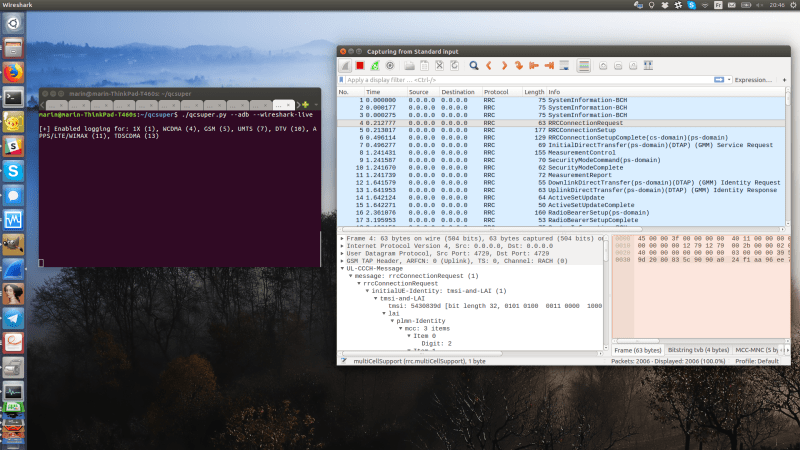
If your thought repurposing DVB-T dongles for generic software defined radio (SDR) use was cool, wait until you see QCSuper, a project that re-purposes phones and modems to capture raw 2G/3G/4G/5G. You have to have a Qualcomm-based device, it has to either run rooted Android or be a USB modem, but once you find one in your drawers, you can get a steady stream of packets straight into your Wireshark window. No more expensive SDR requirement for getting into cellular sniffing – at least, not unless you are debugging some seriously low-level issues.
It appears there’s a Qualcomm specific diagnostic port you can access over USB, that this software can make use of. The 5G capture support is currently situational, but 2G/3G/4G capabilities seem to be pretty stable. And there’s a good few devices in the “successfully tested” list – given the way this software functions, chances are, your device will work! Remember to report whether it does or doesn’t, of course. Also, the project is seriously rich on instructions – whether you’re using Linux or Windows, it appears you won’t be left alone debugging any problems you might encounter.
This is a receive-only project, so, legally, you are most likely allowed to have fun — at least, it would be pretty complicated to detect that you are, unlike with transmit-capable setups. Qualcomm devices have pretty much permeated our lives, with Qualcomm chips nowadays used even in the ever-present SimCom modules, like the modems used in the PinePhone. Wondering what a sniffer could be useful for? Well, for one, if you ever need to debug a 4G base station you’ve just set up, completely legally, of course.
















Nice …. so I’m guessing I could legally sniff my own unencrypted data from one of my external 4G devices by way of IP address? …. or how would I filter through all the other traffic?
Be careful about the “legally” part – that the device isn’t transmitting doesn’t mean you won’t run afoul of any telecommunication secrecy laws which go back ages, to the era of paper letters and sealed envelopes.
That you are physically capable of receiving some signal doesn’t mean you are legally allowed to as well. Check the laws in force in your jurisdiction and if in doubt, don’t! Prosecutors and courts don’t like nerdy smartasses trying to tell them something doesn’t apply only because it has been written before cellphones were a thing.
Granted, this would be both difficult to detect and to enforce but don’t do stupid stuff – such as posting videos on social media/Youtube showing you how you are using such a device and exposing the content of someone else’s communication. If the regulator catches wind of that you are pretty much assured to get a police visit because of the laws on surveillance, eavesdropping, etc.
The last paragraph is important. I think our law is like: You are not allowed to receive communication, not intended for you or as broadcast. If you happen to recveive such communication by chance or unintended, you have to ignore the fact of of the reception and contents and DON’T TELL ANYBODY about the reception. What you did not hear/read you can of course not tell anybody about. :-)
I have zero clue about how cellular networks work, but even though you can read packets surely they are encrypted and you can’t access their contents, right?
A) It doesn’t matter
B) Only packet contents might be encrypted, data in the headers like the IMEI can’t be to function.
Think of it like a letter in the mail. The letter inside can be encrypted, but the delivery address on the envelope can’t be if you have any expectation of it being delivered, and even reading that delivery address might be a crime.
For certain cases that might actually be the most interesting part of sniffing:
My (admittedly layman’s) understanding is that cellular standards have included encryption since more or less forever(though the stuff associated with 2G has a lot of ominous-sounding cryptoanalysis work about it; not sure about 3G); but that, for export, debug, or telco-standards-are-set-by-national-carriers-and-some-spooks reasons; some of the encryption options are null cyphers that offer only plaintext levels of protection.
Knowing that your local cell tower is negotiating everyone down to null, or some 2G thing with known attacks, is interesting information even if you don’t have any desire to poke at other people’s packets; especially with all the stingrays about.
A much-needed disclaimer, puts it way better than I did, thank you!
I’m not a lawyer, but this is just looking at traffic between the cell and _your phone_, so I don’t think there’s any legal issue here.
If you want to know what the apps running on your phone are up to, however, this is super duper important.
I’m pretty sure I remember that back in the way-old days… when cellphones were still analog and unencrypted the law was that you could listen to anything that was unencrypted… except cellphones. There was a specific carve out to make cellphone listening illegal. Or was it just selling devices that were capable of it… Now I’m second guessing myself.
Whatever it specifically was, although I am sure more restrictions have been added I really doubt any old ones have been removed. So, like Jan said. It’s probably best not to go posting everything you receive on the internet.
Difficult to say with any authority because laws differ country by country, what’s legal in your bit of the world might be illegal in mine and vice versa..
EG:
In the UK it’s illegal to listen to any radio transmission you’re not licenced to receive or aren’t broadcast for general reception and it’s a further offence to act on anything you may have heard.
So, in theory, you could be prosecuted for listening to your taxi being dispatched and going to the kerb when you know it’s about to arrive.
Sorry, I usually think to qualify that with “In the US” when I comment on legal stuff. I’m not sure why that slipped my mind yesterday.
Also recommended: Scat https://github.com/fgsect/scat
Is it legal now? In my phreaker days it could land you in jail.
If the government can do it with out a warrant, why can’t we?
I have used this interface to debug roaming issues in IoT devices. You won’t see non-broadcast traffic to other users.
I used to do this for my old job at QRC. We developed several Android and windows mobile applications that could receive GSM and CDMA paging channel information. It was called ‘Cnitch’. It was used primarily for target development. We could tell whether or not certain cell phones were in the area based on their IMSI. I even developed a non alerting traffic stimulator to call people’s phones without it ringing to generate paging channel traffic. We used primarily Qualcomm based chipsets using the diagnostic mode port. I also developed several cellular monitoring and survey tools using the same methodologies. That tool was ICS-QP.