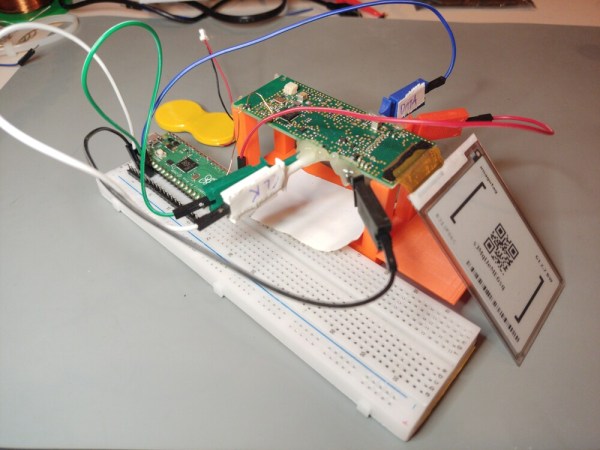
E-ink displays are great, but working with them can still be a bit tricky if you aren’t an OEM. [Jasper Devreker] got his hands on three e-ink shelf displays to reverse engineer.
After cracking the tag open, [Devreker] found a CC2510 microcontroller running the show. While the spec sheet shows a debug mode, this particular device has been debug locked making reading the device’s code problematic. Undaunted, he removed the decoupling capacitor from the DCOUPL pin and placed a MOSFET between it and the ground pin to perform a voltage glitch attack.
A Pi Pico was used to operate the MOSFET over PIO with the chip overclocked to 250 MHz to increase the precision and duration of the glitch. After some testing, a successful glitch pathway was found, but with only a 5% success rate. With two successive glitches in a row needed to read out a byte from the device, the process is not a fast one. Data pulled so far has shown to be valid code when fed into Ghidra, and this project page is being updated as progress continues.
If you want to delve further into hacking e-ink price tags, checkout this deep dive on the topic or this Universal E-paper Sniffer.