Friday saw what looked like the most dangerous ransomware infection to date. The infection known as WannaCry was closing down vital hospital IT systems across the UK canceling major operations and putting lives at risk.
Spread Halted?
It spread further around the world and almost became a global pandemic. Although machines are still encrypted demanding Bitcoin, one security blogger [MalwareTech] halted the ransomware by accident. As he was analyzing the code he noticed that the malware kept trying to connect to an unregistered domain name “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com”. So he decided to register the domain to see if he could get some analytics or any information the worm was trying to send home. Instead much to his surprise, this halted the spread of the ransomware. Originally he thought this was some kind of kill switch but after further analysis, it became clear that this was a test hard-coded into the malware which was supposed to detect if it was running in a virtual machine. So by registering the domain name, the ransomware has stopped spreading as it thinks the internet is a giant virtual machine.
Why was the UK’s NHS Hit So Badly?
According to the [BBC] Information obtained by software firm Citrix under Freedom of Information laws in December suggest up to 90% of NHS trusts were still using Windows XP, However NHS Digital says it is a “much smaller number”. Microsoft has rolled out a free security update to Windows XP, Windows 8, and Windows Server 2003 “to protect their customers”. There was much warning about XP no longer receiving updates etc, the 2001 operating system just needs to die however so many programs especially embedded devices rely upon the fact that the OS running is Windows XP, This is a problem that needs sorted sooner rather than later. There is still obvious problems facing the NHS as all outpatients appointment’s have been canceled at London’s Barts Health NHS Trust which happens to be the largest in the country. However [Amber Rudd], Home Secretary, said 97% of NHS trusts were “working as normal” and there was no evidence patient data was affected. Let’s just hope they update their systems and get back to fixing people as soon as they can.
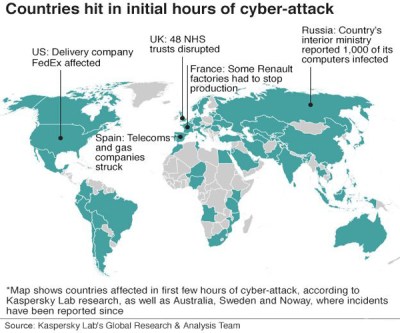
Where Else Was Hit?
There was quite a few other places hit as well as the UK’s NHS including The Sunderland Nissan Plant also in the UK, Spanish telecoms giant Telefonica along with some gas companies in Spain. In the US FedEx was affected, France has seen production in some of it’s Renault factories halted. Finally, Russia reported 1000 governmental computer systems has been hit.
So is this the end for ransomware?
No, this infection was stopped by accident the infected are either still infected or have paid up, had they not included the sloppy code in the first place then who knows what would have happened. Microsoft had rolled out patches but some people/organizations/Governments are lazy and don’t bother to apply them. Keep your computers up to date, Good luck because we think we will be seeing a lot more ransomware malware in the coming years.
[Update WannaCry v. 2.0 has been released without the “kill switch”, We wonder what will happen now. Probably not a lot as the media attention has been quite intense so it may not be that big an infection however there is always a few who live in the land where news doesn’t exist and will go a long their day until BAM! Ransom Ware installed and pockets emptied.]















Disabling the Windows file encryption service is not a bad thing to do in general as added insurance.
That’s probably the best single thing you could do other than keep up to date.
How would it help though? I mean, nothing stops the malware from implementing encryption by itself and simply crawling the filesystem and encrypting it “by hand”.
I think it would help until everyone started doing it, but as that isn’t going to happen I think it might be useful even if it is bypassed.
Its really a numbers game, if they hit .02% infection rate they make a lot of money. Heh, imagine devaluing the ransom market if decrypt didn’t work flawlessly, I.E. they got the reputation as a whole that paying won’t get your files back either.
It’s been reported that the perpetrators have made $26,000 so far. Not my idea of a princely sum. And now they got half the planet’s law enforcement and intelligence services hot on their trail.
I think the solution to this is a mandatory death penalty for anyone convicted of spreading malware of any kind. Make it international law, after a few hackers are executed the rest will decide it’s not worth the risk.
An air gapped USB drive with a current image file of your internal drive(s) is the best insurance.
comradewhoopie. The perpetrators have risen to near $100,000 :(
your execution idea would just be abused, it would be way to easy to make you look like the culprit, on the other hand hitmen would have a field day.
The ones we have seen here all used the Windows service, they could certainly run their own encryption if they want to go to all of that trouble for not a lot more benefit. Also comes with all of the testing across LANs and that it will actually decrypt network mounted drives correctly and play nice with the security in MS such as it is. Like I said, just some added insurance.
Now they want to blame the XP machines, and complain the NHS should have spent the money to buy Microsoft´s newest, shiniest and buggiest OS. The number of win7, win8, 8.1, 10 machines infected shows the blame lies not with the XP machines, but in the security of the networks compromised, in people´s lack of care when using work computers to browse the net, and also in MS confuse patch policy. Now, with the latest rollups bug (is it really ? or was it intended ? ) that disable security updates for some AMD and Intel processors that MS says should be running only win10, that seems even worse.
tl;dr: MS “ecosystem” is rubbish. Stay away from it.
Can’t be helped when it’s offered on every machine for tom, dick and harry’s to buy.
Linux is never sold because it’s advertised as “a difficult system” and “you can run microsoft software on it.”
The lazy tom, dick and harry’s won’t go out looking for alt software or other methods to run the software when they can pick up a machine that just runs it without fiddling.
Yah it’s pretty bad and seems to only be getting worse.
I describe Microsoft’s approach to security as trying to turn a colander into a bowl by applying band-aids to all the holes.
It exploited a bug for which MS provided a patch in March. Labelled as critical and RCE.
The blame lies solely with the IT department who didn’t apply the patches.
I get that patching is hard, and risky.
But with such a wormable exploit it’s only a matter of time before abuse is widespread.
We got off lightly this time that the malware had a killswitch or shot sighted anti-VM system. I guarantee you there are copies of this malware out there now without that killswitch.
Why was this article so sloppily written? Missing punctuation, bad grammar. I am no language nazi by any means, but there is a limit. In other words, if I am getting bugged by it, it is pretty bad.
It’s wear what you want to work today at HackaDay, I woke a chicken costume, I had to peck each key on the keyboard because wings don’t have fingers, any way think I done brilliantly.
At least you have all of your fingers. http://hackaday.com/2014/08/27/bils-quest-for-a-lost-finger-episode-i/
>:)
Do you ever suffer from phantom limb? I’ve always been interested in that. and R.I.P Bil’s finger,
Yeah I have woken up because I can’t scratch the part that is missing or there is a nasty pain about an inch past where the finger stops. Since I tore it off instead of cut it off the nerves were all stretched and are all jumbled with scar tissue. At least I did it late in life. >:)
Bil, you should DEFINITELY Google ‘phantom pain mirror therapy’. Here’s a good intro: http://www.physio-pedia.com/Mirror_Therapy
Sorry can’t reply to that comment but it sounds crazy trying to scratch something that isn’t there, It’s kind of a shame I think in the next 50 years we will be growing body parts in a lab like fingers arms etc. Hope it doesn’t give you too much trouble.
I wanted to get a prosthetic that was useful, maybe a combination Bluetooth™, Laser Pointer, Salad Fork kind of thing.
ROFL @ [Bil Herd]
Kind of like the Swiss knife of prosthetics.
I spose you could fit enough lippo battery in there to do something.
Hmmm… Perhaps a (cough)”Joy Buzzer” that’s switched on by darkness and lowered external resistance (dampness) reading?
Just wanted to point out that this conversation is the best author-made response to criticism I’ve ever read on HAD *happy grin*
Where’s part two?
It’d be a awesome lace to have a secret compartment. Plenty of space for a roll of microfilm or two. Or a microsd card if you’re not feeling retro.
LOL, That’s the best response to that suggestion that I have read.
I can’t agree more.
The NHS had a contract with Microsoft to maintain and secure the aging XP machines (needed because of software and other hardware dependencies, not just because of the costs of replacement). The current government didn’t renew the Microsoft contract – as a cost saving exercise.
I’m waiting for the responsible politician to say that it was a sure fire cost saving exercise and it is not his fault that it didn’t work.
yes, and I’m waiting for MS’ “total cost of ownership analysis”.
Now I am waiting for the Tories to come out and say: “See, we told you that the NHS is badly run, we need to privatise it, in order to make it work!”
Or something in the same tone….
Stick EVERYTHING in the cloud. Make it someone elses problem.
I understand a certain Theresa May was the person in charge of that very decision to not pay for the security updates before she was prime minister. Will she be held to account?
Imagine living in a country run by her.
Unfortunately I do.
It’s odd that the article author isn’t aware that governments all over the world pay MS for continued XP support/patches.
And interesting to hear the UK decided to not pay while continuing to use XP, I wonder how they rationalized that.
Someone probably pointed out the amazing cost savings and all the additional money they would be able to invest in the NHS as a result B)
Oh wait.
So why do they need to saves costs? I thought nationalizes healthcare brought better service at reduced costs?
I was going to say it is time to move these systems to open source, but if the people responsible for them don´t fix the bugs, or don´t apply the patches, the (bad) end result really would be no different.
CyberReason RansomFree. its free, updated often, and effective. https://ransomfree.cybereason.com
You kind’a sound like an AD ;)
Do you work for them (whoever they may be)?
I do not. I just use it myself and have found it to be effective.
“behavior analysis” so, its a standard off-the shelf anti-virus software.
Not exactly. It is not a full AV suite by any means. It is targeted at detecting encryption behavior on dummy files that are placed in various places on your drives. When it detects something funny happening to those files it will among other things, kill related processes. Im sure its not perfect, but hard to beat the price.
Please spare us the “XP have to die” bullshit. Had the computers run Win 7 or 8 the result would be the same. And I am looking forward to the horrible vulnerabilities that yet have to be discovered in the 20 GB pile of sh*t called Win 10.
well XP needs to die, no bullshit. the update was released March 14 dor windows versions including windows 7. Even if you skipped the last TWO patch tuesdays you would be safe on windows 7. If you would be on Linux and a gaping hole security breach would be in Linux administrators would patch within no-time (heartbleed had virtually no impact and not a single affected system is online).
Patch management and EOL management of systems seems quite hard.
So, the only difference in the case is that M$ decided not to release patches for one of the three OS in question. Sorry, but I cannot agree that XP is by any means worse than the newer Win versions. M$ is just deliberately killing it by stopping security updates and support, but if they did the same for Win 10, 8 or 7, these would be equally “bad”.
well, considering the NHS specifically had a contract to support a [dead] OS that doesn’t automatically receive security updates, yes, part of the blame lies on the person who decided to keep using it.
Ditto to the person who decided to stop paying that contract as a cost-cutting measure.
if had been a Win 7 – or 8 install, you wouldn’t have to keep paying a contract for the security updates to work.
Windows 10 would have been a marketing failure if they didn’t force it.
It probably would have been less harmful for them to have just thrown the entire Window 10 and Cortana code into the trash and fire or demote all the key people behind the concept and called it a loss.
No. Win7/Win8 would only be affected IF there was a XP/2000/Server 2003 machine on the same network. The worm used a SMBv1 exploit to spread to these machines and from there beyond. SMB got to v2 on Win7 and v3 on Win10/Server 2016. For compatibility they go down to v1 when chatting with those older systems, so yes, killing XP/Server 2003 as Microsoft pointed out would stop the infection, only the first computer, infected by user behavior, not an exploit, would be encrypted.
All of my Linux systems did not notice the attack ;-).. WHY?
Must not have had wine installed. This shit works perfectly in wine.
Install wine> write custom code to get affected portion of registry to run > tie in linux file access so it can encrypt the files> shake fist angrily at microsoft>???>profit!
Given the Chinese dominance over bitcoin it would be easy to force the criminal underworld to hand over the people responsible for the attack, just put a temporary ban on all bitcoin operations, and if all of the other badly hit countries did the same… But the Chinese have the particular advantage of being able to kill or torture people that don’t do as they are told, so their ban would be much more effective. In fact they could say that if the machines are not encrypted in x days they will implement the ban and not lift it until the people responsible are in custody, that way there is no ban unless it is really needed and the criminal have a chance of fixing things before they spoil the game for everyone else and end up “dead men walking”.
…are not dencrypted in x days…
“decrypted” ;)
Yeah, LOL, had a lot going on earlier, it’s a mad house here some days and I can’t here myself think. Anyhoo you get the idea.
Then again if it was the NK government that deployed the malware other methods will be required, and it was an act of war.
http://www.abc.net.au/news/2017-05-16/researchers-link-wannacry-to-north-korea/8531110
If man can make it, man can unmake it. Place your securities and well being in an environment of known instability and negative consequences are inevitable. There has been this blindly fast paced purge of tangible for invisible while the technology is being developed rather than evolved — as technology has grown, people have demonstrated their inability to be responsible with in the spectrum of automation and until there is an equilibrium of the two in the future, I shall sit back and enjoy people succumbing to the whims of enemies. So concludes my lecture — go on with you.
Let us not forget that the NSA has known of this flaw for quite some time, but chose not to inform the vendor. Of course, they take their direction from politicians, so ultimately the US congress needs to grow up, be the adult, and tell the NSA to stop playing this dangerous game. I don’t recommend holding your breath waiting for that to happen…
Microsoft and all the others who have these exploits which the NSA discovered, and the info was stolen from the NSA, need to be told about those exploits by the NSA so they can be fixed.
The NSA will just have to work harder to spy on people. The S in their TLA is for Security, the Security of the United States. If giving up a bunch of the back doors they’ve been hanging onto for potential spying on possible and known enemies of the USA is part of the price for enhancing the security of the USA, then that’s what they should do.
Till one realizes that “price” is really bad people (of the head-cutting variety) getting away. The people howl about that because despite all their rhetoric, they don’t like to die.
Exactly! I’m quite disappointed not seeing any news so far about this topic where the NSA is at least partially blamed.
It’s the definition of why the shady underground business of trading and hording ‘secret’ 0-Days is generally bad and should be made illegal immediately.
If the NSA had informed M$ about these bugs before they became public probably none of the current mayhem would have happened.
Microsoft patched the bug in March. 2 months ago…
The NSA being tasked with both to secure American computer systems, and break into enemy computer systems, has conflicting missions. The agency needs to be split in 2 so those roles are filled by different agencies.
NSA/CIA/FBI control political figureheads, since they collect dirt on every one of them (and us). Cart is actually controlling the horse.
This is why 18th century Americans put privacy protections in the US Constitution. But plebs today is weak, and it is easy to keep them distracted with “bread and circuses”.
Maybe all this is inevitable and just human nature. After all, sht always floats to the top.
Not explicitly, which is the problem.
The particular strain of virus has been halted. There is nothing stopping the author from releasing a version that has no killswitch.
They already have.
NHS should switch to Linux + WINE. :)
It works in wine.
https://twitter.com/hackerfantastic/status/863359375787925505
But why did connecting to iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com mean that it was in a virtual machine?
It is similar to how some games attempt to write to an invalid or read-only memory block. If it actually writes, than the game is running in an emulator.
iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea is random enough to be 99.9999999…% sure that it wouldn’t exist anytime soon in the wild, luckily or brilliantly someone tried it out. (Thanks. +1 [MalwareTech])
The few a-holes that created this attack probably have this domain on their network so they don’t infect themselves. Or something like that.
The whois is a little amusing.
because the creator but “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com” in his (VMs) host-file to keep himself from being infected or to test it without it’s self spreading functions.
They didn’t, this was obviously an act of cyber terrorism carried out against the UK government by Welsh separatists. Source: I am Welsh and grew up in Iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea. I know how some of these guys think.
I so want to upvote this post!
It does indeed look like a Welsh word. Then I realised there are too many vowels.
So swedish?
More likely it was an (odd) test to see if you are behind a captive portal. As generally, all domains resolve then.
Isn’t this old news, I thought that there was a new strain in the Wilde with the killswitch domain removed.
Awesome. Looks like my XP system is safe again!
LMAO! +1
Hasn’t anyone noticed that this guy took a big risk registering the domain? It could have been a switch that make the virus do even more damage. Is there any mention of whether he sandboxed it and tested the domain first?
How could it have caused more damage?
Send itself to more people than usual? Harder encryption? Ask for more money? Fry the video card?…
I thought it was a risk, unless he had tested it by creating a host entry or making a domain in the local DNS server first as once the domain was created it would have taken a lot of working with the DNS industry to make it stop showing up as registered.
For example it could have deleted the files or deleted the encryption keys was what came to mind
I accidentally reported your comment just now! Sorry about that, presumably the hackaday staff will notice it was an accident.
Anyway, I meant to hit reply and say that he did at first think that he might have triggered something in the virus:
“After about 5 minutes the employee came back with the news that the registration of the domain had triggered the ransomware meaning we’d encrypted everyone’s files (don’t worry, this was later proven to not be the case), but it still caused quite a bit of panic.”
( https://www.malwaretech.com/2017/05/how-to-accidentally-stop-a-global-cyber-attacks.html )
It’s not inconceivable that a ransom-ware author might hold something back (not ransom 100% of infected computers maybe) until it becomes obvious that somebody is trying to reverse engineer the code– by registering obscure domains from the source code for example. It could deter white hats poking around I guess.
To find out if a bear is sleeping, you poke it?
Works every time.
What was stupid was letting out exactly how it was stopped. The next one won’t have such a killswitch left in. “When your enemy is making a grave error, do not interfere.”
I remember back before there were computer viruses. Upon reading one of the earliest magazine articles discussing the possibility of programs that could modify other programs in order to spread themselves, and the kids of nasty things that might be possible. My thought was “You idiots! Don’t give people ideas like this!”. It wasn’t long after those first articles about the possibility of computer “viruses” were printed that the very first network worm was unleashed.
This, so stupid. WHY would they help this guy debug his code?
You really think the original ransomware author won’t be able to discover why suddenly his virus is not working anymore?
security through obscurity has never and will never work, even before the internet info got out.
someone explain to me how a DNS lookup is supposed to determine if it is running in a VM ?
let me answer my own question, it was in the malwaretech article :
“In certain sandbox environments traffic is intercepted by replying to all URL lookups with an IP address belonging to the sandbox rather than the real IP address the URL points to, a side effect of this is if an unregistered domain is queried it will respond as it it were registered (which should never happen).
I believe they were trying to query an intentionally unregistered domain which would appear registered in certain sandbox environments, then once they see the domain responding, they know they’re in a sandbox the malware exits to prevent further analysis. “
The author(s) of this would have a local server with that URL, on a LAN not connected to the Internet. When they wanted to stop the worm during testing, they’d simply have to boot that up or plug it into the LAN. When the worm contacts that domain it would send a stop signal out to copies of itself across the network.
Same thing for the worm detecting if it’s running in a virtual machine. Run multiple VMs on one computer, all sharing network access through the ethernet controller, with one of them setup as a web server with the killswitch domain name. Start the worm on one VM and watch it spread, then launch the killswitch VM to stop it.
Any infected site that pulled the plug to disconnect from the internet and WWW would only have to reconnect after that domain was registered and in short order the worm would stop spreading on their network, either by self-stopping when finding the killswitch domain name or by receiving a stop signal from another infected computer that had found it.
It’s like the bacteria that took down the Martian invaders in “War of the Worlds”.
It is surprising that the author(s) left that in. Perhaps they have read the list of inventors killed by their own inventions? Wouldn’t want to get their computers hit by their own worm.
no, it was actually a badly implemented check to see if it was running in a VM. (eg. being analyzed)
from the article :
“This technique isn’t unprecedented and is actually used by the Necurs trojan (they will query 5 totally random domains and if they all return the same IP, it will exit); however, because WannaCrypt used a single hardcoded domain, my registartion of it caused all infections globally to believe they were inside a sandbox and exit…”
What I read was that the registering of the domain was all it took, it didn’t say anything about resolving or functioning (I.E. A records or absence of NX Domain), just registered. I am not saying there was more to it, that’s just what I read.
If that’s the case the domain could have been faked with hosts files or creating a zone for the domain in the local DNS server, In this case then I don’t think a VM needs to run for the DNS to look modified.
looking at the researcher’s LIVE attack map, that visualizes the DNS queries, the worm is still spreading in china, surely they would have opened their great firewall to this domain name by now ?!
https://intel.malwaretech.com/WannaCrypt.html
It apparently is open. That’s where the map data is coming from.
the trouble is than – aside form (the lack) of security – XP is a perfectly usable system for much of the worlds users, and many many people don’t want (or can afford) to have to upgrade their whole machine to go to the latest bloatware from MS.. And that’s without even considering the problem of getting all their programs working, and also having to worry about MS keeping tabs on everything they do…
MS should still be selling XP, as well as providing security updates. Instead they have moved to bigger and bigger bloatware – that also reports back what you are doing… Why would a corporate want to spend millions to move to that?
You know of course that Apple happily refuses to provide updates for old OS/hw combos? If e.g. you want to run Lightroom, then you might well have to upgrade your hw because the newer versions won’t run on older MacOS. So hardly a MS issue, in fact MS is bending over backwards to keep the ancient stuff running for the inept organizations that still use XP. Not like the EOL policy isn’t published, it is just ignored because ‘bad things cant happed to me’ attitude. Negligence and bad decisions on the part of companies, not MS.
There has been lots of evidence that XP is in fact no longer a wise choice for anyone, you do read the news don’t you? I can understand ‘cant afford’ for individuals but ‘don’t want’ is an explicit decision to open yourself up to problems. So don’t cry when it happens because it will happen.
I think that his point is that some people prefer Win XP and that it is a perfectly sufficient system for them – I mean the look & feel, resource usage (e.g. disk space, memory and CPU requirements) etc. The fact, that M$ is forcing people to upgrade by stopping security updates is a completely different story.
The thing is most normal people view a computer and it’s operating system as just a tool. As such they assume that as long as the tool still works for them they shouldn’t have to buy a new one. This is in stark contrast to enthusiast and geeks who pride themselves in always having the latest and greatest. Think about it this way, If I buy a torque wrench and i take good care of it and it still works when I need it 10 years later, why should I be forced to buy a brand new one just because the manufacturer wants more of my money? That’s the way the average Joe sees it. It’s really the tech industry who’s out of touch with the real world and not the other way around.
Also, I 2 machines that I still runs XP on and they are even connected to the internet and I’ve yet to be infected by any viruses or malware of any kind. A lot of this has nothing to do with the operating system your running on your computer and everything to do with your computing habits and how security conscious you are. smart people don’t browse the net using their administrator account and with the browser security settings at the lowest level. They also don’t download and install just any piece of software on the net. That type of activity is where 99% of these problems come from.
A torque wrench is never likely to need upgrading/updating. A prime analogy would be analogue to digital radio/television…and should broadcasters continue to support old, analogue equipment even after they spent months/years informing people that there would be no analogue support after a certain date.
The average computer user just wants to press a button and get to the required web destination, or open that piece of email. Do you suggest that the old lady from Gardenia Crescent employs a techie every time that updates are on the horizon? The folk who create this kind of code are relying on the average user, not the cautious/aware IT techies; they rely on large organisations not having a tight patching process because of staff issues/budget restraints, etc.
I have no inherent love for microspasm but they HAVE informed people for a number of years that official support for older systems will be phased out. They are no different in this attitude than any other software developer: eventually it becomes more cost-efficient to cease spending time/resources on older versions of the OS.
I loved XP. And then they put out crap like Vista and the auto-download that Windws is now, sad.
That’s why I switched to Linux Mint. Now my XP resides in a virtual machine under Linux. It even runs faster than it did on my old computer. I don’t use it much, Linux has equivalent software that does everything and the few Windows programs I use run under WINE. I’m so glad I switched, when I read about all the problems Windows users are having, and being spied on, I know it was worth the effort to learn Linux.
Better solution, those users should just switch to linux and use wine, but they won’t because they can’t be bothered to learn something new, even if it’s free. The problem isn’t just being stingy, it’s laziness and resistance to change.
Well, actually there are people who want to do useful work on their desktop machines, and that won’t be happing with Linux. There isn’t even an equiv for MS Office that is worth using. Can’t run Lightroom, AutoCAD Inventor etc.
I do all my work under Ubuntu linux as a python coder and I’m so pleased with my coding rig. I don’t really care if your autodesk bloatware doesn’t work. You have OpenSCAD if you need to draw something to 3D print. Cheers bro!
The applications =I= use for serious useful work run natively on linux. That include libreoffice.
… and apparently dependencies on legacy hardware
https://twitter.com/hackerfantastic/status/863359375787925505/photo/1
XP with the kernel and underpinnings from 10 really the only good part of it minus all the telemetry malware would have actually been a good seller.
For any operation where confidentiality is needed bank,medical,and even cad/cam work the telemetry in 10 is unacceptable and I would not be surprised in the least if there are already viruses and malware that make use of the already installed spy services in windows 10.
Why the hell did everyone explain exactly why it was stopped in such explicit detail? why would you help the writer of the ransomware debug his code? why?
Because it would take not more then an hour to find out for the original developer.
Now how long until someone removes the url that’s holding back the flood.
> There was much warning about XP no longer receiving updates etc
Yeah, I don’t get it.
There were around 17 patches released for XP in January 2017.
Another 8 or so in March.
Around 35 the week before last… Count them!
And now this jobbie….
Microsoft still supports their best ever product, but they just don’t want to admit it.
Not officially they want everyone to move to 10 because they think they can make more money selling people’s personal information and making windows and it’s software a subscription.
Both things are very scummy and as shady as they come.
Ah the paid apple shill. Level one media or red river???
On the subject of updating:As I pointed out in the other article, there were several instances of MS rolling out an update that completely disabled systems of big chunks of functionality like classes of peripherals, so it’s not ‘laziness’ that makes people not update, it’s the dread.
And it’s so universal I hear from people with absolute zero knowledge of tech that they disabled software updates on various software packages because of having been stung a few times.. (And Mozilla isn’t helping to not have that atmosphere BTW.)
Making them silent and not telling people what’s it’s for doesn’t exactly help with the trust situation.
I noticed that in recent days, there had been a big dose of those “I hate you…..” or the “Why are you sending me ……”
My junk Gmail acct used for Craigslist dealings.
They all seemed to be coming from a UK address and had the cliched “click here to see link” or “unsubscribe”, etc.
The email addresses usually have a gibberish looking string of characters in them.
After seeing what happened after [MalwareTech]registered that domain
Makes a person wonder a bit more, about what those gibberish looking mail identifiers could be calling up.
Hopefully no one is clicking anything in these.
Small BTW: Autopsy is for people. Necropsy is for things.
I know but it was a slight play on words since it was hospitals that felt most of the attack.
Everyone is worried about the wrong thing. Just find the guys and skullfuck them. The machines will keep propagating until the human operating them ceases to exist. Sheesh. Easy stuff folks. Drop a friggin kinetic rod on them already. Also, thanks wikileaks the infonazis that they are. You sure showed the NSA who is boss lmao. Nope just the hospital smh.
balls…
https://s3-eu-west-1.amazonaws.com/thelab.gr/uploads/monthly_2017_05/18556224_1593017024044302_8755365373935062913_n.jpg.adb0ce0d0a5b62bd5236097f3ae40412.jpg
Pay up or they Stuxnet your spin cycle?
So has the UK nuke sub fleet escaped infection?
When they catch the responsible parties, they should hang them up by their balls.
Our consulting engineer has Windows XP *embedded in* two spectrum analyzers that cost $80K each. I’m sure he doesn’t want to hear that XP “needs to die”.
I’m sure he doesn’t but for the greater good perhaps it would be for the best.
Today in researching firmware rootkits for my own knowledge and stumbled onto your page here… https://hackaday.com/2015/06/08/hard-drive-rootkit-is-frighteningly-persistent/
It seems “Malwaretech” was/is a trusted contributor to hackaday. As I subscribe to the idea that is anonymous, I support hackers for the most part and I’m 100% in favor of open source everything for obvious reasons. My reason for commenting here then, is this article is the most recent hackaday article that speaks of [Malwaretech] and i wanted to get hackaday’s take on the following article I happened to come across today in my searching, on Wired dot com.
url = https://www.wired.com/story/wannacry-malwaretech-arrest/
Indictment: https://www.documentcloud.org/documents/3912549-MalwareTechBlog-Indictment.html
As it seems [malwaretech] was arrested back in August for allegedly writing the Kronos banking trojan. I have yet to look further into the situation myself but as i stumbled into this completely randomly AND hackaday seems to be supportive of [malwaretech] (and the rest of us hacker types) I thought it prudent that hackaday perhaps make a statement or at least let us know what’s the skinny on this thing is. Revolution will NEVER be legal. Stay safe. And thanks ahead of time. Assuming someone from hackaday reviews article comments, I look forward your response and perhaps an article to speak to this in the future. ✌