Over the last few months, a few very capable hackers have had a hand in cracking open a Transcend WiFi-enable SD card that just happens to be running a small Linux system inside. The possibilities for a wireless Linux device you can lose in your pocket are immense, but so far no one has gotten any IO enabled on this neat piece of hardware. [CNLohr] just did us all a favor with his motherboard for these Transcend WiFi SD cards, allowing the small Linux systems to communicate with I2C devices.
This build is based upon [Dmitry]’s custom kernel for the Transcend WiFiSD card. [CNLohr] did some poking around with this system and found he could use an AVR to speak to the card in its custom 4-bit protocol.
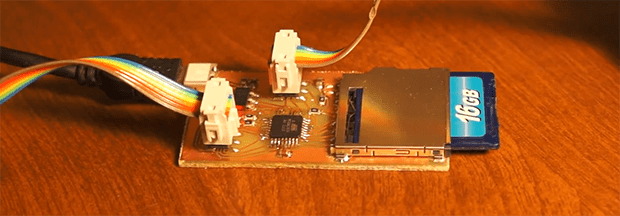
The ‘motherboard’ consists of some sort of ATMega, an AVR programming header, a power supply, and a breakout for the I2C bus. [Lohr] wired up a LED array to the I2C bus and used it to display some configuration settings for the WiFi card before connecting to the card over WiFi and issuing commands directly to the Linux system on the card. The end result was, obviously, a bunch of blinking LEDs.
While this is by far the most complex and overwrought way to blink a LED we’ve ever seen, this is a great proof of concept that makes the Transcend cards extremely interesting for a variety of hardware projects. If you want your own Transcend motherboard, [CNLohr] put all the files up for anyone who wants to etch their own board.















CNLohr is, again, doing crazy cool hack.
Very very cool!
This can be done a lot more efficiently, once we have better idea of how KA’s SDHC bus works. AFAIK, one can send SD commands direct to linux in the card, and it can reply (much faster). Sadly, so far, nobody knows exactly how. Just the general idea
This is a pretty neat hack. What I’d like to see is someone wiring the serial tx and rx pads to the unused pins on the SD card (pin 8 and 9, per the wikipedia article on SD cards). It would only work on modified cards, but you could leave the whole SDHC bus out of it, and have a more reliable communication method.
Pin 8 and 9 are used for the 4-bit protocol… And, the card doesn’t support the 1-bit protocol :(.
Awesome. Every post about this card has been great. I need to buy myself one of these.
Be carefully – this card good for hacking, but not so great for primary usage. Mine (16G) with RAW burs shots works very very bad – internal software reports to camera succesfull write operation, but in reality generates damaged and unreadable files.
It would be awesome if you could run wireshark on this or something to strip SSL certificates, or capture packets for cracking wifi.
could not do so, why? simply because the onboard wifi hardware will likely not support monitor mode, which means it will not inject any packets, in any way it is a cool hack
doesnt it? i thought ar6k driver did support it
Run full aircrack-ng system on it would be awsome!
I was doing this 12 – 13 months ago with a flucard pro – http://www.jaycar.com.au/productView.asp?ID=XC5620 – decided it was cheaper to buy a raspberry pi.
Incidentally, why aren’t busybox/kernel devs up in arms about the GPL violations?
The “GPL violations” don’t appear to be actual GPL violations. What Transcend is doing is shipping a binary-only driver along with the GPLed kernel, like what NVidia does with their graphics drivers. This isn’t ideal, but it’s not against the license. IMHO, IANAL, etc.
The GPL is not the GPL3, and most projects only have to disclose changes where the licenses have required. In this case, they do not have to publish changes if the kernel is the same uC based kernel already on the net. Compiling it does not make it a new work… ;-)
Open source does not mean free as in “free beer”…
I use Apache or BSD license for code I want to share, as people can use it for businesses etc.
Mewonders how long til the SD card hotspots are compatible with this