Once upon a time, arcades were all the rage. You could head down to your local arcade with a pocket full of quarters and try many different games. These days, video arcades are less popular. As a result, many old arcade games are becoming increasingly difficult to find. They are almost like the artifacts of an ancient age. They are slowly left to rot and are often lost or forgotten with time. Enter, MAME.
MAME (Multiple Arcade Machine Emulator) is a software project, the goal of which is to protect gaming history by preventing these arcade machines from being lost or forgotten. The MAME emulator currently supports over 7000 titles, but there are still more out there that require preservation. The hackers who work on preserving these games are like the digital Indiana Jones of the world. They learn about lost games and seek them out for preservation. In some cases, they must circumvent security measures in order to accurately preserve content. Nothing as scary as giant rolling boulders or poison darts, but security nonetheless.
Many of the arcade cabinets produced by a publisher called NMK used a particular sound processor labeled, “NMK004”. This chip contains both a protected internal code ROM and an unprotected external ROM that controls the sound hardware. The actual music data is stored on a separate unprotected EEPROM and is different for each game. The system reads the music data from the EEPROM and then processes it using the secret data inside the NMK004.
The security in place around the internal ROM has prevented hackers from dumping its contents for all this time. The result is that NMK games using this chip have poorly emulated sound when played using MAME, since no one knows exactly how the original chip processed audio. [trap15] found it ridiculous that after 20 years, no one had attempted to circumvent the security and dump the ROM. He took matters into his own hands.
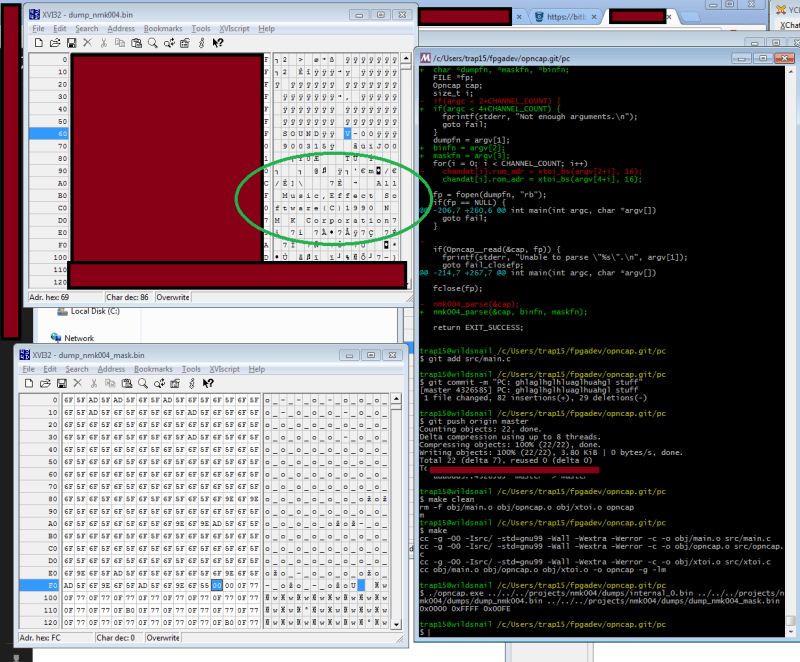
The full story is a bit long and contains several twists and turns, but its well worth the read. The condensed version is that after a lot of trial and error and after writing many custom tools, [trap15] was able to finally dump the ROM. He was able to accomplish this using a very clever trick, speculated by others but never before attempted on this hardware. [trap15] exploited a vulnerability found in the unprotected external ROM in order to trick the system into playing back the protected internal ROM as though it were the sound data stored on the EEPROM. The system would read through the internal ROM as though it were a song and play it out through the speakers. [trap15] recorded the resulting audio back into his PC as a WAV file. He then had to write a custom tool to decode the WAV file back into usable data.
[trap15] has released all of his tools with documentation so other hackers can use them for their own adventures into hardware hacking. The project was a long time in the making and it’s a great example of reverse engineering and perseverance.
[Thanks Ryan]













Man discovers MAME, news at 11
Read comprehension. Do you have it?
lenolee learns how to RTFA, news at 11!
This is actually a BFD to the MAME community and much praise should be heaped upon [trap15]
Carefull linolee there are special defences against trolls round here. http://hackaday.com/2010/12/19/hackaday-unleashes-a-troll-sniffing-rat/
Ha! You can still see that thing hanging around in my shop. I should think of some new features and do a rev2.
NFC reader, and multiple hammers supplied with tags (ban-hammer, remove-hammer, open-in-browser hammer)?
nice
Wow this reminds me of one of the few programs I ever wrote. Mine was even laid out just like this one is, with the hex on the one side and ASCII on the other. Mine was a RAM dumping utility too. I wrote mine in assembler. It was like 14 pages long. Mine was only a terminal application though, no fancy GUI. I did have a blue background with white characters I think they were? I can’t remember for sure, it was quite some time ago now. I thought it looked nicer than white on black at any rate.
But for all of the differences I can still see the similarities. I guess this is just how these memory dumping programs all look? My short lived programming career was cut short when one of the floppies that my assembler was on became corrupted, and I couldn’t reinstall it.
Shortly after that I became frustrated and started running Linux too. I never really got back into trying to program ever. I never felt as if I had any knack for it really. I don’t know, maybe no one really has a knack for programming, and everyone just muddles along with it, much like I felt I was doing. Well, I’m sure a select few have a genuine gift for programming, but I’m certainly not one of them.
To me programming is like a foreign language, and I’m not big on those either. When fscking computers learn to speak English then maybe I’ll try to program them again!
Fascinating. Who will be playing you in the movie version of this epic?
My god, what is up with all the trolls on this article?
Confirmed, there are a select few who are really good at it (John Carmack, Michael Abrash, even Linus Torvalds). Don’t feel bad about it, there are many people who write programs to make programming “easy” enough so others can pretend to be programmers (Python, Arduino, Ruby come to mind).
>who are really good at it (John Carmack, Michael Abrash, even Linus Torvalds).
I’m not sure comparing games programmers to an operating system (among other things) guy is really works.
There are people out their that do really nice stuff in ?insert managed language of choice here? but feel totally out of their comfort zone when they use a language that doesn’t free all the junk they allocate. Similarly I know a developer that works in C and assembler for microcontroller type stuff that just can’t get his head around anything higher level and ends up rewriting stuff that’s in the standard library because he isn’t used to having stuff like data collections implemented. Horses for courses.
I’m not sure what pcf11’s little story adds either way. He wrote something that shows hex and ASCII decodings of stuff.. that’s like um 100% of the tools out there for working with raw data like this.
He tricked the protected ROM to play it’s own program, captured the sound as a WAV file, then analysed the WAV file to decode the ROM contents?
Rick, you wrote it well, but I just had to repeat it to feel the awesomeness of what was done here.
WOW.
WOW.
And included his work log?
http://daifukkat.su/files/NMK004-WORK-NOTES.txt
Great job!
This. So much wow. I’m beyond impressed.
This chap deserves a HaD Oscar. Mind bogglingly awesome hack.
HACK
And how soon will this get rolled into MAME so these games can have better sound? Or did the company do something sneaky and use different protected code in the sound chip for each game?
Its already been added to MAME. Evidence is that the sound works in all the games that used this same sound chip, meaning the internal code is likely the same.
Truly. Epic. Hack.
This article has partially restored my faith in HaD.
“It’s beautifuuuul…”
OK, I admit I didn’t RTFA, but there is something I don’t get. The ability to convert WAV into original data must have included understanding how the chip was generating audio… but that’s what he was trying to learn? If he had WAV->binary converter, wouldn’t reversing it create a functional clone of the chip?
The external ROM contains data that controls the program in the internal ROM. The external ROM contains offsets that point to data that the internal ROM turns into sound.. but those offsets can be within the internal ROM so you can make it play itself. As long as you know what data creates what sounds you can analyse the output to work out what data created it and recover the ROM.
Wasn’t the GameBoy(Advance) internal ROM recovered in a similar way?
“A quick list of games that utilize this sound CPU:
USAAF Mustang
Uchuu Senkan Gomorrah (Bio-ship Paladin)
Vandyke
Black Heart
Acrobat Mission
Koutetsu Yousai Strahl
Thunder Dragon
Hacha Mecha Fighter
Choujikuu Yousai Macross
GunNail”
[trap15], you have mucho hacking, programming gonads! I bow to you in your awesomeness!
A very fun read though I did not understand much of how the hack was actually pulled together (probably because I am not very familiar with the details of the sound tables etc). Impressive hack though.
BTW: I used play Marvel vs Capcom on mame many years ago. I would only play occasionally and one day I realized mame would not play the game any longer. I guess one of the updates broke it and it could no longer play the rom. I tried reverting back to a few old version w/o much success but I guess I didn’t try very hard. I never managed to get it working again. Maybe I will try it again this weekend.
I recall seeing a list of unMAMEable games, that for one reason or another can’t be emulated. I wonder if that list will change now!
Would love to play Street Viper some day!
They just cracked another ‘biggie’ this week too, Raiden. That one was one of the more elusive ones. They also last year smashed MESS and MAME together. It has been paying very nice dividends. It really is the borg of emulation :)