CSL Dualcom, a popular maker of security systems in England, is disputing claims from [Cybergibbons] that their CS2300-R model is riddled with holes. The particular device in question is a communications link that sits in between an alarm system and their monitoring facility. Its job is to allow the two systems to talk to each other via internet, POT lines or cell towers. Needless to say, it has some heavy security features built in to prevent  tampering. It appears, however, that the security is not very secure. [Cybergibbons] methodically poked and prodded the bits and bytes of the CS2300-R until it gave up its secrets. It turns out that the encryption it uses is just a few baby steps beyond a basic Caesar Cipher.
tampering. It appears, however, that the security is not very secure. [Cybergibbons] methodically poked and prodded the bits and bytes of the CS2300-R until it gave up its secrets. It turns out that the encryption it uses is just a few baby steps beyond a basic Caesar Cipher.
A Caesar Cipher just shifts data by a numeric value. The value is the cipher key. For example, the code IBDLBEBZ is encrypted with a Caesar Cipher. It doesn’t take very much to see that a shift of “1” would reveal HACKADAY. This…is not security, and is equivalent to a TSA lock, if that. The CS2300-R takes the Caesar Cipher and modifies it so that the cipher key changes as you move down the data string. [Cybergibbons] was able to figure out how the key changed, which revealed, as he put it – ‘the keys to the kingdom’.
There’s a lot more to the story. Be sure to read his detailed report (pdf) and let us know what you think in the comments below.
We mentioned that CSL Dualcom is disputing the findings. Their response can be read here.










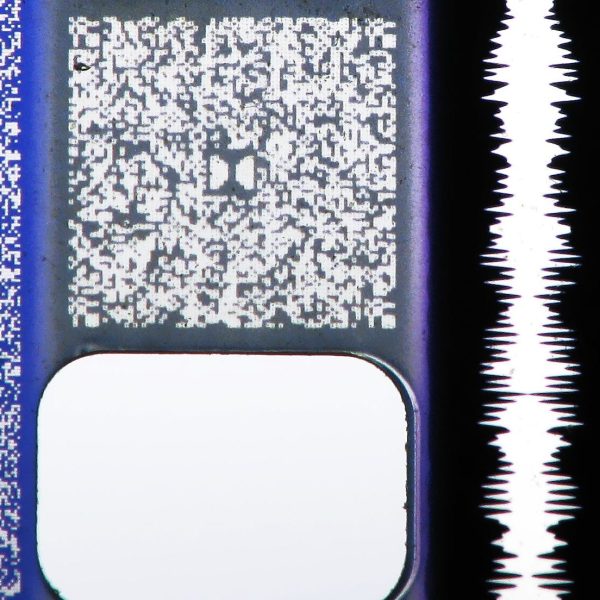




For those who cbf reading the response, i’ll give the TLDR
1. You need physical access to the MB to do these “hacks”
2. No vulnerabilities could be accessed via external means (PTS/GPRS)
3. This is a cheap device and is 6 years old.
Thanks for the comment.
1. I dispute that you need physical access. I needed physical access to carry out the reverse engineering, certainly. But after that, there are several attacks that can be carried out without physical access. Even not taking this into account, I suspect that you just need an image of the outside of the unit to substitute.
2. I dispute that as well. The IP side is external means, which they seem to totally ignore.
3. It’s the same price as all of their other devices. Plenty of 6 year old alarm systems are in place – they have a lifetime of ~10-15 years.
1. I dispute this. The reverse engineering was helped by having a device, many of the attacks don’t need access.
2. If you ignore the IP path, this is the case. And ignore that GPRS is no longer secure.
3. £200 isn’t cheap, and there is no evidence that they have changed anything for later devices.
Did you read the article? Cybergibbons highlights more than just vulnerabilities in the specific device, he highlights clear failings in CSL Dualcoms development processes and ability to take standards and security seriously.
The commenter is simply paraphrasing the response, not necessarily agreeing with any of those points.
If i understood the system and report correctly he did expose some security problems with the “alarm receiving server” too, Like the fact that some ports, including FTP, are open to the wwweb, and it does not have a whitelist of devices that are allowed to access the server. (Basically leaving them wildly exposed to a denial of service attack).
And your second point seems kinda wrong too, as he was able to alter the server IP by sending SMS commands using a default pin code used in most devices. Again, no whitelist for devices that would be allowed to use these remote-commands in the device.
Please read again before you post false information.
As someone working in the same industry too, i wonder if we should hire some external white hat hackers to take apart our systems too… (I must say tho that we seem to have a better grip at interface security than CSL Dualcom had implemented in theyr devices.) And no, i’m not going to announce our company name here ;)
Vigenère Cipher it is called if I’m not mistaken.
Hmmm…. don’t think CSL comes out of this smelling of Roses. Well done Cybergibbons. Fascinating read and expose.
I love that PCB. I see exactly *that* here in Hackaday.io often. Except when I see it here is a prototype. Not production like this picture.
Everything in the main PCB is hand solderable. There is 1.27mm SIOC chips, 0.8mm chips. The PCB has 10mil or greater tracks with plenty of spacing. And the high density (hard to solder) stuff is on modules.
Love it!
More power to those who like to use modules.
That’s thing about modules, sometimes ‘group buying’ modules is cheaper.
Unless you are producing very large volumes, you can buy Arduino Leonardos cheaper than ATmega32u4 for example. You can also use Arduino Leonardos across several product lines.
A single Mega32U4 is $5 at a random source. The Arduino goes for $20.
Price for the chip drops below $3.50 at farnell at 500+ (which is usually expensive).
Wondering how you are beating that with your $20 Arduino…
… ever heard of compatible designs from china? Arduino Uno incl. shipping $2.60?
The PCB looks like most production electronics that don’t need to be disposable or incredibly small. Nothing wrong wiht making a product repairable.
It’s not “hard to solder stuff is on modules”. It’s “GSM/GPRS modem is on module, because we don’t want to deal with FCC stuff too much”