Every day, we see people building things. Sometimes, useful things. Very rarely, this thing becomes a product, but even then we don’t hear much about the ins and outs of manufacturing a bunch of these things or the economics of actually selling them. This past weekend at Shmoocon, [Conor Patrick] gave the crowd the inside scoop on selling a few hundred two factor authentication tokens. What started as a hobby is now a legitimate business, thanks to good engineering and abusing Amazon’s distribution program.
The product in question is the U2F Zero, an open source U2F token for two-factor authentication. It’s built around the Atmel/Microchip ATECC508A crypto chip and is, by all accounts, secure enough. It’s also cheap at about $0.70 a piece, and the entire build comes to about $3 USD. All of this is hardware, and should be extremely familiar to the regular Hackaday reader. This isn’t the focus of [Conor]’s talk though. The real challenge is how to manufacture and sell these U2F dongles, a topic we looked in on back in September.
The circuit for this U2F key is basically just a crypto chip and a USB microcontroller, each of which needs to be programmed separately and ideally securely. The private key isn’t something [Conor] wants to give to an assembly house, which means he’s programming all these devices himself.
For a run of 1100 units, [Conor] spent $350 on PCB, $3600 for components and assembly, $190 on shipping and tariffs from China, and an additional $500 for packaging on Amazon. That last bit pushed the final price of the U2F key up nearly 30%, and packaging is something you have to watch if you ever want to sell things of your own.
For distribution, [Conor] chose Fulfillment By Amazon. This is fantastically cheap if you’re selling a product that already exists, but of course, [Conor]’s U2F Zero wasn’t already on Amazon. A new product needs brand approval, and Amazon would not initially recognize the U2F Zero brand. The solution to this was for [Conor] to send a letter to himself allowing him to use the U2F Zero brand and forward that letter to the automated Amazon brand bot. Is that stupid? Yes. Did it work? Also yes.
Sales were quiet until [Conor] submitted a tip to Hacker News and sold about 70 U2F Zeros in a day. After that, sales remained relatively steady. The U2F Zero is now a legitimate product. Even though [Conor] isn’t going to get rich by selling a dozen or so U2F keys a day, it’s still an amazing learning experience and we’re glad to have sat in on his story of bootstrapping a product, if only for the great tip on getting around Amazon’s fulfillment policies.

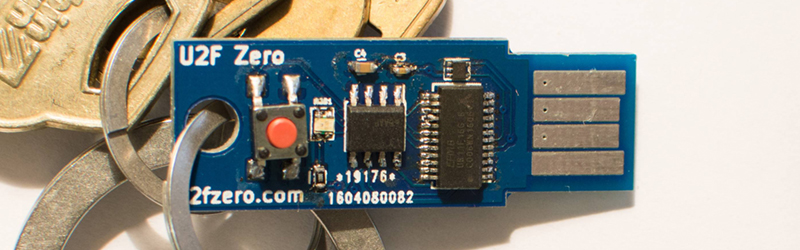












I don’t want to downplay Connor’s fantastic work, or incur the wrath of Benchoff… But GOD DAMN that is some horrendous soldering!
I really hope they didn’t go out like that
The rest of them look much better than the title image.
https://conorpp.com/designing-and-producing-2fa-tokens-to-sell-on-amazon
Looks like the soldering from some $3 buck boosts from china I ordered, 1/2 of them were incorrectly assembled and the others were just messy 1 had the HS floating about.
This is fantastic, the hand-soldering is a bit sketchy, but I think if it was available as a kit I would take pride in putting it together myself.
Would there be much benefit in potting the whole lot?
at least the CC508?
I think he would benefit from diversifying and creating a similar product with more features at an inflated price.
On the amazon he says to stay away from SMS based backups. Is this justified?
I’d be more concerned about call backups given the recent spate of having call forwarding redirect your voice backups.
Yes.
The primary risk is someone walking into a franchise store of whatever telco you use, and convincing them (money, social engineering) that “you’ve” (ie. they) have lost the SIM. They reissue a new SIM, and presto, the SMS goes to them.
In Australia, the telcos reminded the banks a couple of years ago that they were not going to be held responsible for any financial losses due to this. In their opinion – rightly, IMO – the banks were actually pushing a business cost onto them. They engineered authentication for SIM replacement against a threat model which didn’t include the potential for huge financial loss. If the banks were making an assumption otherwise, then they took the risk.
Yes, this attack has been practically mounted.
He had to write a letter to himself as to sell it as the brand owner the product needed the brand printed on it. Writing the letter meant that he could sell it on behalf of himself.
Sorry, the packaging needed it printing on…
If you can acces to the I/O data line of the crypto chip , does security is still guaranteed ? Oo
Yes. Disclosure: I work for the group that made this chip.
I’d say it isn’t much more secure than a piece of paper with a complicated password written on it.
The security isn’t that you can’t reverse engineer the chip and extract the password, but rather that you need to get your hands on it in order to do that.
I played around with a few of these chips, and read the datasheet. It is more like the chip plays a game of confirm/deny when presented with a public key. Any priv keys are hidden behind a fuse.
You’re forgetting that since it can’t be copied if you are in possession of the key you know no one else is.
A keylogger can’t steal it, nor can loss of your password database.
And if it’s missing you immediately cancel it.
Its more secure than paper as U2F checks the URL before authentication happens. It then can optionally sign the TLS session so even if DNS was compromised, the remote end will see it as a bad signature if there is someone in the middle.
I looked at Amazon for selling one of my products and the prices the tool was quoting me were terrible. Want to sell something for $14? They’ll pay you $5.42 per unit. “Ok,” I think, “that’s fine, I’ll do fulfillment myself to save more money.” Now Amazon quotes $5.65 for it.
I must have done something wrong though, because in Conor’s case above, the cost per unit comes to $4.22, and they’re selling for $8. He would either have to lose money or he’s getting a much better price than I was quoted.
I see the reference to “Small and Light” on his post now. I’ll have to check it out.
Not to forget the astronomical costs one has to calculate in when trying to sell hardware (or even directly imported goods, “directly” meaning: from outside the E.U.) – e.g. for waste disposal (both of packaging and electronic goods). That can easily put the retail price at four times the figures mentioned in this post, if one would calculate on the number of sales quoted. If not higher.
This is, if you play by the rules (law). If you don’t – like most Chinese-goods-importers do, basically destroying the market for those who want to play fair – then the numbers may fit.
… obviously I am talking about “import into the E.U.” and “selling hardware in the E.U.”, where “hardware” refers to self-made stuff.
Tin pads should never be used for USB contacts. Tin is harder than gold, and will cause fretting of the gold plating on your PC’s USB connectors. One issue with this is the generation of foreign object debris (FOD) inside the connector, which can short pins together. Another issue is that it can expose the nickel layer that sits under the gold. The tin-nickel junction will then be susceptible to corrosion, which can easily degrade your signal performance.
If you absolutely must, then it would be a good idea to use a sacrificial male-female USB cable between.
The connector company TE has a great application note on the subject:
http://www.te.com/documentation/whitepapers/pdf/aurulrep.pdf
Side note: If you ever want to see someone give you a shitty look, walk over to your RF engineer’s desk and hook something up to their $50,000 oscilloscope by sticking a resistor lead into the BNC connector.
Also forgot to mention- ENIG is not the best idea either for contacts. The gold layer is just thick enough to extend the shelf-life of the pcb prior to assembly. The first connector mating will scratch away the thin gold layer and expose the materials underneath.
(Not trying to sound negative- it’s just that there’s a lot more to connector selection than most people are aware of.)
Starting with an absolute statement, you started to come across as being negative, but then you backed up your statement and explained it well. This is actually good information to share with this community, and I thank you for it.
Thanks, good to know
I do love hackaday, great SNR on the comments :-)
I tend to tin the contacts when I make PCB usb plugs. That solve the issue?
I’m afraid not- The contacts on the inside of the USB receptacle in your PC will still have gold contacts, so you’ll still be mating tin with gold. You would either need to change the USB connector in your PC to tin-plated (not sure if those even exist for USB connectors), change the USB contacts on the board to hard-gold plated, or use a USB plug on the board instead.
Using a sacrificial USB extension cable would probably be the easiest solution though.
its a shame you can’t get these via european amazon.
Is there a recording of this talk somewhere?
There will be in 6 months or so.
That really puts some emphasis on how much better the CCC conferences are in terms of making good recordings available.
Maybe the Shmoo people could have used some of their major sponsorship money from the 0-day exploit vendor Zerodium for this.