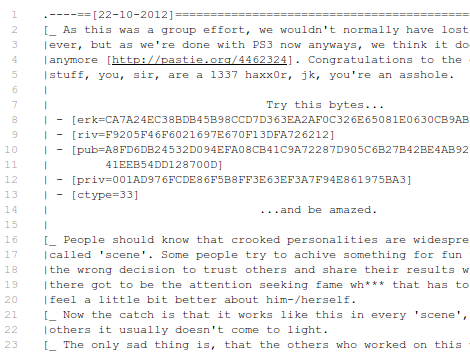
It looks like the security of the PlayStation 3 has been cracked wide open. But then again we’ve thought the same thing in the past and Sony managed to patch those exploits. The latest in the cat and mouse game is the release of the LV0 encryption codes for the PS3 console. The guys who discovered the magic strings of characters supposedly intended to keep them a secret, but have gone public after there was a leak and some black-hats now intend to use them for profit.
The keys are the bottom layer of security when pushing firmware updates to the PS3. With keys in hand, current and future upgrades can be unencrypted, altered, and repackaged without the gaming rig putting up a fuss. Our only real beef with the tight security came when Sony removed the ability to install Linux on systems marketed with this option. The availability of these keys should let you install just about whatever you want on your hardware.
[Thanks Kris via Phys]















this is good cuz the ps3 has yet to be fully utelized. more power i say and with the option of a posibul pc mod again yey for full out gaming on a power house console. lets make it just as good as our hacky friend the dreamcast
wat
i agree m8, dis cud probly be d best hack since xbox1
…I died a little inside writing that, even more so than reading your initial post
…aaarrrghhh! (brain hemorrhage) :P
Nice!
PS3 is damn near EOL.
I would say that Sony accomplished what they wanted to do with the ps3 security.
You may notice how there were almost no major vulnerabilities found UNTIL they decided to remove OtherOS support. I believe that’s the real player here…
How about MOL running in YDL on the PPC chip in there? ML on the PS3 – Now that’s a port…
Mac On Linux?
Too many acronyms
lol, Yes, and the ML == Mountain Lion
Mac On Linux
Yellow Dog Linux
PowerPC
Mountain Lion
:D
I have no idea what you’re saying there. There’s just too many acronyms.
I guess if you look at PS3 hardware, ya for the most part they did a pretty good job keeping the console like they wanted.
But remember the whole ps3 security fallout? I know that was more to do with the servers that ran the accounts but still a part of ps3 security.
NEVER buy Sony products. Ever. Not even headsets.
After what they did to Geohot?
Why would the hacking community even speak about this company?
Because it’s still a viable hacking target and this site is about hacking?
If you hate them so much you should be happy their lowest level of security just got bypassed.
except ps3 eye cams, they are great and I suspect they are sold at a loss ($10 in my local shop :o)
Yeah, I stopped buying Sony products after they put lik-sang out of business for literally no reason…
we’ve got a geohot 2.0
1.Geohot glitched HTAB before otheros removal
2.bootldr isn’t compromised/can be fixed
Geohot didn’t release anything before the OtherOS removal, he just showed that it was possible to crack the security in some way on the console, sony got scared and removed OtherOS in hopes that it would take away most points of attack. That made everyone pissed and more and more devs started to look into the security of the PS3, thats when those darn piracy dongles showed up and after that Fail0verflow found the signature keys.
Funny thing is that OtherOS had nothing to do with 1. Enabling piracy
2. The signature keys getting released
Those happened only because Sony wasn’t implementing their security well enough. I believe that team fail0verflow even said that they wouldn’t have looked for security flaws in the system if OtherOS wasn’t removed, as they only wanted to crack the console so they could get back their beloved linux
I agree with some points made above but the main reason Sony decided to remove the OtherOS feature was to prevent mass sales of the hardware to businesses & institutes looking to create an extremely cheap Cell CPU cluster with no intention of buying games, media etc from their services where they make the real money and attract game designers to create and license for their hardware.
Also the GPU was restricted within the OtherOS feature crippling it for anything other than trivial / computational tasks.
I know it annoyed a lot of people, me included
xorhack
bootldr can only be updated in newer skus as they did starting in factory and with 3.60fw
However for everybory else they cannot update and since they need to maintain compatibility to lower skus and the last place they could encapsulate the loaders is owned…
The PS3 in terms of hacking kind of lost its interest (everything can be decrypted now)…
Only those that have the newer bootldr can’t do anything…
Does this means I can load win7 on a ps3? that would be pretty killer.
Or better yet load it up to work like a modded xbx would be some funny looks at lans.
No, Windows 7 only runs on Intel processors. Windows 8 has an ARM version, but this isn’t ARM, either.
Windows 7 only runs on x86 processors, Intel is not the only company making them. AMD would be the first obvious alternative.
You can run Win7 or Win8, but you can run WinNT 3.51. Believe it or not there’s a version of WinNT for power. Would be a nice hack if you ask me.
You can buy things such as the Progskeet flasher or the E3 Flasher which is a NAND/NOR flasher and can replace a “bricked” Ps3 regardless of which firmware it is on, as long as you made a backup of the original image installed on that hardware. You either soulder it up to the memory on the motherboard and if you ever screw up the firmware you can reflash back to which ever backup you created. The best firmware to be on right now is 3.55 Official firmware as it can be exploited with Kmeaw/Rogero firmwares.
The hardware in Slim PS3’s shipped from factory with OFW 3.55 and down have the same hardware keys as every single PS3 so it’s technically possible to downgrade even more PS3’s that are on OFW 4.30+. The problem is getting a software exploit in an official firmware on these “cracked” machines is hard as of yet.
The new Slim Ps3’s CHECH3x+ (500GB Top loading disc Drives) have all new hardware keys and can’t be hacked as of yet. Since future updates have to apply to existing Ps3 hardware types it’s easier to exploit further firmwares for future hardware revisons.
Isn’t this old news? Firstly, geohot published his hack an age ago, in response to sony removing other os support, which was in response to his comments on the flaws in ps3 security.
Secondly, did nobody see that talk 2 years ago where they completely dissected ps3 security at every level? http://www.youtube.com/watch?v=PR9tFXz4Quc. In this talk they showed you how to extract the private keys in every level of ps3 security due to flaws in the implementation of the encryption layers.
Neither geohot nor fail0verflow broke the lv0 encryption, and in fact if you had even bothered to watch the video that you linked everyone to – or were smart enough to understand it, which you obviously aren’t – you would have seen as much. Geohot and the fail0verflow guys only managed to find keys down to lv1, not lv0. Idiot.
Easy man, make peace not war.
Updated on 25.10.2012, 17:20: Apparently Sony delivers the slim version of the PS3 from CECH-30xx and the super-slim with lv0.2 that checks a second signature. This would mean that these newer models can not crack on the manner described above.
Sorry google translate is crude. Full Article here:
http://translate.google.de/translate?hl=de&ie=UTF8&prev=_t&sl=de&tl=en&u=http://www.heise.de/security/meldung/PlayStation-3-angeblich-final-gehackt-1736203.html
does this mean someone will be releasing new CFW soon? Or will people be a little scared of doing it after the geohot fiasco?