As we have seen time and time again, not every device stores our sensitive data in a respectful manner. Some of them send our personal data out to third parties, even! Today’s case is not a mythical one, however — it’s a jellybean Amazon Echo Dot, and [Daniel B] shows how to make it spill your WiFi secrets with a bit of a hardware nudge.
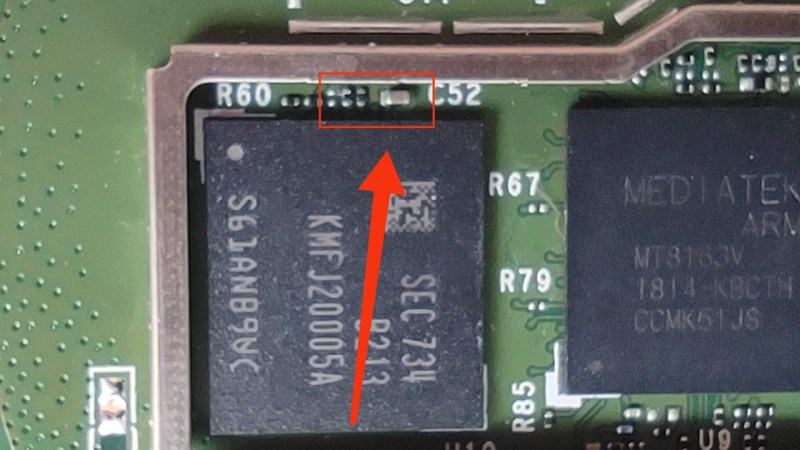
There’s been exploits for Amazon devices with the same CPU, so to save time, [Daniel] started by porting an old Amazon Fire exploit to the Echo Dot. This exploit requires tactically applying a piece of tin foil to a capacitor on the flash chip power rail, and it forces the Echo to surrender the contents of its entire filesystem, ripe for analysis. Immediately, [Daniel] found out that the Echo keeps your WiFi passwords in plain text, as well as API keys to some of the Amazon-tied services.
Found an old Echo Dot at a garage sale or on eBay? There might just be a WiFi password and a few API keys ripe for the taking, and who knows what other kinds of data it might hold. From Amazon service authentication keys to voice recognition models and maybe even voice recordings, it sounds like getting an Echo to spill your secrets isn’t all that hard.
We’ve seen an Echo hijacked into an always-on microphone before, also through physical access in the same vein, so perhaps we all should take care to keep our Echoes in a secure spot. Luckily, adding a hardware mute switch to Amazon’s popular surveillance device isn’t all that hard. Though that won’t keep your burned out smart bulbs from leaking your WiFi credentials.















Kinda funny, I tore my old Dot apart last night to turn it into a crude bluetooth speaker.
Lame
You can connect an alexa to Bluetooth anyway
Hi there! Daniel here, I just wanted to point out that I included a slight misconception in how wpa hashing works in the article and I’ve updated it with a correction at the bottom (I’m 14 and currently studying computer science, almost all of this was based on my own research and made a mistake when researching how password hashing works.). It was an amazing surprise to see this featured, thank you hackaday!
14, wow. Keep up the good work!
You’re either born a hacker or you’re not. The ability to reverse engineer something like this is a special gift and you’ve clearly got it. Keep up the good work, I’ll be looking forward to seeing what you come up with next!
“… perhaps we all should take care to keep our Echoes in a secure spot”.
Unless you’ve totally pwned an Echo or similar device so ‘Zon can’t get their grubby hands on your privacy, the only secure spot for it is on a shelf in an Amazon warehouse gathering dust. Ditto for Ring and other similar spies.
I personally think you are being too optimistic and generous
Fine, but tin foil hasn’t been around since WWII.
My high school physics lab must have been in some me sort of time bubble cuz we had aluminum foil and tin foil and gold foil and even the fencing team had many kinds of foils.
No verbal foils?
Curses! Foiled again.
F-O-I-L – First, Outer, Inner, Last? Anyone? Every time I hear the word, multiplying polynomials is the first thing that comes to mind.
How does tin foil become aluminum foil????
Alchemy!
Particle accelerator.
April 1 is a bad day to post a tech revelation.
It’s in EVERY convenience store. Tin foil and aluminum foil are the same thing.
Daniel,
Great article buddy well done. You should be very proud of it. Good luck with the computer science. You are clearly well suited to it.
Gary
Tin is a heavy metal. You don’t want your food wrapped in tin.
No, it’s meant to protect your head
This is incorrect. Tin is tin, and aluminum is…well, aluminum. The foil could be an alloy and tin, but if it’s called aluminum, it’s mostly aluminum.
In my country everyone calls aluminium foil tin foil, hence the confusion. It was aluminium foil.
Just like ‘gas’… can either refer to gasoline or diesel oil.
It’s not still made of tin. The name stuck in some countries and still call it tin foil. Use Google before being a smart a**
Aluminum foil will work too, and it’s a better electrical conductor as well.
Is the foil just for bridging the pads and bypassing the capacitor? Like, basically pulling the pin to ground I guess?
It shorts the power to ground, preventing it from booting and forcing it into BROM mode where the flash can be dumped or written to.
What does it matter if the device steals your wi-fi passwords by accident after it has already stolen all your private conversations by design? The answer is simple, never let this kind of neo-stasi in to your house, at all.
What private conversations?
Ok, what I don’t understand, is why would anyone even buy the damn things, in the first place.
They are fun and useful little things. Use it for some entertainment or have the kids do an interactive story – but when it’s not in use it’s unplugged.
Because the benefits outweigh the risks. Same reason I get on an airplane or behind the wheel of a car now and then.
Oh it has LOTS of benefits. ;-) Which is why Amazon had an opt-out policy to begin with.
https://www.theverge.com/2023/3/28/23659191/amazon-sidewalk-network-coverage
I have an Alexa enabled thermostat. My whole house is set up for automation. Even have Google devices in certain rooms. It always sounds stupid when you first hear about it, but like good tool, it becomes indispensable. I just understand and accept the risks. The benefit significantly outweighs the risks with this.
as a ‘ham’ who moderates a couple of hamradio groups…I learned to turn the spellchecker off 10+ years ago (boy, do they mangle callsigns). I use Echo as a spellchecker…or spelling suggestor.
> [Daniel] found out that the Echo keeps your WiFi passwords in plain text, as well as API keys to some of the Amazon-tied services.
I don’t think there is much alternative.
A randomly generated per device key encrypting the information would work better, as it means you only need to erase one piece of information the master key (or secure element key).
But at the end of the day if the device isn’t reset, the key will be just as available.
I think it’s the right choice to avoid obscurity where there is no added security, even though it will lead to PR nightmares like this article.
If you use a password to connect to your WIFI access point, this password is shared for all WIFI clients and needs to be stored on the client in a decryptable way.
So, besides cleartext, you can store it encrypted, meaning you would need to enter a decryption key every time the device (re)boots, or store that decryption key somewhere. Most of the time, it is only adding a layer of obfucation, not a layer of security.
The solution to this risk is to use client certificates to access your WIFI. An implementation of this is called WPA Enterprise (instead of WPA personal which uses shared keys). This means all WIFI clients have their own unique key and such a key can be revoked without impact on the other clients.
Good luck finding an IoT device that supports this, though…
While J_B is right about the alternative, and Amazon does support that connection type for business users, wpa2 Enterprise isn’t exactly an easy setup for most consumers. I’d argue vlans are probably a simpler concept than managing CAs. But this article missed a crucial point: you need physical access to exploit this and if you already have physical access then no amount of security on the device is going to matter. API keys are equally silly as the keys are almost always stored with the apps and can be invalidated remotely. Now bearer/access tokens could be more problematic but those aren’t stored on the device but in the Alexa cloud service–a necessary evil to avoid making customers login to every device separately. Dumping from a yard sale could potential grant you a password though, but if you unregister the device, a necessary step so someone else can use it, the device is factory reset. I’d suspect that most consumers don’t take this step though.
One note, this is a kid who wrote this, so I’m not expecting them to go through the vetting steps of security and understanding how Alexa uses oAuth or anything else like that. It’s amazing that such a young mind put the thought process
and time to expand a known exploit into other domains in the first place, and I’ll applaud him everyday for such a feit. But HaD is ran by adults who should know better that this is no different than dumping the firmware from Espressif where we often store the password on the header files.
Ob Stasi: I used to work for a company in Berlin some years ago.
When talk came up about those little technical wonders, my answer used to be
“In former times, state came in to install such things in your flat, concealing the wires and fixing up the wallpaper… all at their cost. Nowadays you pay yourself for such a service”
You could see by the reaction who had lived in former East Germany. I guess those were a couple of potential Echo customers less :-)
I got rid of my echo when I found out there is a 900mhz radio on every model since gen2 or 3 that trys to build mesh networks with BT devices and works with their smart doorbells to build their sidewalk project so it will try to talk to your neighbors devices even if they don’t own an echo. Everything is encrypted though so I find it funny that they encrypt that but not other things like aou keys. and moved to Rhasspy on Home Assistant as 99 percent of what I did was control smart home devices (via Home Assistant),, set timers, and ask about the weather information. You can opt out but it’s buried in the settings and Amazon resets it back to defaults when there is an update on the echo.
Everything is local and stored on a 5 year old NUC as I built a weather sensor which is what provides. 8 was never a fan of free software for all your data business model created by Google and Facebook but making me pay for something, then using it to build mesh networks to help them create something to make money was a step over the line for me. Also, since it’s all local, my smart home devices react way faster. Apple HomeKit is the only system that requires local control and it’s mandatory. I know it’s mandatory with Matter/Thread also but from what I’ve read Matter is a nightmare right now so I’ll stick to ZigBee and esp32/wifi/BT for the moment and keep everything local. One of the great things about Home Assistant is any information you want to send is opt IN. Not opt OUT.
Facebook is the same. Why give people a setting, when one is going to change it back? Basically whack-a-mole security.
I’m interested in how the 900MHz mesh is built. Since BT is not in that range, which devices is the Echo trying to connect with?
It also shares your wifi to transmit data. Amazon says this is capped at 80kbps and 500MB a month and compares it to HD streaming in terms of bandwidth. That doesn’t address the fact that plain text is very low bandwidth and if your echo stores you wifi creds and API keys in plain text that would not take hardly any bandwidth to transfer if the security was cracked.
Amazon does use 3 layers of encryption but as we all know, nothing is 100 percent secure and now they are allowing 3rd parties to create devices so that will end with some bad actors. Just search for “Amazon Sidewalk 900 mhz security” or something similar and you will find lots of articles although some contradict themselves because of Amazon’s silence. Below is a cut and paste from consumer reports. The 900 mhz spectrum is the same spectrum LORA uses which is a low bandwidth, low energy protocol to transmit data over long ranges where cellular isn’t feasible due to power like transmitting data from say, a weather station in a remote location. It’s estimated that it can reach anywhere from a half a mile to a mile with the radio in their echo’s but they have also added it to their security cameras which has raised more concerns and can use your neighbors wifi to turn on a WiFi light if it’s far away from your router and gets a better signal from your neighbors router in your own home. It’s already been proven to reach up to 10000 miles over the mesh network and covers 90 percent of the US already. The record for LORA is as high as 832 km but that’s with a much, much stronger 900 mhz radios then what’s in the echos.
Some say the 3 layers of encryption makes it secure but I disagree. One of the first devices it will be used in is tiles for tracking pets or kids, or people with dementia. Similar to apples tracking “tiles” (I forget the exact name). People will use them to stalk people as people have used Apples devices to stalk people and hide them under there cars or other places due to there small size which makes them very easy to hide. That’s just one of many potential issues.
Essentially Amazon is building its own closed internet and due to the 3 layers of encryption nobody knows what it’s really doing but Amazon. It’s estimated that Amazon is losing a billion dollars a year on Echo because they haven’t been able to monetize it like smartphones (same for Google). So I guess building a closed long range internet is their answer to make that money back.
There is no way this will end well IMO. I hope I’m wrong but I just don’t trust multi billion dollar companies that rip of other companies with the copycat Amazon devices. I believe it’s named Amazon basic but they just look at what is selling well and make a copycat device and sells it for less money. They are also starting to put it in fire sticks and their new TV’s they are selling.
Cut and paste below
How Does the Sidewalk Network Actually Work?
Amazon Sidewalk is technically two wireless networks in one: Bluetooth Low Energy (BLE) and 900 megahertz. The BLE network is for devices within a couple of hundred feet, while the 900 MHz network is for devices up to half a mile away.
To send data to the internet, Sidewalk devices will use one of these two networks to first send data to an Echo speaker or a Ring camera. The Echo or Ring device then sends that data off to the internet via your home’s WiFi. Alternatively, Sidewalk devices can connect to the commercial-grade Amazon Sidewalk Bridge Pro by Ring, which can support “hundreds of devices over five miles away” and has its own internet connection provided by the companies or organizations that install it.
One more fun fact I forgot to mention, the former NSA director Keith Alexander works on the board of directors for Amazon. He once said “The crux of the NSA story in one phrase ‘collect it all'”