A team of researchers from the ASSET Research Group in Singapore have published the details of a collection of vulnerabilities in the fifth generation mobile communication system (5G) used with smartphones and many other devices. These fourteen vulnerabilities are detailed in this paper and a PoC detailing an attack using a software defined radio (SDR) is provided on GitHub. The core of the PoC attack involves creating a malicious 5G base station (gNB), which nearby 5G modems will seek to communicate with, only for these vulnerabilities to be exploited, to the point where a hard reset (e.g. removal of SIM card) of the affected device may be required.
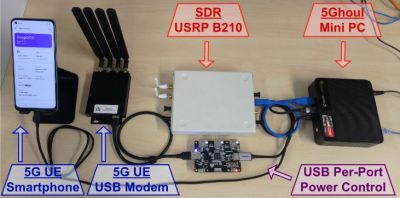
Another attack mode seeks to downgrade the target device’s wireless connection, effectively denying the connection to a 5G network and forcing them to connect to an alternative network (2G, 3G, 4G, etc.). Based on the affected 5G modems, the researchers estimate that about 714 smartphone models are at risk of these attacks. Naturally, not just smartphones use these 5G modem chipsets, but also various wireless routers, IoT devices, IP cameras and so on, all of which require the software these modems to be patched.
Most of the vulnerabilities concern the radio resource control (RCC) procedure, caused by flaws in the modem firmware. Android smartphones (where supported) should receive patches for 5Ghoul later this month, but when iPhone devices get patched is still unknown.
















I assume power cycling the attacked device is the only option for those who have devices with eSIMs…
Bigger the G bigger the risk.
Terribly shoddy programming, probably comes about due to the fact that a lot of the code is now directly generated from specs by tools. In this day and age, being able to crash a stack because of invalid input over the air beggars belief. I went through all this back in the day with 2G, and we are still making the same mistakes?
Great name for an exploit. But unlike Wifi and Bluetooth exploits, there are fines for operating on frequencies that are owned by someone else. Pictures always make it look so easy, but I suspect the researchers had a box with lots of RF shieling sitting behind them.
When doing this kind of research, you make a testbed by replacing the antenna with a direct link to the SDR. There is literally a universal connector for antennas, so it works on everything that isn’t 100% garbage.