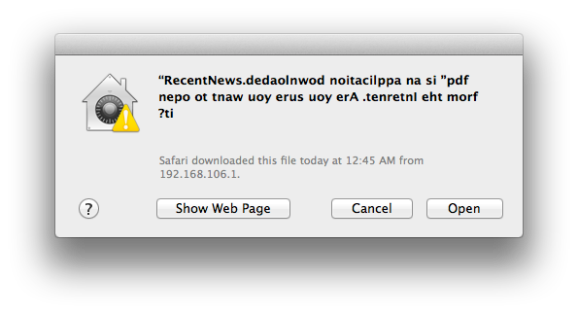
Check out this jumbled confirmation window. At first glance the message appears to contain a bunch of gibberish, but it can actually be read if you start at the right side and read each character moving left. The text displays like this because it is prefixed by a special Right-to-Left override Unicode character. The technique is being used in malware to obscure the actual extension of the file being launched. Notice that when written backwards your eye can still pick out the string “pdf” which may be enough to trick the uninitiated into approving the launch of the file.
This confirmation screen is launched when clicking on a piece of malware found in the wild a little over a week ago. If you do choose to run it, a decoy PDF file is opened in order not to arouse suspicion. But at the same time the program — which is signed with an Apple Developer ID — is installing itself in the home directory and making a cron job to launch at each boot. Sneaky!















And everyone told me OSX didn’t have viruses.
it’s not a virus….it’s malware -_-
.ekoj a dellac s’tI .ffo dos, hO
my fault sir, no need to get lippy. This is the internet after all….Poe’s Law and what have you.
Sorry, must’ve been the kawaii emoticon. Those things set me right off. We coo’?
For those who don’t know, I was making a reference to this.
Btw, does can I embed the rtl character in this box? Let’s find out.
I had to try one more time.
Most of the Windows “viruses” that Apple relied on to market their computers to non-tech-savvy individuals were actually malware and not viruses; it’s not like most users make the distinction, and actual proper virus infections on Windows were relatively rare.
Maybe people need to start telling you that you need education? As it seems you can’t identify what a virus is.
Maybe people need to start telling you that you need education? As it seems you can’t identify what a joke is.
It’s fuckface, all he ever does is pop ’round the comments to shit all over what everyone else is doing. Guy needs less education and more sterilization, really.
Remember Wheaton’s law, kids.
I remember back when hackaday said they’d moderate the comments.
*sigh*
Maybe if I give them half a million dollars they’ll do it.
It’s a trojan.
And by default setting, OSX won’t even display that advice, it will simply not open that application because isn’t from a (Apple) trusted source, or downloaded from the Mac App Store. Of course for knowledgeable users it seems unnecessary, like an antivirus software, but for average Joe’s or corporate computers, it’s better.
Unless you hold down CTRL and chose Open, when you get the option to actually run it anyway. Way smarter design than UAC.
I have also seen this exploit be used to show fake file extensions when they are hidden by default in Windows.
For example, the exploit would be “file[backward-char-code]gpj.”.exe, and show up as file.jpg.
First thing I disable, on EVERYBODY’S PC. For one thing, makes it easier for me to fix problems over the phone if people can see what’s what. I can’t BELIEVE nobody in Microsoft saw that vulnerability coming. All the disadvantages having 3 letter extensions, with none of the advantages. Hiding anything that might look a bit technical is not a proper user interface design method.
btw doesn’t file.jpg.exe in the forwards direction still work?
Yes it does. I do it all the time to individually suppress some of Windows annoying file handling routines but still want to know what the original extension was.
I meant “work” as in “is it still a massive security hole in current versions of Windows?”.
I’m still using XP, which I was dragged screaming into when some software demanded it. Nobody should be an early adopter if they want an easy life, and 6-months-past-obsolescence is about enough time for them to iron most of the bugs out.
yes it does, the attack is actually to make the extension seem to be part of the file name
so: al[rtl]gpj.exe comes out alexe.jpg added with the cue that this is a picture of a girl names alexe and no one thinks anything about it.
Good grief. It’s amazing what computer hackers think up, while at the same time utterly miserable what giant holes companies leave.
If you can’t read backwards you deserve what you get! This would have never happened if we hadn’t shifted from boustrophedon!
The ability to read backwards is unnecessary in this situation.
If you can’t understand what you are reading, namely, it all looks like a bunch of gibberish, why would you run the application anyway?
Only an individual with a head full of decomposing grey matter would do such a thing.
i think apple should use the language settings to determine text direction not the “?” in the filename.
it’s called unicode, and some ppl need to be able to display multiple languages/scripts at the same time.
Uhh… “pdf” isn’t actually backwards in that image… that would be why it’s so easy to pick out…
If you read the linked article it mentions that Apple considered this and show the file type forward, so you can read it in the example above. It’s hard for us to understand the picture above, since it’s not English. So has Microsoft thought of this?
The thing to do would be to create the new domain www so you can then create a web site called moc.knabitic.www.
Just proves that a web browser and especially Adobe software should be run in a separate virtual machine with minimal OS.
The picture above is in English, just read right to left instead of normal.
Doh! Guess I should have read the article…
Vulnerability in that VM would be equivalent to a vulnerability in Java, or a vulnerability in Chrome, or a vulnerability in flash, etc. Once you get arbitrary code execution, you can do pretty much whatever you want.
Software is software, and no amount of VM will remove the fact that when you connect to another computer you transfer information in two ways.
>Vulnerability in that VM would be equivalent to a vulnerability in Java,
You seem to be missing the point of what the OP was actually saying.. Unless there is a exploit that allows an attacker to escape out of the hypervisor or whatever is running the virtualised environment then the problem is limited to what is accessible from inside that virtualised environment. If you have a shitty app that you have to run sticking it in an environment you don’t care about is a good idea(tm). If you’re really paranoid about all the applications you are running you would setup something like SELinux or TOMOYO and write a rule set that gives processes access to the bare minimum of resources they need to operate.
> Once you get arbitrary code execution
Once you get arbitrary code execution in the virtualised environment you then have to escape the VM to get access to host…
>no amount of VM will remove the fact that when
>you connect to another computer you transfer information in two ways.
So you have an exploit that allows you to target the host environment while it passes packets for a guest?
i work with an f secure partner, it’s cool that they found something. i got even more to tell my customers now.
How do I modify my Grandparents mac to prevent executing software like this? They are pretty gullible and never should be executing anything they have downloaded on their own.
Parental controls may go too far. She lives a couple hundred miles away so my ability to tweak the machine is limited. And if I overly restrict my Grandmother’s access, she’ll raise a huge stink and take me out of the will.
I use teamviewer to log into and fix my mom’s compute. I’ve also used it with clients. Different flavours depending on your OS and really easy to use. Free for non-commercial too (I think).
You can’t since they’d accept that promt even if it was spelled right.
“Hibernate Once, Resume Many” configuration is used in embedded/industrial regions, but I rarely see them done in home. I believe it would be a great help to those people as long as malwares need to install themselves on local PC.
I like how people are arguing about how it’s “malware” and not a “virus.” It’s got to be one of the most useless arguments ever.
A bolt is a nail. Cancer is a cold. A tree is a shrub. Etc, etc
I think the cancer to cold comparison goes a little too far. “Cancer is Staph Infection” would be more like it.
Some distinctions matter, some don’t. You treat cancer differently from a cold. The outcomes are different if left untreated.
Mind going into the functional differences between a virus and malware from the user’s perspective? They have bad shit on their machines that is doing things they don’t want.
Except they are both wrong. Software of these types should be called __BULLSHIT_VIRUS_ALIAS_2__.
I love it, don’t outsmart the software, outsmart the user.
That just seems lazy to me.
ok maybe what apple should do too is do like what netscape did where all plugins require the submission of the source code to to be compiled into a standalone browser plugin.
in the same i think apple should make it that you as a developer has to submit (upload) all your resources to apple’s developer section to be packed and made into an installer ( dont allow the end user to make their own installer package).
also dont allow execution of code upon disk image mounting (remember chico de salon? from the newsgroups back in the 90’s) he changed something in the boot block of the image so a sound file would play.
only that more than just a sound file could be played you could run an application via the boot block hack.
so as a prank i copied the system 7 desk accessory “shutdown” to the image and set it so when the image would be mounted the mac would shut down.
that’s harmless compared to what can be done today since it just caused the mac to shut down
How many people are there who are stupid enough to go ahead and click Open when confronted with a dialog box of backwards text?
Enough and too many.
Thanks for posting this. I’ll keep an eye out for it.
Only Apple could rip off BSD, make billions off it, then turn it into a malware magnet, and never give anything back to the BSD community. Well, maybe the not giving back thing is a good thing after all.
What about CUPS? And I would hardly call it a malware magnet as these exploits are not that common.
Anyway, that’s enough of defending apple, they don’t deserve it.
indeed, only Apple could make a *nix variant user-friendly enough to be commonly used as a desktop installation.
“… installing itself in the home directory and making a cron job to launch at each boot”
If it’s lounched on every boot, it’s not a cron job, but it probably runs from /etc/rc.local
Hmm… Would a sort of “language” parsing system work? I mean, if the meta-tags on the file were able to display the region of the intended recipient, maybe the file could be striped of the character before being display for the user.