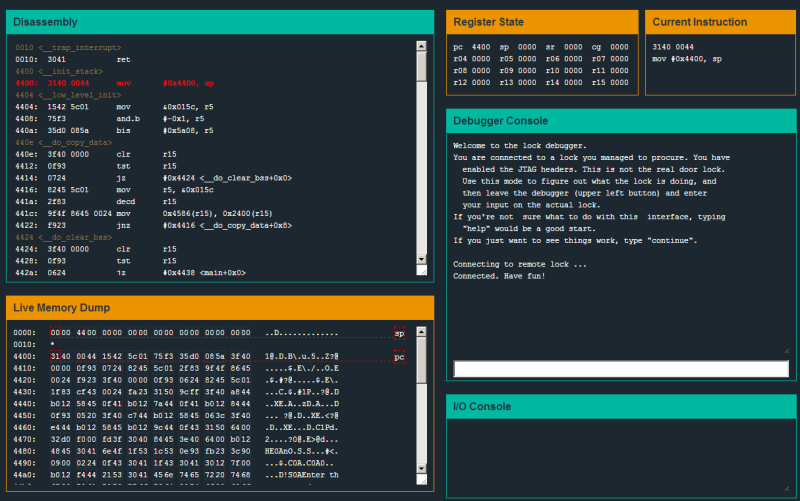
The folks at Matasano Security and Square have teamed up to build an online capture the flag (CTF) competition. The Microcorruption CTF focuses on embedded security and challenges players to reverse engineer a fictional “Lockitall LockIT Pro” lock system.
Each level places you in a debugging environment with a disassembly listing, live memory view, register view, and debugging console. You can set breakpoints, step through code, and modify registers like in a real debugging environment. Your goal is to figure out how to bypass the lock to collect bearer bonds.
While the device and motive may be fictional, the assembly is actual MSP430 code. The debugger is similar to GDB connected to a remote target using OpenOCD. There’s even a manual (PDF) to help you get up to speed with writing MSP430 code for the device.
This CTF looks like a great introduction to embedded security, and doesn’t require buying real hardware. It even includes a full tutorial to get you started.















Sounds a lot like a game I used to play around 2000 on a telnet server called drill.hackerslab.org (RIP) mostly about finding setuid scripts and TCP packet forging and things like that (to progress from the guest login level0. all the way up to userid level17). This does sound interesting, I’ll give it a spin.
I loved hackerslab! You could also write to the public_html for the level you pwned.
Been playing with this since last night, it’s awesome. Definitely makes all those security vulnerabilities like buffer overflows, stack smashing, and other spoilery stuff much more tangible. Working on Algiers right now, tearing my hair out and loving it!
Been playing with this since last night, it’s awesome. I’m not one to yell at the computer when playing games, but there have been several loud shouts of “PWNED!” and a handful of victory dances while playing this one.
Definitely makes all those security vulnerabilities more tangible — stuff like buffer overflows, stack smashing, and other spoilery stuff I won’t mention. Working on Algiers right now, tearing my hair out, and loving it!
yes this is so cool! I’ve always tried to follow along with spritemod’s stuff, but this is the first time I’ve actually got anywhere!
With which of his stuff?
that harddisk firmware hack most recently
Yeah. That’s his best work, I think. Literally changed what we consider secure.
Where did spritesmods come in relative to this post, though?
Really great stuff. For person who finds this kind of stuff seriously interesting and enjoys reading about it, but has never done it this is a godsend. A structured environment to hack about in, but rooted in reality – targets an actual microcontroller, and I could compile C for this imaginary lock if I wanted to. A legitimate all-in-one intro to exploitation, assembly, working in hex and reverse engineering. As one of the ‘have never done its’ I look forward to getting past the first non-tutorial level…
Matasano have put together a great recruitment drive here.
Eeey this is fun, also more difficult than I imagined.
Really interesting. Reminds me of corewars. This could be a serious and fun way of teaching assembly. I wonder if they will “port” it to other architectures (ie ARM for example) or perhaps TI is behind this and won’t support any other architectures.
For those interested in games based on programming:
http://www.corewars.org/index.html
http://rars.sourceforge.net/
http://corewar.co.uk/crobots/
I think (unfortunately) that this kind of programming is not a good way to get people into programming. I remember when I was in school and many many of the other kids complained about how stupid and useless it was to learn to write code in an “emulated environment, with no real-world use” (i cant remember the specific environment, it was some asm-variant, probably even one not found on any real cpu). this is however _great_ for improving your skills if you are already interrested. And if you do get kids started on using this then i am not going to fault you for proving my anecdote to be just that.
Oh and for those, who haven’t noticed, it’s a job listing from a security company named Matasano.
im crap at this sort of thing but am enjoying having a play and learning.