 In honor of DEFCON, this week we’re looking at some cryptography and reverse engineering projects over at Hackaday.io
In honor of DEFCON, this week we’re looking at some cryptography and reverse engineering projects over at Hackaday.io  Every hacker loves a hardware puzzle, and [Tom] has created a tool to make those puzzles. His Hardware Reverse Engineering Learning Platform consists of a shield with two ATmega328 chips and an I2C EEPROM. The two Atmel chips share a data bus and I2C lines. Right in the middle of all this is an ST Morpho connector, which allows an ST Nucleo board to act as a sniffer. The platform allows anyone to create a reverse engineering challenge! To successfully reverse
Every hacker loves a hardware puzzle, and [Tom] has created a tool to make those puzzles. His Hardware Reverse Engineering Learning Platform consists of a shield with two ATmega328 chips and an I2C EEPROM. The two Atmel chips share a data bus and I2C lines. Right in the middle of all this is an ST Morpho connector, which allows an ST Nucleo board to act as a sniffer. The platform allows anyone to create a reverse engineering challenge! To successfully reverse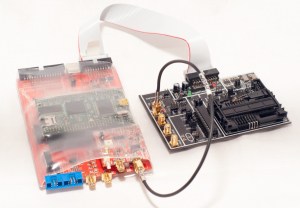 engineer a board, it sure helps to have good tools. [coflynn] is giving that to us in spaces with The ChipWhisperer. ChipWhisperer is an open source security research platform. The heart of the system is a Xilinx Spartan 6 FPGA. The FPGA allows very high speed operations for things like VCC and clock glitching. ChipWhisperer is an entire ecosystem of boards – from LNA blocks to field probes. The entire system is controlled from an easy to use GUI. The end result is a powerful tool for hardware attacks.
engineer a board, it sure helps to have good tools. [coflynn] is giving that to us in spaces with The ChipWhisperer. ChipWhisperer is an open source security research platform. The heart of the system is a Xilinx Spartan 6 FPGA. The FPGA allows very high speed operations for things like VCC and clock glitching. ChipWhisperer is an entire ecosystem of boards – from LNA blocks to field probes. The entire system is controlled from an easy to use GUI. The end result is a powerful tool for hardware attacks. 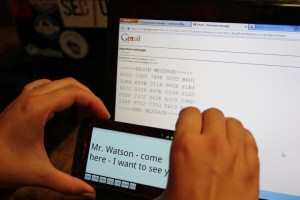 On the Encryption side of the house, we start by keeping the Feds at bay. The [Sector67] hackerspace has collectively created NSA AWAY. NSA AWAY is a simple method of sending secure messages over an insecure medium – such as email. A one-time use pad is stored on two SD cards, which are used by two Android devices. The message sender uses an Android device to encrypt the message. On the receive side, the message can be decoded simply by pointing an android device’s camera at the encrypted data. So easy, even a grandparent could do it!
On the Encryption side of the house, we start by keeping the Feds at bay. The [Sector67] hackerspace has collectively created NSA AWAY. NSA AWAY is a simple method of sending secure messages over an insecure medium – such as email. A one-time use pad is stored on two SD cards, which are used by two Android devices. The message sender uses an Android device to encrypt the message. On the receive side, the message can be decoded simply by pointing an android device’s camera at the encrypted data. So easy, even a grandparent could do it!  Next up is [Josh’s] Bury it under the noise floor. “Bury it” is an education for cryptography in general, and steganographic software in particular. [Josh] explains how to use AES-256 encryption, password hashing, and other common techniques. He then introduces steganography by showing how to hide an encrypted message inside an image. Anyone who participated in Hackaday’s ARG build up to The Hackaday Prize will recognize this technique.
Next up is [Josh’s] Bury it under the noise floor. “Bury it” is an education for cryptography in general, and steganographic software in particular. [Josh] explains how to use AES-256 encryption, password hashing, and other common techniques. He then introduces steganography by showing how to hide an encrypted message inside an image. Anyone who participated in Hackaday’s ARG build up to The Hackaday Prize will recognize this technique.  [yago] gives us encrypted voice communications with his ZRTP Hardphone. The hardphone implements the ZRTP, a protocol for encrypted voice over IP communications. The protocol is implemented by a Raspberry Pi using a couple of USB sound cards. User interface is a 16×2 Line character LCD, a membrane keypad, and of course a phone handset. Don’t forget that you need to build two units,or whoever you’re trying to call will be rather confused!
[yago] gives us encrypted voice communications with his ZRTP Hardphone. The hardphone implements the ZRTP, a protocol for encrypted voice over IP communications. The protocol is implemented by a Raspberry Pi using a couple of USB sound cards. User interface is a 16×2 Line character LCD, a membrane keypad, and of course a phone handset. Don’t forget that you need to build two units,or whoever you’re trying to call will be rather confused! 
Finally we have the Mooltipass. Developed right here on Hackaday by [Mathieu Stephan] and the community at large, Mooltipass is a secure password storage system. All your passwords can be stored fully AES-256 encrypted, with a Smart Card key. Under the hood, Mooltipass uses an Arduino compatible ATmega32U4 microcontroller. UI is through a OLED screen and touch controls. That’s it for this week! Be sure to check out next week’s Hacklet, when we bring you more of the best from Hackaday.io!















steganography, not stenography. Totally different.
Hey Adam, it’s steganography… stenography is the court recorders IIRC
damn you!
Arrgh! I Got the link right and screwed up the word. Thanks for the catch.
um… ‘stenography’ is a set of skills, such as typing and shorthand, used for transcribing dictation. I believe the word you’re looking for is ‘steganography’.
Haha the 5th element Mooltipass!
Sure the one-time-pad encryption thing is very wonderful and everything, using cameras as it does, but didn’t PGP solve this problem much better about 20 years ago? They haven’t cracked that yet, have they?
It has the advantage of not needing a secure channel to send the pads over in the first place, which eliminates the point of bothering with encryption if you have one.
If PGP had one problem, it would be the pain in the arse of having to manage a whole system of keys for you and everyone else. And the interfaces I last tried it with seemed written for the sort of person who could do PGP in their brain anyway. Not friendly or simple.
Unless it’s been compromised, then what’s really needed is PGP with a decent interface. A quick download, integrate it into Android, or even Gmail or whatever. So all the annoying stuff is taken care of automatically as much as possible. Encryption systems are much better the more people use them, and people don’t have the effort or ability to learn more than they really need to, to use it.
The idea has some potential, maybe a way of converting public keys into little images, would make them easier to deal with conceptually. And work with cameras! Do the same with signatures. People are good at comparing images, strings of characters, not so much.
Oh, I say PGP, I really mean any public-key encryption system.
The real problem is that the only people who are really spying on anyone can just have the manufacturer give them a backdoor with full access to all these devices, from the smartphones to the PC’s. If you didn’t cook the wafers, it’s not secure.
Hint: it’s not some crackhead in the hood that’s spying on you.
Diffie-Hellman, properly speaking. If someone can break that, well, we are in for some very interesting times. The tech or mathematical breakthrough needed to break it would lead to the complete annihilation of effective cryptography. No more secure authentication. No more credit cards. No more bank transfers. Everything would have to go back to paper in security envelopes immediately to be any more secure than a postcard.
The use of Android devices to hold and handle the one-time-pad encryption is a non-starter.
NSA could hack an Android device in a hurry. They are likely present inside the silicon of those devices already.
A better setup would use the lowest end controller you could to do the same job.
A tiny device that would fit comfortably on a key-chain and contain 4gb of flash, something like a Tiny84 as processor, a noisy diode for hardware randomness, a mic, a small speaker and a low cost LCD display. Use buttons to enter text messages by selecting characters from a scrollable alphabet. Send short messages as audio over any device capable of audio..a cellphone, a tablet, a PC or a plain old phone. Use DTMF tones since the phone system is set up to facilitate their transmission. Wipe the used bytes from the OTP data in the flash as you use it…thus no old messages can be decoded even if the device falls into unfriendly hands.
A suitable device should be possible for less than 20 dollars.
Using a really low-end processor pretty much assures that NSA is NOT inside.
The silicon is too simple and large-scale and it would be easy to see an attempt at mischief.
There are also lots of them already in the marketplace…
Flash can’t be easily “wiped” due to the write-balancer. It should use SRAM or DRAM for temp storage.
What you do is fill the 4gb space totally…that way you overwrite the data.
3000-5000 writes per block and the device fails readonly. overwrite used blocks with random data to be exchanged later with various friends later would make more sense. i.e. keep the device 100% full at all times.
Of course, then you just wear out every cell much faster, and replacement costs of the Flash memory far outweighs simply using the right technology in the first place :P
I’ve written an article titled The NSA, Snowden, And Citizen Cryptology. In thew article are links to create your own (analog) one-time pads using Scrabble tiles. also there’s a link to an article about USB dead drop file sharing: http://www.science20.com/square_root_of_not/the_nsa_snowden_and_citizen_cryptology-141431
No! No advertising. If you have something to say, do it here.
Seriously? You’re calling my post spam? Fine, then. I’ve added as a Hack A Day project:
http://hackaday.io/project/2378-The-NSA%2C-Snowden%2C-And-Citizen-Cryptology
An Android based device would keep the NSA away? Seriously… Android?!?
You mean that thing where even the hamster feeding app needs full access permissions to run, and it would be so tempting a scenario where.. say one every 50 apps developers would work also for some 3 letters agencies?
Can you guarantee there is nothing phoning home or reading keys (virtual keys, even easier than sneaking a sniffer) in your phone or tablet? If not, you better not rely on that toy for data protection.
And before someone even thinks of some OS war trolling going on, let me get it straight: the same principle applies to iOS, Windows and every other mobile OS in the market.
I agree with your message but not your tone aha :)
I can understand, but Google is acting in some strange ways lately so that our trust in their “don’t be evil” principle deserves to be reconsidered.
How many people noticed they early this year hid the discussion search filter, then disabled it completely in july? Now our searches are inundated by paid for sites where a few months ago we had blogs and forums results. This probably is reducing spam to some degree, but also killing the search for honest opinions.
Sounds trivial? Then how about Joe User who is searching for information on some politician and instead of common people discussing all he gets is official information coming from that politician press office?
Openmoko ?
The NSA Away project page mentions they disable all radios at the hardware level. Assuming they mean cutting traces, then yes – they can guarantee that nothing is phoning home.
Just finished “How to Wreck a Nice Beach” by Dave Tompkins. It is a history of the vocoder and all of the SIGSALY stuff involved all the way up to modern autotune that studios love. A fun read and highly informative. I think HaD readers would dig it so here is the amazon link if you want to check it out
http://www.amazon.com/How-Wreck-Nice-Beach-Vocoder/dp/1612190928
Not trying to spam or anything just thought it was applicable to the voice cryptography :)