Samy Kamkar is well known for many things, but lately it has been his hardware security hacks that have been turning heads. The nice thing to know is that, despite not having a background in hardware, Samy is able to run with the best of hardware researchers. At the Hackaday SuperConference he offered words of advice for anyone trying to walk the path of discovery with an exciting new piece of electronics. One might say it’s a crash-course in how to be a hardware hacker.
Low-Cost Exploitation Tools
Samy’s first bit of advice is to do the research. There is a ton of freely available information out there — the first place to look is the piece of hardware you already hold in your hand. Take it apart, tear it down, find out how it works, and start learning about the parts that you don’t understand.
Google is your friend, helping discover the work of others so you can build upon their efforts. Patent searches are a great way to figure out how a device works. Also incredibly useful are FCC filings which are available for pretty much anything that has a radio inside of it. Sometimes you will find entire schematics and communication schemes as part of that filing. With that information in hand, use simple tools to sniff the wireless.
When it comes to tools, Samy’s not hoarding unicorns in his toolbox. One of his favorite go-to’s is Arduino. When that’s too small or too slow he grabs a Teensy, and he may reach for an FPGA but only for the rarest of exploits where incredibly fast timing is needed. No, he pretty much uses the tools we’re all familiar with. On his workbench you’ll find a Saleae Logic Analyzer, DMM, Oscilloscope, and your basic soldering kit.
Where’s the Skill?
So if the tools are simple and widely available, how is it Samy can come up with such amazing hacks? I think he has well-tuned intuition about when he is following the right path for a problem. It seems his trick isn’t knowing everything, it’s know the right thing to go out and learn. This skill is displayed in a trio of very cool hacks he showed off during the talk.
CC Spoofing
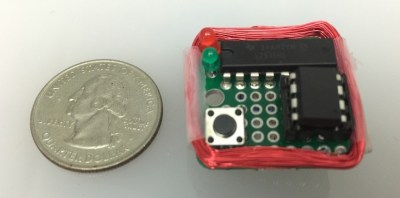 He built his own credit card mag-stripe out of a coil of wire and an ATtiny microcontroller — what he calls MagSpoof. How is that possible? His process started with exploring how a credit card actually works. He demonstrates dipping a card in iron oxide — the particles stick to the magnetic strip and you can actually read out the data with the naked eye. The leap here: if the stripe is magnetic can’t I just do it with a coil? The answer is yes. He built the coil, holds it up next to a stripe reader, and plays back the data. It’s interesting to hear that flipping a bit in your harvested stripe data means the reader will never ask you to use the chip reader.
He built his own credit card mag-stripe out of a coil of wire and an ATtiny microcontroller — what he calls MagSpoof. How is that possible? His process started with exploring how a credit card actually works. He demonstrates dipping a card in iron oxide — the particles stick to the magnetic strip and you can actually read out the data with the naked eye. The leap here: if the stripe is magnetic can’t I just do it with a coil? The answer is yes. He built the coil, holds it up next to a stripe reader, and plays back the data. It’s interesting to hear that flipping a bit in your harvested stripe data means the reader will never ask you to use the chip reader.
Fixed Codes and Rolling Codes
Two slightly related hacks are those to spoof garage door openers and automotive key fobs. Garage door openers generally have a fixed code (set by DIP switches) that is always broadcast from the remote to the receiver. It’s easy to imagine how to capture and play back this code. Samy wanted to do it without the capture. There aren’t that many combinations and it can be brute-forced in about 30 minutes. He further reduced that to three minutes by removing the waits between transmission. But it was a dive into the De Bruijn sequence that let him crack any fixed-code garage door in eight seconds! This one is called OpenSesame and uses the IM-ME children’s toy that has been seen around here doing a lot of wireless spoofing.
Vehicles are more robust. Key fobs use rolling code sequences that you can’t just capture and reuse and you certainly can’t brute force. The trick is to jam the receiver while you capture the code from the transmitter. Do this two times and you have two good codes — the first you can then actually transmit to unlock the car which the user thinks is normal behavior. In reality, you have a device magnetically attached to the vehicle that is always one code behind the most current. When the attacker wants entry to the vehicle the button on this device is all it takes.
This last attack was accomplished with a Teensy 3.1 and two CC1101 boards connected on a breadboard. That’s incredible! All of this serves as a roadmap to learn about the underlying technology that stitches our world together. The hope is that Samy’s talk, and the hardware security hacks that he uncovers in his work, will inspire the next generations of engineers to build better and safer systems, and the next generation of security researchers to find the new holes.
















I think he does niche stuff like gaming console hackers he just finds the stuff with weak or no counter-measures. Magstripes you can put a hall sensor in place of any mic element on any RF transmitter circuit and have a wireless skimmer.. There’s no security.
If you look on his site it’s also like a SEO page for low-hanging-fruit in computer security.. “OwnStar: Locates, Unlocks, Remote Starts GM/OnStar Cars” it has to log the app net-stream.. For example..
He used mathematics to improve the speed of an existing garage door hack, and has setup that maintains access with a key fob hack. Is physical security important?
This is the weakest comment I think I’ve ever seen in all the Hackaday shit comments. Well done!
Hahaha BarryFnGibbs hilarious…..
There’s no doubt Kamkar is a smart man