Today, you likely often authenticate or pay for things with a tap, either using a chip in your card, or with your phone, or maybe even with your watch or a Yubikey. Now, imagine doing all these things way back in 1998 with a single wearable device that you could shower or swim with. Sound crazy?
These types of transactions and authentications were more than possible then. In fact, the Java ring and its iButton brethren were poised to take over all kinds of informational handshakes, from unlocking doors and computers to paying for things, sharing medical records, making coffee according to preference, and much more. So, what happened?
Just Press the Blue Dot
Perhaps the most late-nineties piece of tech jewelry ever produced, the Java Ring is a wearable computer. It contains a tiny microprocessor with a million transistors that has a built-in Java Virtual Machine (JVM), non-volatile storage, and an serial interface for data transfer.

While it might be the coolest piece in the catalog, the Java ring was just one of many ways to get your iButton. But wait, what is this iButton I keep talking about?
In 1989, Dallas Semiconductor created a storage device that resembles a coin cell battery and uses the 1-Wire communication protocol. The top of the iButton is the positive contact, and the casing acts as ground. These things are still around, and have many applications from holding bus fare in Istanbul to the immunization records of Canadian cows.
For $15 in 1998 money, you could get a Blue Dot receptor to go with it for sexy hardware two-factor authentication into your computer via serial or parallel port. Using an iButton was as easy as pressing the ring (or what have you) up against the Blue Dot.
Indestructible Inside and Out, Except for When You Need It

Made of of stainless steel and waterproof grommets, this thing is built to be indestructible. The batteries were rated for a ten-year life, and the ring itself for one million hot contacts with Blue Dot receptors.
This thing has several types of encryption going for it, including 1024-bit RSA public-key encryption, which acts like a PGP key. There’s a random number generator and a real-time clock to disallow backdating transactions. And the processor is driven by an unstabilized ring oscillator, so it constantly varies its clock speed between 10 and 20 MHz. This way, the speed can’t be detected externally.
But probably the coolest part is that the embedded RAM is tamper-proof. If tampered with, the RAM undergoes a process called rapid zeroization that erases everything. Of course, while Java Rings and other iButton devices maybe be internally and externally tamper-proof, they can be lost or stolen quite easily. This is part of why the iButton came in many form factors, from key chains and necklaces to rings and watch add-ons. You can see some in the brochure below that came with the ring:
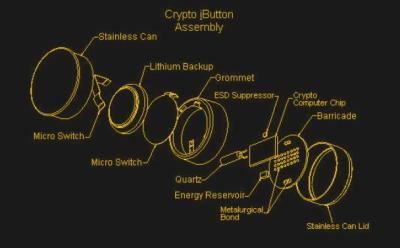
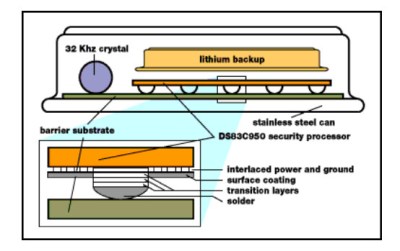
The Part You’ve Been Waiting For
I seriously doubt I can get into this thing without totally destroying it, so these exploded views will have to do. Note the ESD suppressor.
So, What Happened?
I surmise that the demise of the Java Ring and other iButton devices has to do with barriers to entry for businesses — even though receptors may have been $15 each, it simply cost too much to adopt the technology. And although it was stylish to Java all the things at the time, well, you can see how that turned out.
If you want a Java Ring, they’re on ebay. If you want a modern version of the Java Ring, just dissolve a credit card and put the goodies in resin.


















Dallas TouchMemory ? we had a customer in ’96 (in Argentina) that use the Dallas versions DS1994 for access to a lab where vaccines were produced. It was used in a high humidity environment, the people of Dallas didn’t like high humidity :). It worked well, if I remember correctly.
I’m pretty sure that the UK pub giant Marston’s used these for quite a while. The staff had something which looked like this on a lanyard, and authenticated to the POS system with it
I’ve seen these in a lot of pubs. Of course, I don’t know if they’re actually Java Rings or just some other kind of token in the same form factor.
It’s interesting to look back at the old JVM, which was very much designed for embedded use — like, the only part of the language which allocated memory was the
newkeyword, and by restricting it to static initialisers only you ended up with a remarkably usable language which didn’t have any form of dynamic memory allocation, and because it was interpreted programs were very dense. And as it was a strict subset of desktop Java, development was trivial.Why is it bigger than Dallas challange-response button?
Nothing happened. That iButton became part of technology’s past. The rest of the buttons are still around, mostly. But the original idea lies with a timer built by BULOVA for the Explorer 1 sat. It became a watch. From there the Dallas people created them. I still use the RTC buttons for the stuff I build.
I desperately wanted some of these back in the early 2000’s, but they were export restricted due to the crypto, and could not be shipped to South Africa. They should be the same size as any other still-available iButtons, I would expect, if they are intended to use the same readers.
And yes, they are still in use here in South Africa for things like security guard patrol tracking – they have a smart baton that they touch to a series of iButtons (typically only holding a 64-bit identity) scattered around the site, that records the time that each identity iButton was touched to confirm that the guard was not sleeping on the job.
Such devices could store some data associated with the device owner, but it can’t store a useful amount of data. Such data would either have to be public, or the device would have to authenticate someone trying to access it.
A useful amount of data associated with the device owner is easily stored in a database on a server. The device can be used as an identification key “into” the database. But that’s no more useful than an RFID or banking SecurID type device.
Hence such devices aren’t much more than a solution looking for a problem.
I’m pretty sure LaserQuest used I-Buttons. I just kind of assumed they were I2C EEPROMS before.
One-wire, I meant one-wire
The SDK was dreadful for these things, and I suspect that was a big part of it. It was clunky, brittle, and closed source and didn’t really offer much in terms of inspiring exaples.
I remember snagging a dev kit to play with and arriving at the conclusion that there was previous little it could do in practice that couldn’t be done just as well with a signed blob stored in a plain old EEPROM (since it had no real I/O with the outside world except to its base station, other than knowing the time and possibly a private key, anything you fed it had to be when it docked and at thay point its maximum capability envelope was a limited transaction log and the only thing it could offer over a vanilla EEPROM in that respect was the ability to refuse to update itself for an untrusted base station).
With modern ECC keys and experience with TPM/FIDO operation it could probably be done much better. You have it generate a key locally that it will never give you, sign the public portion at your authority, and put that cert back on it. Then you have an API to sign or do key-derivation with it and you’ve got a nice identity system.
I will not run, jump, or climb!
YES! When i looked up what an iButton was while reading this article, that was the first thing I thought of! Vivid memories of going to LaserQuest as a kid, and they used these neon colored sticks with a round metal circle on the end to activate your guns and packs iirc. At the time I just assumed they were magnets but I am willing to bet they were iButtons. Glad to see somebody else remembers as well haha.
They’ve been popular as guard-tour stations, where the iButtons are in little wall mounts bolted to various places on the building or grounds, and the guard walks around with a reader and touches them to prove that they actually walked the property rather than sitting in the guard shack playing Angry Birds all night.
I still have mine from the first JavaOne conference.
Vin Prothro (RIP) gave me his card and said, “If any of these sales people give you the runaround, you call me!”
iButton devices are still heavily used in Fleet Management, for driver authentication, trailer identification, access control for heavier machines like scissor lifts etc. I’ve worked with heaps of different devices over the past.. 14 years (holy cow!) and almost all support reading this type of 1-wire device. An added bonus is the plethora of RFID/NFC card/tag readers available that also output scanned data using the same type of 1-wire interface.
I have been to a resort in Turkey where all guests got a tag like this on a wristband and our bar tab was placed on it. I spent millions on beer that way (as a beer cost about a million Turkish Lira back then… go figure how long ago that was).
As I was there to paraglide, I wore mine on the ankle instead of wrist, much to the amusement of hotel staff.
Old-stock Java Cards have now been repurposed by NXP and ST Micro (at a markup) as “Secure Element” ICs used in the emerging CCC standard for vehicle entry via cell phone.
Forget the Java button – the Thermochron is where it’s at. I had a need to log some temperatures over time a few years back, except all temp logger gadgets apparently cost five kidneys for some inexplicable reason. I was NOT in the mood to hack together something myself, but then I remembered Dallas made an iButton that was using its internal battery to work as a completely standalone temperature logger – you just had to “commission” it first, telling it how often to wake up and log etc. then remove from the reader, place at target location, retrieve later, and read out the temperature log (and turn off). And of course I had one of these in my drawer at work from the BeforeTimes when we actually considered using these for access control (I think?). Still worked fine, did the job…
Ah, Thermochrons. We had been fighting with our building maintenance people over poor temperature regulation in our new office space and weren’t getting anywhere… until I used a few Thermochrons to log temperatures over several days in different cubicles. I imported the data into Excel and produced some nice graphs to prove the wild temperature swings we were complaining about. The building people finally gave in and spent the time to adjust the ductwork to fix the problem.
I still have my Thermochrons but one or two have died – presumably when their batteries gave out – and one got lost somewhere in my car when I was trying to study how my windshield sun shade affected interior temperatures. I suppose one day I’ll find it buried under the seats along with spare change and old french fries. I wonder if the data will still be readable?
I found one on the sidewalk outside Moscone Center in SF after a JavaOne Conference. Owing to it’s ungainly size & general unattractiveness, I always referred to it as a Java® Pimp Ring.
At least one community college in Sacramento used iButtons for door security, long after they went out of style.
Thanks for the mention :)
The article was a good enough read that I read it to the end, and I’m glad I did.
There’s a little confusion evident in some of the comments. The Java Ring was just a wearable carrier for a Dallas Semiconductors Java iButton. I don’t fully understand the technology, but I think the idea was that a Java application could be loaded into the Java iButton and would run inside a secure, tamperproof processor inside the device itself. I suppose one could do other things with it, but the flagship app for the Java iButton was authentication.
The Java Ring was probably mostly a marketing thing to put the technology into a familiar form for developers to play with.
If I recall correctly, Sun Microsystems had a family of diskless workstations that incorporated an iButton port and the internal employees had cards – I don’t think it was a ring – with a Java iButton they could use for secure authentication. I don’t know if the product ever made it out into the wild in any significant way. If I recall correctly, Java iButtons weren’t exactly inexpensive – even outside the ring form factor – and as some have said they weren’t easy to program. Other than Sun’s internal workstations I’ve never seen one in actual use.
The iButton form factor is used for plenty of other devices that aren’t Java iButtons, and some of the commenters here have encountered them. One of the big wins to the physical form factor is that they’re just about indestructible in normal use. No, they’re not hammer-, Dremel-, or steamroller-proof, but they’ll last forever hanging on a keychain or attached to a surface.
Some Laser Tag places used them to identify their customers; you’d pay a couple of dollars the first time you played and they’d register your nickname and give you an iButton. Each had a guaranteed-unique serial number that identified you without having to sign in. These were inexpensive serial-number-only devices and no Java iButton was involved.
The iButtons used by security patrols are likely the same thing. The security guards could prove they made their rounds by carrying a reader that they’d touch to a serial-number iButton at each required station to log the time when they were at the checkpoint. Again, no Java needed.
Other iButtons had readable/writable memory, and there were applications where that could be useful.
Thermochrons have a temperature sensor, a real-time clock, memory to hold 2000 samples, an internal battery, and a unique serial number (so you can tell multiple devices apart). You program the clock with the current time (they did drift a little bit) and then set them on a mission to take a sample at user-selectable regular intervals and save them into their memory. They can also save overtemp/undertemp events. The internal battery allows them to keep their time and do their sampling completely disconnected from any computer or source of power. I think the Thermochrons’ batteries were rated to provide a million temperature readings before running out. That sounds like a lot, but you had to be careful because logging the temperature once per second (saving only the last 2000) would wear your battery down within a couple of weeks. They were sealed inside the iButton can so once they’re dead… they’re dead.
All of these products used the Dallas Semiconductor “1-Wire” protocol. 1-Wire, as in they used a single wire (plus a ground) to connect many (not sure the limit) iButton devices without having to have selection lines or multiplexors. The devices use draw parasitic power supplied on the single data in/out line.
BTW, one common and inexpensive place where we see the 1-Wire protocol very much in use is with DS18B20 temperature sensors. These are available in (less bulletproof) TO-92 packages for under $1 each, or $2 each in a ‘probe’ format with a short cable and a steel shell. These generally have an third wire because they need a separate 3.3-5v supply. Although Dallas Semiconductor does allow some versions of the DS18B20 device to operate using parasitic power, I haven’t managed to make this work – either because mine aren’t the right parts, or because they’re cheap clones.
Code to read these temperature sensors using Arduino, ESP32, and Raspberry Pi is really easy to implement, and I’ve used them extensively to monitor freezers and heat pumps for malfunctions. They’re highly recommended!
Since you went to the trouble of writing such an extensive post, I’ll also add a pointer to OneWireHub (https://github.com/orgua/OneWireHub), firmware for various microcontrollers to implement the device side of the 1-Wire protocol, so you can convert an analog thermistor to an emulated ds18b20 1-Wire sensor.
Hah, and that points out a bit of a downside of using the supposedly-unique serial numbers of iButton/1-Wire devices. If you’re smart enough to be able to clone the serial number of a (non-Java) iButton used for simple ‘authentication’ (like in the Laser Tag example) or proof-of-physical-presence (the security guard example), then you can take someone else’s identity or make it look like you’re making your rounds when you’re actually napping under your desk.
Which – to get back to the original topic – is why the Java iButton (on a Java Ring or not) made sense for more secure applications. All that extra tech inside a sturdy, tamperproof/tamper-evident device made it impossible (supposedly) to clone and ideal for its intended use.
The badge won out as a wearable. Now and then NFC rings pop up, but I don’t really see anyone using them.
For authentication these schemes are like keys, “something you have”. But that is not the primary method today. It’s “something you know”. Your bank should keep asking to the think in your head, even if, as XKCD pointed out, the $5 wrench might break that.
I thought the iButton was also used to measure acceleration forces and temperature in packages? To make sure your shipment was handled correctly, not tossed around, transported upside down, overheated.
I have an iButtonLink with “linkTH” connected to a raspberryPi zero2w, monitoring my basement temp and humidity. (Verifying performance of a dehumidifier bought last year).
The company I work for has also included a 1wire-to-I2C converter in an industrial product we sell, in case customer requirements begin to include environmental monitoring.
Java rings are no longer “a thing” but 1wire is still out there.
I’ve only used these things dozens of times in a single place, ULTRAZONE… The most awesomest laser tag arena of the Northeast Philadelphia burbs, next to the DMV outside the Neshaminy mall. Back in the 90s after paying for your turn in the arena you were handed one of these things to tap onto the vest of the gear /rifle combo in the staging area. If memory serves that was quickly shut down and the associate who worked the room began handling them all after a couple years. Was fun while it lasted, for my 15th birthday I got a gift card that I’m pretty sure was supposed to get me my own Java ring to track my scores but instead they only gave me a punch card in the end…. 😢
I have a Sun Microsystems Java ibutton men’s ring which I think I was given at a conference in San Francisco back in 1998. Looking online, I have found several similar rings either on ebay or written about in various forums and blogs.
However, at the same conference, I won a Dallas Semiconductor men’s Fossil Watch with a Java ibutton on the wrist band. I have searched online but have never found another one. Does anyone know if any others exist or if it was just a one off that I just happened to win at the conference?