For administering many computers at once, an IP KVM is an invaluable piece of equipment that makes it possible to get the job done over the network without having to haul a keyboard, monitor, and mouse around to each computer. The only downside is that they can get pricey, unless of course you can roll one out based on the Raspberry Pi and the PiKVM image for little more than the cost of the Pi itself.
The video linked below shows how to set all of this up, which involves flashing the image and then setting up the necessary hardware. The build shows an option for using HDMI over USB, but another option using the CSI bus would allow for control over options like video resolution and color that a USB HDMI dongle doesn’t allow for. It also makes it possible to restart the computer and do things like configure BIOS or boot from removable media, which is something that would be impossible with a remote desktop solution like VNC.
The creator of PiKVM was mentioned in a previous post about the creation of the CSI bus capture card, and a Pi hat based on this build will be available soon which would include options for ATX controls as well. Right now, though, it’s possible to build all of this on your own without the hat, and is part of what makes the Pi-KVM impressive, as well as its very low cost.















Assuming all the machines are network capable, why not use one or more instances of a remote desktop application? There’s no extra hardware involved. You would need a keyboard, mouse, and monitor just one time to setup each remote machine, afterwards it runs headless. Setup the remote desktop app(s) to start on boot, that way the remote connection will survive a reboot.
Until you need to make a BIOS change or log into single user mode after a failed kernel update/parameter change etc. I.e. all the times that you don’t get as far as to have the desktop up and running.
Or if the machine is unresponsive and need a janitors reset.
As he says in the video, this option let’s you access the bios remotely and mount CDs.
> Assuming all the machines are network capable
This is a wrong assumption. Some times you misconfigure the firewall, or delete the default route, or the network card driver update fails, the disk crashes, boot fails and drops to the recovery console… Lots of things will have the computer up but inaccessible.
This is not for a desktop computer, but for a server on a datacenter or server room. You don’t want to physically get there to reboot the server and change the firewall or route.
I was thinking “I wonder did they do the right thing and have a readonly filesystem in pikvm”, to extend the lifetime of the SSD to the maximum, and to my pleasant surprise one of the features is “The ready-made OS with read-only filesystem”.
It’s a cute idea, but I think it’s more economical to buy motherboards with IPMI in the first place, than to bolt something like this on to it.
I fully agree, but you would never place a IPMI directly on the Internet because the binary blob firmware is never updated as often as it should.
This is what VPNs are for.
I bought a server motherboard with IPMI. That IPMI was based on JAVA. So atm, i need to hassle with downgrading the web browser and accept a LOT of JAVA related exceptions. And even then, the IPMI is unreliable because of all the “hacks”.
So a cheap and update able external solution sound awesome for me.
That’s why we went with an IP KVM at my employer. Thankfully, since my employer is in a field where there is (usually) a good amount of money coming in, we can afford the shiny Raritan KVM units which run in excess of 10 thousand US rubles. (They are verra shiny, and worth it, though.)
To be honest I disagree, I have a server board with IPMI builtin however it’s old so it’s java based, this solution will allow someone to use a ryzen apu giving you great performance with a low TDP.+
You can also use an external hdmi kvm switch too which means you’d be able to control multiple servers over one pikvm.
Not to mention this allows for VNC.
Boards with actually good IPMI implementations are stupid expensive bespoke server boards.
Has anyone tried this with a ZeroW? You’d have to compile the OS according to the instructions. Curious how well it works with the smallest RPi.
It performs surprisingly well on the Raspberry Pi Zero W and is my preferred configuration. Not only can it be fully powered with a 1A USB host interface using the OTG port, it performs surprisingly well compared to some of the enterprise solutions I’ve used.
External power, using an appropriate power/data splitter, is a requirement if you need to control a powered off host or need reliable power during host reboot to access BIOS. Ultimately I prefer the Pi Zero W for PiKVM but there are reasons to use a Pi 4, such as encoding performance and connectivity options the Pi Zero W does not have.
Thank you for sharing! That’s good info, gonna set up one of my Zero’s here soon. Already have the USBHDMI dongle
Not to knock an interesting project, but as a solution to the problem, you can get old enterprise grade dell/hp network KVMs on ebay for less than $100
Are they IPKVM’s without positively ancient implementation of the whole network facing parts.
Not to mention, if one has a Pi 4, SD card, and a USB capture device and finds themselves in a sudden need for a KVM, it’s just a matter of flashing the latest PiKVM image to the SD card, inserting it into the Pi 4, and, if the system has a USB 3.1 Type C (3A) port, just two cables to hook it up and done.
Most IP-KVM devices under the $100 price point are pretty clear — they do not support KVM over IP and they definitely don’t have control pin or GPIO that can be wired, with proper isolation, to the computer’s control pins. While IP-KVM has its purpose, the PiKVM project definitely fills a niche that IP-KVM does not.
Yes. Immediate availability, compatibility with any computer and price are the advantages of this project and they’re undeniable.
Commercial IP KVMs, with one port, start at about $500. Those with more ports are even more expensive and you also *have* to buy an expensive additional cable for each computer you want to connect. Also you rarely get all the functions that this one provides, nor the flexibility.
Not to mention the ancient software and the limited compatibility involved with most commercial units.
Someone also talked about “network” KVM you can buy on ebay fo a hundred bucks… Well those are actually just KVMs that use CAT5 cables and are (sometimes also) capable of long cable runs. They’re *not* IP KVMs, unless it’s otherwise specifided.
The few IP KVMs you find on the used market are usually way more expensive.
For those who want a ready make KVM, Currently ATEN is probably the only brand that actually sells IP KVMs of any kind for less than $500.
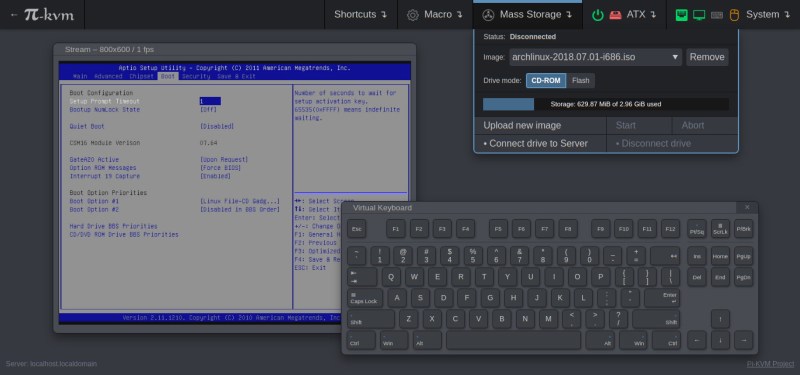
Why is that virtual screen showing SETUP in 800×600 resolution ? Is it scaled ? Square pixels ?
I thought BIOS uses a VGA text mode of 720×400 pixels normally. Or is this UEFI in disguise ?
It’s clearly UEFI. It even mentions the CSM module version in the screenshot…. and 800×600 is much more common of a resolution than 720×400.
I’ve been using Michael Lynch’s Tiny Pilot Raspberry PI 4 based KVM over IP for a couple of months now with great results – https://tinypilotkvm.com/
This looks cool, and I’m glad more players are entering this space
FYI, PiKVM has been around a lot longer, and is more polished and fully featured than tinypilot. It’s been in development for years and when you find a feature you wish tiny pilot had, chances are PiKVM already does.
Good to know, I plan on trying this out when I have time.
I can say that Michael’s customer service is top notch
Now it just needs another MCU to watch the KVM and have a LoRaWAN link for rebooting it etc., if it is misbehaving, then an even smaller and more robust MCU with its own watchdog timer to reboot the LoRa MCU if it stops responding.
And if that stops responding, you’ll need some other kind of timer. Some kind of general purpose timer chip maybe…
As mentioned in the videos and other posts, mini KVM such as iDRAC and ILO not only use Java, Flash, ActiveX, or other esoteric webtech … after they reached the end of life they no longer receive security firmware updates.
Working in a corporate environment, there is this thing called PCI compliance. And if you have any interaction with the federal government you have to meet other additional compliance. And all of them recognize CVE vulnerabilities and flag the Technologies used in these ancient kvm’s. You then have to write up an exception justification to get approved by internal auditors and SecOps.
Whereas this appears more current. Granted you are using someone’s Arch Linux software so this solution might not be viable for many businesses because as it’s not commercially supported, vetted and indemnified. But it’s a step in the right direction.
You can definitely use this as a hobbyist and at home. You might be able to use it at a small to medium business depending on how regulated you are. But this project will not be a solution for larger commercial entities – which doesn’t appear to be it’s intended audience.