As the name of the channel implies, [BuyItFixIt] likes to pick up cheap gadgets that are listed as broken and try to repair them. It’s a pastime we imagine many Hackaday readers can appreciate, because even if you can’t get a particular device working, you’re sure to at least learn something useful along the way.
But after recently tackling a VTech video baby monitor from eBay, [BuyItFixIt] manages to do both. He starts by opening up the device and going through some general electronics troubleshooting steps. The basics are very much worth following along with if you’ve ever wondered how to approach a repair when you don’t know what the problem is. He checks voltages, makes sure various components are in spec, determines if the chips are talking to each other with the oscilloscope, and even pulls out the thermal camera to see if anything is heating up. But nothing seems out of the ordinary.
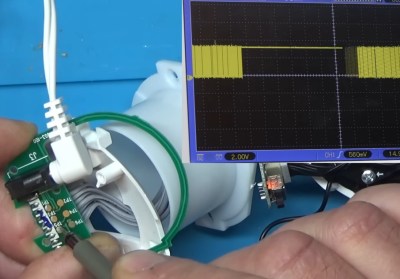
While poking around with the oscilloscope, however, he did notice what looked like the output of a serial debug port. Sure enough, when connected to a USB serial adapter, the camera’s embedded Linux operating system started dumping status messages into the terminal. But before it got too far along in the boot process, it crashed with a file I/O error — which explains why the hardware all seemed to check out fine.
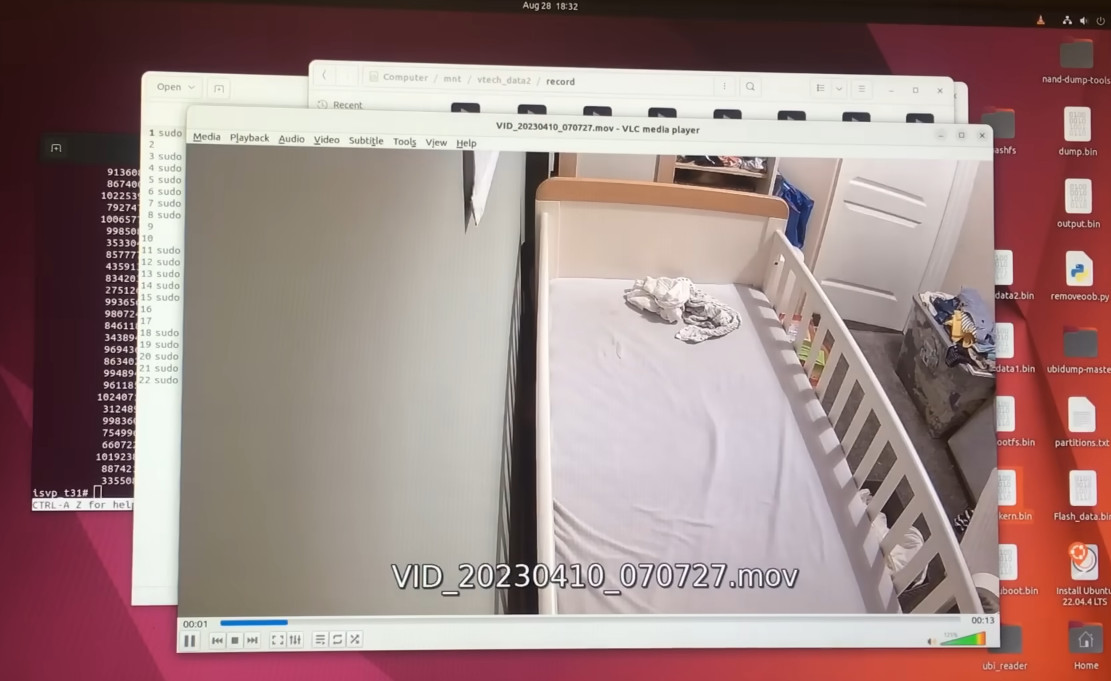
Now that [BuyItFixIt] knew it was a software issue, he started using the tools built into the camera’s bootloader to explore the contents of the device’s flash chip. He uncovered the usual embedded Linux directories, but when he peeked into one of the partitions labeled Vtech_data2, he got a bit of a shock: the device seemed to be holding dozens of videos. This is particularly surprising considering the camera is designed to stream video to the parent unit, and the fact that it could record video internally was never mentioned in the documentation.
While copying the chip’s contents over serial would have been possible, [BuyItFixIt] instead pulled it out and physically dumped the whole thing with a reader. With a bit of Linux-fu, he’s able to mount the chip dump and confirm that the videos in question are of the previous owner’s infant. Yikes. Of course, he promptly deleted the files once he realized what the camera had stored, but it makes us wonder how many cameras like these are holding private video files waiting for a bad actor to uncover them. This is an important reminder of the inherent dangers of tossing away “broken” smart devices.
As for the repair itself, [BuyItFixIt] reasoned that some file — maybe the database of videos — must have been corrupted on the chip, so he took the nuclear option and wiped it all out. He had to use the bootloader commands to recreate the partition table, but once that was done, the firmware seemed to understand that it had been returned to a factory state and was finally able to boot up normally. He’s documented the commands he used to get it back up and running in the hopes he can help out somebody else with a similarly ailing camera.
We can never get enough of this sort of firmware hacking, and the fact that this particular bout opened up with a great real-world example of hardware diagnosis makes it all the better. This is a long video, but one that’s well worth your time to check out. If you’d like to see more repairs from [BuyItFixIt], we’ve got you covered.
















The only part that should be shocking about this is that it left behind evidence of its wrongdoings. Who knows what and when things like this upload to where.
@Duh said: “Who knows what and when things like this upload to where.”
It continuously uploads what it stole from you directly to Pooh Bear in the Chinese Communist Party.
Good point. No imminent need to panic, thus.
Back in the late 20th century, babyphones did operate on 27 MHz and could be heard by whole neighborhood.
Back in 70s and 80s, about everyone had a CB station, even in the car, which makes it even more relevant.
But even if they hadn’t, CB to medium wave converters had been around.
So people could listen to 11m band and babyphone in the car radio.
They couldn’t send, but receive. That was useful for certain things. CBers could listen to their friends’ weekly rounds on CB or could hear their girl friend calling them home. Things like this.
But that was another time, maybe. People were more relaxed, more open. Less soap opera.
Back then, children used to walk to school all alone or with friends (better), did explore neighborhood with bicycles and so on.
At least here in my country. Not sure how it is in other countries.
Ah, the good old times, Back Then (TM).
Back then there were no data brokers [1] sweetening your hardware provider’s razor-thin margin. Nowadays, I suppose there is no choice but.
The times, they-a-change.
[1] https://en.wikipedia.org/wiki/Data_broker
The other times is gone in large parts from Sweden.
Now the kids do not have time to be outside.
Kids has commonly 6.5 hours of screen time outside of school time.
The Swedish Public health office released recommendations for screen use yesterday.
The report is now being followed up with recommendations on screen time for children and young people. Children between 2 and 5 years old are recommended to use a screen for a maximum of 1 hour per day, children between 6 and 12 years a maximum of 1 to 2 hours, and children between 13 and 18 years a maximum of 2 to 3 hours.
Back in the 70s there weren’t any billion dollar companies fighting with each other over who could find out your “impression” of today’s end cap display at the supermarket, based on linger time, skin temperature, desperation and heart rate rhythms, pupil response, and any other insanely invasive yet somehow legal methods.
Back in the 70s it took a 3 letter agency and a psyop to change someone’s opinion of something important.
Today it just takes a credit card and hyper targeted ads.
The biggest difference is that today, WE are the product.
This isn’t surprising. Having a short cache to handle brief intermittent outages is a feature more than a bug.
What is surprising is that the device didn’t have a “factory reset” button that blew away all saved data. It’s also surprising that their legal department let them leave it turned on without documenting it. This is the kind of thing that can get you sued if you don’t either document it or leave it “off by default.”
Try actually watching the video, it looks like there’s 30 or 40 individual videos on there. That’s not a “short cache” by any definition.
Even if it was, why would they not be deleted regularly?
Probably a circular buffer, delete oldest when low on space thing.
Also possible if the WiFi went out they were never uploaded.
I wonder if this is an attempt to optimize network traffic at the server. I don’t really know, but I suspect that having thousands of these streaming live to a server would require more resources than having each camera buffer a certain amount of data, then upload it at intervals. You would need some kind of buffering in the camera for that, most likely a circular buffer.
That said, it wouldn’t be hard to build a buffer clear for videos more than X days old at boot.
Very interesting!
Engaging in malicious activity requires much more intelligence than an activity carried out with negligence, laziness or stupidity. Fortunately intelligence is a less widespread quality than negligence, laziness or stupidity among humans. And that intelligence also requires more financial means (except of course for the commercial or legal consequences that negligence, laziness or stupidity sometimes entails).
Since this device does not have an internet connection to call home, nor a GPS to locate the user, it would seem that the second hypothesis is the correct one.
That said, I remember someone saying: “only the paranoid will survive”. In addition, being paranoid from time to time allows you to feel like an important person ;)
You’re NOT paranoid if they are really out to get you
I’m not paranoid ,just like very much my tinfoil hat, but THEY don’t know it cos I cover it with a normal hat. I’ll leave it here so they cannot trace my locat…
Are there any ip cameras that you can by that don’t
a) have a back door
b) easily hackable to get control of your network,
c) send data to some third party,
d) all of the above
?
I think the only way to get one that is ok is to build it yourself, the bought ones seem to be the number 1 dodgy device..
Whatever back doors they have won’t do them any good on an isolated network. There is zero reason to give one internet access. If you want to view them remotely, VPN in and access the cameras through the DVR.
Agreed, but most consumer ones now have cloud DVR, so you’re stuffed. I run older cameras with motion eye, but even they needed hacking to output RTSP.
Raspi or ESP32 running your own code
^ this is the way, I’m amazed by how cheap ESP32cams are.
I think there are some that are easily hackable to let you replace the firmware with open source firmware. Alas, I have not kept track of which ones those are.
Since this is hackaday.. You could use SSTV and a scrambler circuit.
The AF signal then can be carrierd by anything that works.
An web audio stream, radio transmitter, microwave link, infrared, the landline..
Try MotionEye OS and an R Pi – plenty of bells and whistles to tweak.
Buy it fixit has lots of intetesting videos. This was a very interesting one and left me admiring his skillset.
Second that :)
FWIW, to “short circuit” the Linux boot process, given access to the bootloader, you can change the linux kernel command line to set “init=/bin/sh”, which dumps you straight into a shell, from which you can explore the filesystem, manually executing the steps from the usual init=/sbin/init sequence until you get to the part that is failing, or until you get enough to figure out what the problem is.
remount,rw is also your friend after that.
Are those 0 Ohm resistors really used here as fuses?
It’s not an uncommon thing. They’re not great fuses, but they’re cheap.
Jumpers are more common, sometimes they used as test / debug points, you unsolder them so you can monitor the current etc, although they usually vanish after the first board revision.
I have bought a broken secondhand baby camera once. After digging around I found the wifi credentials of the former owner in plain text. Good advice to throw these smart devices away, and not sell them because you don’t know what you could be passing on.
“Hey, wiretap, can cats eat cheese?”
https://i.imgflip.com/2ulado.jpg
Go to your local resale shop and buy 2-3 digital picture frames. Most resales sell them for about $3.99 USD. Gauranteed at least one will still have all the photos in the memory and there is no hacking involved. You’ll get great stuff on these EG: weddings,wedding receptions, family birthday parties. most people are too ignorant or simply don’t care if others see their business.
They don’t care. All those photos are up on their Facebook, Twitter, Insta etc anyway.
Quite often, a secondhand smart TV had all the IP based movie subscriptions still active.
Can be cheaper than paying the subs.
Now they have all sort of data like how long does your baby sleep, does it cry often, and does it require a night light. (ads for night lights to follow…)
49mHz not 27 for the audio babysitters. Landline cordless too, I knew a lot of the neighborhood back in the nineties. People would read their CC number over the air.
Hi, yes, 49 MHz is right. But cheap or old babyphones did exist for 27 MHz, too.
They used the odd spaced channels. 11m also was an ISM band here in Germany, at least. That’s why it was nicknamed “Schrottband” also (scrap band, a reference to industrial use).
R/C toy cars had usd 27 MHz, too. Early models of the 1960s/1970s used 27,120 MHz frequency from before the days CB radio was being opened to public (that was 1975 in Germany and/or Europe, I think).
Before 1970s, they had used even lower frequencies in use for r/c models. 13 MHz, I think. And even lower. Professional r/c fans used 40 MHz, I believe.
Nicely done, but I think I’d have looked at a side-project with some pogo-pins for those bottom contacts /way/ earlier than he did.
OK what if this was just the display unit buffer? eMMC RAM is super expensive given these devices are sold for less than $80 retail. Even if there were multiple clips, I would just assume it was designed to just get overwritten again and again and this could lead to possibly multiple footages. I own this device and can totally see why it would do these things. I would imagine if the signal was spotty, it would need to wait until it has sufficient frames to start playing to prevent a choppy video stream display which many would consider as broken. I believe the design choice is also valid since the device itself never connects to the internet. It would be a stretch to call out this finding malicious rather than cheap design flaw.