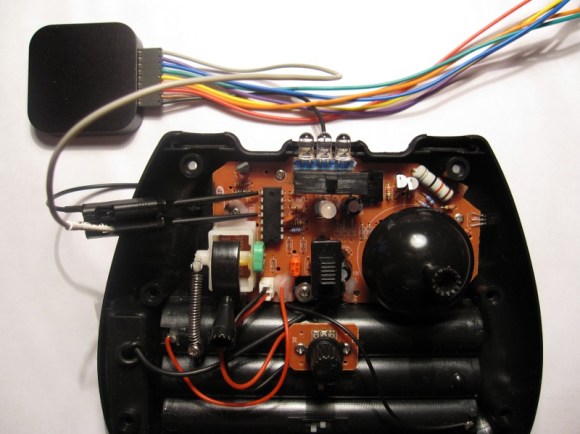
[Jim] used a logic analyzer to do some in depth analysis of the Syma 107G helicopter’s IR protocol. We’ve seen work to reverse engineer this protocol in the past, but [Jim] has improved upon it.
Instead of reading the IR output of the controller, [Jim] connected a Saleae Logic directly to the controller’s circuitry. This allowed him to get more accurate timing, which helped him find out some new things about the protocol. He used this to create a detailed explanation of the protocol.
One of the major findings is that the controller used a 3 byte control packet, which contradicts past reverse engineering of the device. There’s also a new explanation of how multiple channels work. This allows multiple helicopters to be flown without the controllers interfering.
The write up is quite detailed, and explains the reverse engineering process. It also provides great information for anyone wanting to hack one of these low cost helicopters. From the details [Jim] worked out, it would be fairly easy to implement the protocol on your own hardware.