
3. Is there a signal from pic that actually tells the other circuitry that a correct password has been entered? If so the crack will be ‘solder a wire from Vcc to pass_ok_pad’
Hmm If i remember correctly, there is a way to reset the internal code protection fuses and just read back the code. Involves etching away the packaging and using an UV light at the correct angle to hit the fuses. Any one remember the article that went over this?
@necromant
did you read the writeup? :P
anyway, great stuff as always from Sprite_TM
It’s a great article. For all the Dutch folks there’s a translated version at http://tweakers.net/reviews/1764/de-diskgenie-op-de-pijnbank-gelegd.html (Sprite_tm is also a moderator on the forums over there).
@Roman
The fuse reseting trick was Bunnie from xbox hacking fame.
http://www.bunniestudios.com/blog/?page_id=40
“When you want to unlock the disk, you get 50 tries. After that, you have to enter a special code (described in the manual) and then you can try for another 50 times. After that, the disk locks up and you can only reset it, erasing all the data on the disk.”
So, after 99 tries just swap the disk to something not-so-important and then the device erases it. You get 100 new tries?
@nave.notnilc
Looks like I’ve missed the aes part. I guess I’ll open up my silicon power armor and have a closer look what it does do store the passwd…
Nicely done Sprite_TM :) Not that I have ever seen one of these, but good stuff to know. Kudos on the due diligence as always :)
As a side note, I just love it when the guy doing the PCB layout rotates the ICs (specifically the microcontroller) 45 degrees. It looks so cool.
Excellent write-up! I love articles like this!
Just change your password to 9999. NO PROBLEMO.
@Just me
He doesn’t go into details about the reset when you reach the max tries (100), but I would bet that it just erases the key from the PIC rather than actually doing anything to the HDD.
So swapping HDDs wouldn’t do anything.
@goldscott: Don’t worry, it’s almost time for Episode III: Revenge of the PIC
Awesome, this is very similar to the “timing attack” which was used a while back on older Xbox 360’s (before the JTAG exploit) to downgrade the console to the base 1888 kernel. It worked by attaching a microcontroller to the 360’s motherboard to monitor the POST codes, and bruteforcing one of the bootloader’s authorization keys (which the 360 checked one byte at a time) by measuring the time it took to get a “fail” code. MS soon fixed that with an update of course
Why do I always associate PICs with amateurism?
Hi, I was going to purchase one of these. I admit I do not know what most of you are talking about, have you hacked into this unit or are you saying it is possible? There is a difference.
Thx
@JustMe, it was explained in the article. The Pic generates a lockkey based on a new password/hd. It sends that lockkey to the encryption micro, which generates a encryption key based on that to encrypt everything on the HD. Once a password has be rendered useless by the 100 tries, the pic and encryption micro generate new lock keys.
Switching the harddrive out when the 100 tries are up and putting it back in, even with the new, correct password, the key the encryption micro is trying to decode the harddrive data with would be different.
TL;DR version, it won’t work, Sprite TM has tried it.
@hans PICs are just another tool, not all problems are nails, and not all tools are hammers; so yeah, like if your problem calls for a legacy microcontroller that only executes an instruction every fourth clock cycle (or less), and has less features than all of it’s competitors… or maybe you just need to pound in a few nails… PIC is definitely your tool.
@Atomic Dirt Bike
“has less features than all of it’s competitors…”
now give some examples in details…
It just funny to watch how people reference to something they haven’t touch and information is so outdated, stop comparing oldest chip family to modern ones, why don’t you compare 18f instead of 16f. Its PIC’s strong advantage that they so diverse and yes there is very low level devices variations also Microchip usually don’t discontinue its oldest chips
Did anyone crack it or not??
Did anyone crack it? How did you manage it?
Nice article, i have exactly this disk and jep i lost my key… only know the last few digits.
Is there any way to get the rest without the method above? I have no idea what exactly he did :)
They’ve changed the tries from 50/50 to 10/10, so without the eeprom write being blocked/reset, brute force isn’t possible again….