Since we’ve started inviting them into our homes, many of us have began casting a wary eye at our smart speakers. What exactly are they doing with the constant stream of audio we generate, some of it coming from the most intimate and private of moments? Sure, the big companies behind these devices claim they’re being good, but do any of us actually buy that?
It seems like the most prudent path is to not have one of these devices, but they are pretty useful tools. So this hardware mute switch for an Amazon Echo represents a middle ground between digital Luddism and ignoring the possible privacy risks of smart speakers. Yes, these devices all have software options for disabling their microphone arrays, but as [Andrew Peters] relates it, his concern is mainly to thwart exotic attacks on smart speakers, some of which, like laser-induced photoacoustic attacks, we’ve previously discussed. And for that job, only a hardware-level disconnect of the microphones will do.
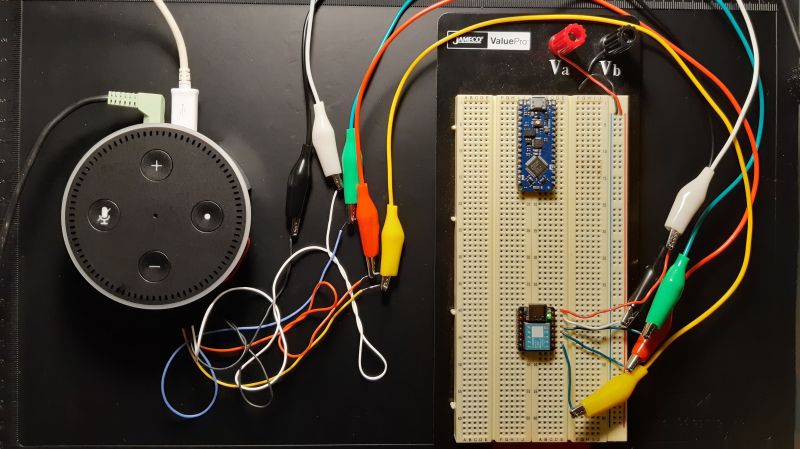
To achieve this, [Andrew] embedded a Seeeduino Xiao inside his Echo Dot Gen 2. The tiny microcontroller grounds the common I²S data line shared by the seven (!) microphones in the smart speaker, effective disabling them. Enabling and disabling the mics is done via the existing Dot keys, with feedback provided by tones sent through the Dot speaker. It’s a really slick mod, and the amount of documentation [Andrew] did while researching this is impressive. The video below and the accompanying GitHub repo should prove invaluable to other smart speaker hackers.















Just ask the device (google, Alexis, Siri) “….. are you snooping?”
The answers are delightful. No, they are not snooping… much!!!
thanks for the info want to pull Alexa from our house.
XD Sometimes I read comments like this and I don’t know if I should laugh or cry. Guys who own pcs and mobile phones, who are using same email and password for everything, worry that Alexa will spy on them xD
An Alexa with 7 microphones and a mains power supply is better suited to spying on me than the battery-powered phone in my pocket. It’s not about making it impossible to spy, but to decrease the attack surface.
google has a mute switch choose that
*edit. Looks like Google has a hardware level switch on some of their devices. Good to know!
Looks like Google has a hardware level switch on some of their devices. Good to know!!
Yes. Also, if attackers were persistent and reset power to your house, your smart speakers would boot up in the unmuted condition, as this is most convenient to the consumer. This modification boots up in the unmuted state.
I typically leave my Dot in the hardware muted condition, but if I’m using it for the radio or some other continuous use, I just leave it software muted. I always place it in hardware mute when I leave home.
This is addressed in the article. It’s ineffective against some types of attacks.
Google is hardware switch, amazon is a software button
What’s even more concerning to me: When you visit someone, their smart assistants may listen to what you say, without your consent. When you invite friends, most of their smartphones are also listening to what you say, whether you want it nor not.
To me, this is peer pressure enforced by surveillance capitalism, and should be illegal everywhere.
But thats not all, the other danger part is, you think you muting the microphone, and still there is one active, but not responding to voice!
But when you select “I agree” you forfeit all your constitutional rights.
That’s assuming one’s “peers” are in accord with what the “surveillance capitalism” has to say. You might find that there can’t be “enforcement” based upon discord.
If you don’t want smart phones to listen to you, then put a phone in a privoro case which has a switch to turn off the mics and replace them with white noise
I was under the impression that the whole point of these devices was their ability to listen to voice commands all the time without additional interaction from the users. So for me an easier solution to this idiotic problem is just not to purchase that “corporate spy” device. Also can’t these things be just turned off/unplugged?
On related note: corporations, like Amazon, Facebook and Google, know about us even more than we know about ourselves. Still everyone use them believing that their personal information won’t be abused in any way by the corporations, outside the agreements signed by creating an account. So if Amazon says “we don’t spy on you with Alexa/Echo”, then why bother with mute switch?
But if you do not buy the device, then people that don´t know better will call you a Luddite or worse. But these same people will cry when their personal information is misused by some evil corporation.
Just wait till I tell them about the outhouse.
Might be a stupid question but why should you care about what information does all of these corporations have about you?
I mean what bad things can they do with this information?
In my case i really dont care about what they know about me, i dont have anything to hide anyway.
Does it matter that a database someplace records your conversation about liking Burger King or your plan to buy new tires? Probably not. But what about the discussion of your cancer treatments, pregnancy, or AIDs medication?
As if that’s not bad enough, your data is aggregated… whole PROFILES exist on you, and from those profiles can be extracted such personal things as your sexual orientation, family relationships, and your voting history.
Anne Wojcicki, CEO of 23andMe, is the sister of the CEO for Youtube. So if you’re foolish enough to use that “service,” big brother now knows what diseases you’ll likely develop and how long you might live. What do you want to bet that info is not tied to everything else recorded about you? You don’t suppose an insurance company or potential employer might be willing to pay big for that kind of inside baseball, huh?
To big tech, you are nothing more than a beneficial strain of bacteria to be studied, and sold.
Worst of all, they’ve convinced millions of people like you that the complete annihilation of privacy is a “service” that you should pay for. It’s like getting raped on a date and then having the rapist expect that you reimberse him for the dinner and the movie.
So Facebook in USA knows that I hate current government in my country, that I’m atheist and I make stuff from wood. Ebay knows that I sell stuff made of wood and buy tools and electronic parts from China. Google knows that I search some datasheets, and sometimes I use their translator to know how to spell some words.Steam knows, which games I like, Epic knows that I’ll pick almost any free game they offer, because I’m cheap. YouTube has my video showing UFO over the town of Garwolin and how I make a bed using magic. And so on and so forth with many other services and sites, some specific only to my country.
So what these corporations can do with all that data? Worst case scenario: they can try to sell me something. Fat chance, as I use adblocker (I really HATE ads!), and I don’t really have any money to spend. There are multiple local and international laws that prevent them doing anything else with that data. And if they try, they would be sued to oblivion.
But lets assume that you don’t want corporations to know anything about you. The only option is to never use Internet, your smartphone, nor your credit/debt card. Pay cash, buy locally and avoid all services and electronics that can spy on you…
There was case a few years back, when local grocery store chain was caught using cameras to profile their customers (age group and sex, one or more people per receipt + what they bought), the “night soil” storm was quite big…
Well there’s you making whoopee.
https://gizmodo.com/a-home-security-worker-hacked-into-surveillance-systems-1846111569
Attacks and racial slurs.
https://www.theguardian.com/technology/2020/dec/23/amazon-ring-camera-hack-lawsuit-threats
In a similar vein, no doesn’t mean no.
https://www.theverge.com/2021/1/31/22258856/amazon-ring-partners-police-fire-security-privacy-cameras
Does anyone else want to argue for voluntarily bugging themselves?
Worst case scenario is actually more like something that happens to people all the time:
You are rejected from a job application, mortgage application, insurance claim, etc. When you call and ask why, the person says “I’m sorry sir we utilize a suite of risk-analysis tools which provided an unfavorable result in your application”.
Maybe it was all those times you coughed when around your smartphone, or how often you sounded stressed or sad when asking for the daily news, or how often you check the price of items over $200 before purchasing. They don’t know, and neither will you.
@Ostracus.
This only proves that some people can’t write good and secure firmware, and that maybe some things should not be connected to the Internet. Besides, in case of ring camera the ability to be used remotely is part of its purpose. The fault is in its hackability. Also why are you complaining about device being hacked on a site at least partially dedicated to hardware and software hacking?
@Lachlan.
This “risk assesment tool suite” is probably a HR temp worker from external recritment company, who visited your social media accounts and didin’t like their contents. I think that’s rather much more likely than “persistent cough detection app” running somewhere on your phone just in case you would seek a job at the company that wrote it.
There was a case in my country, when a primary school teacher lost her job because a parent visited her social media profile on one of those local “Facebook before Facebook” platforms and discovered she liked to wear leather lingerie in her spare time. I believe that a jelous wife caught her hubby staring at those photos.
And the US government say Huawei are unsing their devices and equipment to spy…. Ffs people.. If you think apple, google and samsung arent doing the same then umm.. 🤪
Clearly you haven’t watched Black Mirror. Also, Cambridge Analytica was a real life example of how that data can be used to send targeted propoganda and convince someone that untruths are true.
Do you leave your front door open? Do you allow people to watch your family anytime day or night? Would you allow someone to watch (listen) to you and your SO being intimate?
Saying “I have nothing to hide” means nothing. People who say this don’t realize the things they’re already hiding.
Absolutely agree with this statement.
Too easy. We need an overly complicated solution here.
And I’m here to provide such a solution! But the real value in projects or research like this isn’t always the final product, but how it can be used as a stepping stone to achieve something greater. I suggested in my video that people who are more software-savvy could create an app that gatekeeps smart home devices. A lot of these devices are very well designed and hard to replace with open-source creations, but they also tend to be guarded by good firmware that is tough to overwrite.
The mute switch is so my roomate cant easedrop on me in my room from the dot in his.
All valid points. My wife received the Echo Dot from a previous job as a Christmas gift, or else we would not own one either, and we never powered it up except for this project (although it has been on since). The issue isn’t just the corporations; even if you trust them, there are many ways outside attackers can get to your information. The best electronic defenses will always be penetrated by those with the time and knowledge to try. Just look at the LockpickingLawyer or the entire field of penetration testing for non-malicious forms of bypassing entry controls, both electronic and physical.
Still waiting the the simplest solution. A small embedded linux device with a LCD on it that acts as a middle man between your router and Alexa. Alexa will connect to this device and this device will then connect to your router.
The LCD will show traffic both ways on the lcd. This way if Alexa is listening you will see traffic data.
What if the data is buffered and sent later when you are not looking?
Log files are a thing…
The problem is that most of these devices seem to trickle a constant stream of data anyway for various things, and compressed voice data is tiny, so I’m not sure how much you’d end up seeing. It would be really nice if they’d let you break the SSL / allow signing failures to see exactly what it was sending, but for good reason they’re unlikely to allow that (and could indeed see when it was being sniffed due to the signing failure).
Well as HaD and other places have demonstrated there are people as smart, if not smarter than us. Combined with the surveillance issue already in the public consciousness, one would think the question of, “what do they know” would have been known by now.
I, too, solved this problem by never buying one*.
Unfortunately that is getting harder by the day. I bought a TV on Black Friday to replace the one I’ve had for 10 years. Imagine my surprise learning that the remote was a wifi device with a microphone in it and Alexa built in and no discernable way to disable it.
I’m able to mitigate this with some network nerdery but the average user is hopelessly unable to opt out of the corporate surveillance state.
We are living in a wet dream of the Stasi.
*which, of course is completely negated anytime someone else shows up at my house with their iPhone or Android or Kindle or fitbit or….
Thank you for reminding me that I need to cut the mic out of the remote to my new Roku unit. A screwdriver and a pair of side-cutters is even more effective than the solution in this article, but it’s a one-time fix.
I hope my “bottom end(?)” Rokus (Rokii?) doesn’t have one, but I’ll check!
I think that the ones that have that “feature” have a button on the remote control to activate it.
Here’s a simple fix: don’t buy a TV.
My Android phone doesn’t listen to anything – I use Wi-Fi only when checking for updates and weather, and data transfer is disabled completely due to costs. I also use MAPS.ME with some offline maps on the SD…
I have a mic-enabled Roku, too. I’m considering adding a toggle switch in series, or just eviscerating it with a sewing needle.
I was told at an Alexa developer event that it’s already a hardware button. There’s some discussion on these pages, https://iot.stackexchange.com/questions/2382/is-the-amazon-echo-mic-mute-a-hardware-switch , https://youtu.be/xH8LnK9hh6w , https://blog.adafruit.com/2021/01/12/is-the-amazon-echo-flex-mute-button-real-or-fake-iot-internetofthings-alexa-dieshot-electronupdate1/
I hope all of you keep your phones disconnected from the internet at all time, otherwise this paranoia is ridiculous.
These same companies you support are impacting free speech.
HaD is impacting “free speech”.
There is a lot of ground between ‘I won’t make a landline call because someone may be listening’ and ‘I do a public facebook livestream every time I want to talk to a friend, because why not, and what do I have to hide?’.
– Sooner or later these things will come back to bite us (more than now). There are already companies providing employers automated scoring in various categories on applicants from AI/ML-parsed social media scraping. You posted something thier algorithm found to flag you as an activist in some area? – sucks to be you.
– It’s not just ‘what advertisements you will see’ – it can affect your employment options, creditworthiness, and more. I’d be surprised if health insurance providers aren’t already lobbying for ways to make it legal to base your premiums (or insurability at all) based on the wealth of information profiled against you. I shared a ride to an airport with someone on the IT side of a marketing firm – their datasets were measured in petabytes – and this was a good number of years ago.
How many years until we have to have chips implanted ?
Could do with some feedback for when it is muted (those red LEDs look handy) – you might forget and leave it unmuted at some point.
Place small radios with NPR and Rush Limbaugh playing nearby to keep Alexa company.
B^)
I wonder why nobody (yet?) wrote a song “Alexa, order 10 tons of ice cream” and paid a radio for broadcasting it…
Huh, this was not HTML… Try it again:
(insert xkcd here)
Imagine a record company making a song that basically makes everyone with Alexa in range of a radio to buy their less than popular albums…
And maybe, it could be accomplished with an “inaudible” signal that would be part of the music, such as infrasonic data?
B^)
Hopefully the albums that get ordered would be in the same musical genre of the song that is playing, I’d really hate to get hip-hop in the mail, because I was listening to a Country-Western station.
One of these days I’m gonna write a rap to country and western translator, change every instance of 5-0, heat, popo etc to lawman or sheriff, references to drugs to moonshine or whiskey, references to bubble or box, lowrider or caddy to truck or horse, maybe leave caddy half the time.. turn down the bass a bit, turn the melody to twangy geeetar.
Yes, Max, my mod only includes momentary feedback. I really wanted to use the red mic mute LEDs, but the SAM D21 processor in the Xiao doesn’t support the power levels required to drive the test points for them either HIGH or LOW. If I could fit the standard Arduino ATmega328P processor, I may have been able to achieve this. I considered driving the ring LEDs, but those take around 1.5V, so some extra components may have been required to ensure I didn’t fry any (more) LEDs.
Wow, the range of paranoia here is remarkable. Watch the Netflix docuseries called Spycraft and see where we really stand with “big brother”. Our biggest enemies that we routinely use include of course cell phones with built-in GPS and live microphones, credit cards, on-line purchases, browser search histories/cookies, voter registrations, license plate scanners, toll booth videos, etc. Alexa/Google pale in comparison. I like my Alexa and don’t care about it “listening“. I also have a number of exterior video cameras that store video in the cloud.
Still it doesn’t mean we need to invite corporate snoops into our homes to listen in to our conversations.
A government player is unlikely to sell your data to an insurance company… something I’m sure Facebook or Google would have no problem with at all.
“Just because you’re paranoid, doesn’t mean someone isn’t out to get you.”
-Kurt Cobain?
just never get one ever.
It’s easy to disable google assistant on android, revoke the microphone permission from the Google app. Alternately, block it housewife by adding the appropriate urls to your pihole or firewall blacklists.
https://xkcd.com/1807/
Hmm, fun party trick. Lmao
I would like to point you to a relatively little known hacker blog that, just two weeks ago, ran the story that the mute buttons on Echo devices are indeed hardware and not software:
https://hackaday.com/2021/01/14/is-your-echo-flex-listening/
Yes, voltage is removed from the mics, but this is because the ADCs are commanded to remove the MEMS mic biasing voltage. Unlike the video from your reference article, the Echo Dot has 7 microphones, and there’s three lines that come from the ADCs to each mic, so their schematic wouldn’t explain the full picture. Also, the digital power to the ADCs comes from a larger power plane that doesn’t lose power. If I tear back into my Dot again, I’ll look into this more.
“Since we’ve started inviting them into our homes…..”
What do you mean “we”?
I thought to myself, Farcebook needs users more than I need Farcebook.
I stopped logging in the day they wanted a copy of my ID to prove who I was.
I also stopped using Upwork for the same reason. They already had my banking
information to pay me. The reason Upwork wanted this info?
To “protect against fraudsters and hackers”. My reply to this was, OK, so you
are worried about “fraudsters and hackers” and cannot guarantee my information
will be secure? Think about it, how many data breechs have been in the news?
Then think about how many haven’t been. My own rule of thumbs and 8 fingers is,
keep my mouth and data closed. Stores that want my phone number get the reply
that I don’t have a phone. Zip code, I tell them use the store’s. Would I like
to sign up for “rewards/membership card” no thank you. Had one saleslady ask me,
but don’t you want to save money? My reply, not at the cost of my info and purchase
history being tracked. My personal info is just that, my personal info and the best
way to keep it secure is to keep it to myself. So, no Google, Alexa or Echo in the house.
No smart TV either. So I’m supposed to live in fear of being called a Luddite? Oh the horror.
This isn’t the playground and I’m not 6. I don’t need Alexa to turn off my lights or lock
my door. If getting off my fat butt to lock a door is all I have to worry about, I can
handle that.
So you admit to having a fat butt? I’m telling Alexa. But seriously, your approach is the safest possible. People like Rob Braxman even take it a step further by helping create smart devices that have been “de-Googled”, to further ensure your digital footprint is minimized.
Yep sure do. Old, fat, happy. :)
So…if you are really worried about it listening in on just a specific conversation…just unplug the damn thing during the conversation. Re plug afterwords.
For added security they get your phone number too. Now they can tie all your data together.
These devices hear all your conversations, even the tv. Ever heard your device respond to the tv – there is a tv add that triggers our google and the response is I don’t have any photos.
So let’s take a contrived example…
You and a friend are discussing a murder case on tv. It’s all recorded by google as we know (the all acknowledge this). Now a real murder happens and unfortunate for you, you’re a suspect. They get a court order for the google recordings. At trial they play the recordings of you discussing the tv murder. Guess what, now you’re really in trouble!
Those who marched on the capital, better think about what you discussed around your smart devices!
Everything you do, talk about, search online, photos you post, buy, even in the supermarket, your trips everywhere (gps in phones) are all being logged and collated, directly to you. This is used to target advertising, and fraud scams. This is what we’ve given up. It’s not a conspiracy theory, it’s pure fact!
Your voice print is known and can be compared. In Oz the government uses voice print identification as a security measure for their services when logging in, as well as phone identification.
It’s only a matter of time before criminals use this info way worse than google etc use it for just targeting ads. You can bet they’re trying to hack googles info!
Simple solution, don’t get one and instead of saying Alexa turn the light on get up off the couch and flip the switch.
It would be much simpler to just add a WiFi smart switch to cut the power to the echo…
Google, turn on the Alexa.
Remember the Iraqi trading cards? Spammers would have to send out a million emails to make $6K in dollars. The problem is the people who will respond to advertising gives the spammers and telemarketers reason to exist.
I have a no solicitation policy. You can profile me all you want but I won’t talk to telemarketers or do business with them.
The problem is people are socially giving statistic takers information at the malls. Once they know how much you make, they know how much to charge. The price of service on your home heater is based on home prices by zip code.
If you want to pay more, fill out the survey questions which as you your education and income level. I also imagine these club cards at grocery stores track and average your purchases.
I do think the products shown on Amazon is based on how much you will spend on an item.
For those of you wanting to turn off the microphones, consider how much of your information is stolen by the Solar Winds hack and has already been traded or sold on the black market.
The problem is your date of birth and social security is like using the same password on every website.
The problem is laws have to be stronger than hippa when it comes to your rights on your information.
A police officer told our PTO at school, he adds people on facebook after he makes an arrest. How does he do that if profiles are set to private? I don’t believe in giving people any information for free on social media who have made no effort to be friends which is why I don’t have social media and because I don’t have privacy.
And then you see people who trespassed on capital hill getting arrested from the videos they posted on social media and the video giving GPS data. It makes no sense.
I guess you can say people do dumb things sometimes.
The goal of any company is to make as much money as possible and to use any means
they can think of (legal and quasi-legal) to separate you from as much of your
money as they can. No company give a crap about you. To them, you’re a revenue stream,
nothing more. Even after you die, your data and data profiles live on the net for
years, even decades. You’re a number, a piece of data to be used until you no longer
fill the company’s coffers. That’s what it boils down to. You’re tracked by that
“convenient” phone in your pocket and every shred of data is analyzed to see how it
can be used to annoy the living crap out of you and ultimately attempt to suck every
last penny from you. There is no rich Nigerian prince wanting to send me a billion
dollars, my computer isn’t sending out spam, it doesn’t have a virus and I don’t need
some “tech” from Timbucku to fix what isn’t broken. And last but not least, I don’t
need some squawkbox listening to every word I say so my online searches can be “tailored”
to my interests. Some senator once said that Americans wanted and liked to receive
robocalls. I for one, and I believe a majority of the USA would agree with me when I
say, “Leave me alone.” Go on youtube, you’ll see plenty of videos of people who go out
build some small cabin out in the middle of nowhere and disconnect from all the
electronics and just enjoy life. They grow their own food, take care of themselves,
and are not bothered bu telepests, Alexa, Google, Farcebook etc.
What makes me laugh are the so-called “preppers” who post on youtube that are supposed
to be “prepared for the big one” or whatever. This ham operator was on the news.
He was showing off his radio station, his emergency food, his battery backup and power
system etc. From 3 states away, I knew his address based on his call sign.
When push comes to shove, people WILL find him they WILL take what he has, even if
they have to kill him to do it. It’s a dog eat dog world and it’s everyone for themselves.
Things like Alexa only make things easier for those that want to take from you.
So as I sad earlier, no smart tv, no Alexa nothing that can listen in.
If I don’t want Alexa snooping, I use a very simple process, using existing tools. I unplug it.
Alexa plays me music for free, wakes me up as an alarm clock, helps me with recipes, is useful as a search engine, gives me the box scores, gives me the weather, tells me corny jokes, etc, etc, etc.
I can listen to different radio stations.
Tells me my commute time.
Gets me the news.
Gives me reminders.
And I delete my data whenever I want.
Growing up, it was taboo for a salesman to call us oh the phone. The object is not to get rid of technology but the object is to get your rights back. Congress won’t do that.
I have a company that did business with me and then they start doing sales calls at home when I’m at work. I put them on an eternal block because they don’t get it.
What the major cell phone carriers need to do is to make more anti-telemarketing tools.
What I have done in the past is text telemarketers back and tell them I know they are a scammer and that stopped a lot of junk texts.
This is also a national security issue but people fail to see this. What was the purpose of Iraqi trading cards? To be able to train the troops to identify opposition leaders. What does the phone system give our enemies? Intelligence.
I’m disbled. Alexa offers me a level of help and communication I would sorely miss. I also am aware that everything I do, from going places with phone in hand to searches on Google, is recorded. I have a public persona available to whomever. And when I wish to do something outside that public persona, I simply deprive my collection of monitoring devices of access by turning off, unplugging, and/or leaving them behind. This method doesn’t require hacks of any sort.
Actually I have one hack I use regularly. When I get tired of ads for tactical vests and dating sites, I visit a couple of my fav online vendors. In a couple of cases, I get ads telling me of sales without having my inbox cluttered with daily email.
Never been daft enough to waste my money on one of these. They aren’t useful – I’ve never once thought of a task I really wish I have done with a listening device. And of course the other thing they don’t overly want you to realise is that the ludicrously lazy “turn on the lights” thing will only work if you have Smart bulbs installed – each of which will set you back around £10.
Daft?
somewhat lacking in mental acuity… A few marbles misplaced…
And thinking on it further I’d have to agree its bonkers…
Unless you in a situation where you don’t have lots light switches so you need the bulbs to have onboard switching (perhaps the houseboat/caravan type thing where you want lots of light sources, but don’t have lots of wall space to put individual switches) it makes no sense to spend extra on the ‘smart’ bulbs, and tie yourself into whichever smart ecosystem, that can just dissappear on you when the company gives up or changes standards..
I can see some useful occasions for voice control – never have enough hands, but its never seeming to me useful enough to pay the companies to spy on you for… Especially as you can get such functionality without, probably less accurate initially with more manual training for your voice without that hidden army of humans listening in for the big cloud companies…
This seems redundant, as Echo hardware actually disables the hardware when the mute button is pressed:
https://electronupdate.blogspot.com/2021/01/amazon-echo-flex-microphone-mute-real.html
What these devices (all of them) need is local processing that can recognise a single, user selected (or taught) ‘activation’ word or phrase, they come on for 5 minutes, ready to send your complex articulation to the cloud for processing, then turn off waiting for the keyword again.
There are better solutions. See http://xyzhang.ucsd.edu/papers/KSun_SenSys20_MicShield.pdf
This automatically shields private information and only lets voice commands pass.