We’ve all been there. You are on a flight, there’s WiFi, but you hate to pay the few bucks just to watch dog videos. What to do? Well, we would never suggest you engage in theft of service, but as an intellectual exercise, [Robert Heaton] had an interesting idea. Could the limited free use of the network be coopted to access the general internet? Turns out, the answer is yes.
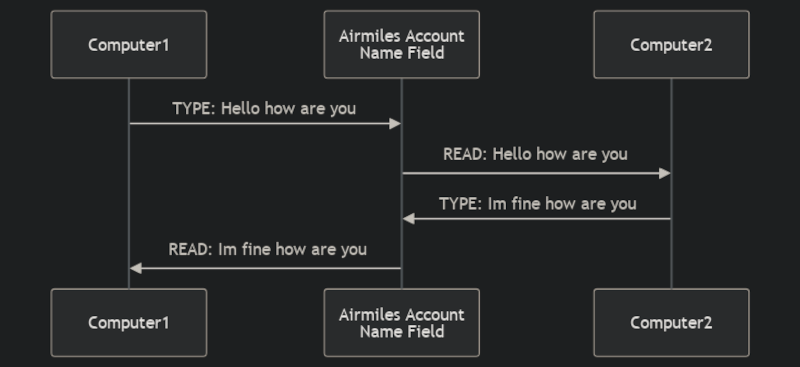
Admittedly, it is a terrible connection. Here’s how it works. The airline lets you get to your frequent flier account. When there, you can change information such as your name. A machine on the ground can also see that change and make changes, too. That’s all it takes.
It works like a drop box. You take TCP traffic, encode it as fake information for the account and enter it. You then watch for the response via the same channel and reconstitute the TCP traffic from the remote side. Now the network is at your fingertips.
There’s more to it, but you can read about it in the post. It is slow, unreliable, and you definitely shouldn’t be doing it. But from the point of view of a clever hack, we loved it. In fact, [Robert] didn’t do it either. He proved it would work but did all the development using GitHub gist as the drop box. While we appreciate the hack, we also appreciate the ethical behavior!
Some airlines allow free messaging, which is another way to tunnel traffic. If you can connect to something, you can probably find a way to use it as a tunnel.















In the old land line days to save the cost of a phone call, people used to ring each other and count the number of rings rather than pick up the phone and the count would be a message e.g. four rings for “I will be late” or five rings for “I am leaving work now” etc.
I heard that the rings you hear when calling aren’t the same rings that come through on the other side. Maybe that one wasn’t the case, or is only the case for out of area. But I’d like to know
I think that was often true. However, if the recipient was on a party line, each party had a different ring pattern. So selecting which number to dial conveyed information even when no party went off-hook.
That is, all parties heard all rings and knew which pattern was intended for them.
Here on ISDN continent there was a (short?) time where one could send text messages for free via the D-channel. I tried it once but our PBX system didn’t “support” it natively and I didn’t have an ISDN PCI card for a computer (we went online via a rs232 connection directly to the PBX).
ISDN has two 64 kbit/s “B-channels”[1] for voice or dial-up internet (128 kbit/s if using both) and one 16 kbit/s “D-channel” for control and signalling information.
The later one was abused for sending text messages – which is kinda similar to counting rings but on steroids and “classy” ;-)
I’m not actually sure it worked but it was reported in a respectable German tech/computer magazine back in 2001(!) [2].
[1] https://en.wikipedia.org/w/index.php?title=ISDN&useskin=vector#Bearer_channel
[2] https://www.heise.de/news/Kostenlose-Chat-Software-koennte-ISDN-Netze-verstopfen-42441.html
A colleague student of me connected PLCs from distant locations to eachother that way, but I wasnt too impressed by his security, but it did work.
PLC = Programmable logic controller?
My first guess was “Power-line communication” because you can run “PLC” over telephone cable[1] too… ;-)
I think I was too young / not yet interested enough back then for playing around with PLCs. Kinda bummed looking back because for several years there was a small PLC demo setup standing in my attic-closet(?) – a few DIN rails, surrounding modules and whatnot. Dunno why my electrical engineer father brought it home at some point but it was gone again when I at least kinda understood a few years later (maybe quite a few years).
[1] https://hackaday.com/2012/04/18/ethernet-over-telephone-wire/
and https://hackaday.com/2019/11/14/ethernet-over-dc-power/
Some European telcos didn’t charge for ISDN BRA D-channel traffic (like Deutsche Telekom) so messaging over this channel was attractive and there were services explicitly to do so.
Unfortunately most of the UK providers did charge so it never took off in the UK.
We had some disappointed vendors from Germany come and demo their kit before they discovered this pitfall in their “free” service..!
There were “official” kits from real vendors?
All I remember is the free software “Linefire” linked above.
And didn’t Deutsche Telekom quickly disable/block the usage of the D-channel for that purpose too?
https://de.wikipedia.org/wiki/D-Kanal
^^ No source cited but it claims many ISDN providers quickly blocked Linefire and the like.
Answering machines… If greeting played after two rings there are new messages waiting and you proceed to enter the remote access code. If no greeting after two, no new messages and just hang up before the greeting to avoid the charge.
Back in the olden days of pagers we had a code where the last 6 digits of the number you entered for call back corresponded to a message on an agreed upon sheet with 2 being the message and the last 4 being the time, (We mostly met int he afternoon). it required one person to make the call but we managed to have people with no service and no cell be reachable almost anywhere and anytime.
That reminds me of a way I once talked with online friends for free from a painfully offline rural area. In the mid-90s, I was at home for the summer after my (very online) freshman year at college. This was before local ISPs became a thing there in small-town Wyoming, so after a couple of semesters of heavy internet I was disconnected — but the state for some reason had a dial-up BBS on a toll-free phone number.
It was meant to provide access to state government data, but for some reason they implemented it as a dial-up Gopher client hooked to the Internet, and the links led to off-site things, including a telnet gateway that could get me to a kind of read-only IRC client I’d found. You could connect to arbitrary servers and join channels, but not type anything to those channels. But you could change your nickname. So I could join my friends’ channel and have very slow conversations at the expense of the state government.
(Of course after a couple of those slow conversations, one of my friends supplied me with a different account with a reasonable IRC client. The admins disabled that telnet access after a couple of weeks, but it was fun while it lasted.)
What are you 3? Or do you just lack all common sense?
Planes aren’t really critical infrastructure. Utilities (water, power, sanitation) are.
I’d recommend checking what terrorism actually means before saying such bs.
TCP over DNS with iodine! Still works because captive portals can’t really respond with mangled DNS data (it’d get cached and site would be unreachable even after paying)
I have very rarely been successful with this approach when using a system where have to pay to use the WiFi!
All cool and such to bypass certain limitations, but, is normal cell coverage not sufficient to play cat-videos and post selfies? I’m sure am missing the point, but why pay lot’s of money for a phone subscription allowing for several GB/month and then log in to some crappy unknown wifi access point. In other words, why bother. Okay, I know (I really do, it’s about the challenge), but still.
Normal cell coverage isn’t an option on an aircraft?
For security reasons, wireless communication is prohibited on planes unless tested to all hardware.
Instead of a blacklist it depends on a whitelist.
With all hardware I mean the wiring, the gearbox, gear traction displays etc.
While it might look harmless, you’re gambling with all human lives on the plane for mid air failing controls might render the plane uncontrollable.
I’ve heard that the prohibition of cellphone use on airplanes has nothing to do with airline safety, but rather the fact that a cellphone in the sky can reach a large number of cell sites, and therefore cause a bit of havoc as they try to figure out which should handle it. Combined with the fact that the phone is moving at airspeed means that lots of hand-overs would need to take place. Probably not a big issue for a single phone, but a plane load of them would be.
Of course, that’s just hearsay, so may not be accurate.
Probably not accurate at all because I can’t imagine any normal cell tower using non-directional antennas or ones actually pointing to the sky…
As in I can’t imagine any normal phone to be able to communicate at all with any normal cell tower because cell towers use directional antennas to cover their cells (different horizontal sections, in high traffic areas maybe even with slight vertical variations to divide one horizontal cell into different sub-cells).
Limroh, even if the phones didn’t send any signal in looking for towers, then unless the towers are all downtilted so that their beam pattern cuts off below their horizon, then any of their beam pattern that doesn’t hit the ground, even if it’s aimed below level, will eventually go to cruising height on its way to space as the earth curves away underneath. Or from the other perspective, there will be a donut around a few hundred miles radius of each plane where numerous towers all have the plane within their beam patterns. I would think that if a phone can manage high speed data when it’s lying on the floor in the depths of a building in a neighborhood full of trees and other signals and such, where the tower is a few miles away and not visible, then I find it feasible that the total emissions of many phones on many planes could add up to something, if they are not inhibited from transmitting.
I’m pretty sure if cellphones posed any kind of actual threat to the safety of a commercial plane, they would confiscate them before you got on.
I have serious doubts whether everyone really puts their phone in airplane mode on the plane (though I always do). If they don’t, we have empirical data about safety of cellphone communications on the plane.
Uh, no, normal cell coverage isn’t enough for that and neither is whatever costs lots of money for only several GB per month. Videos and pictures run through that in much less than a month’s time when you do actually have good reception. And without a VPN, the cell company screws with your traffic more than I’d like, so it’s only somewhat better than the wifi. And yeah, once you’re on the plane you either use their connection or nothing.
Radio Defined == Hard way
When Air France introduced their free messaging option, it was clear it wasn’t limitec to messaging but simply very throttled bandwidth.
Then on one flight I discovered one way or another port 80 wasn’t throttled – this being the age when non-https sites were essentially no longer a thing. Before the next flight I set up a proxy on port 80 and enjoyed free bandwidth :)
Cue the next flight and they’d limited port 80 too! Oh well…