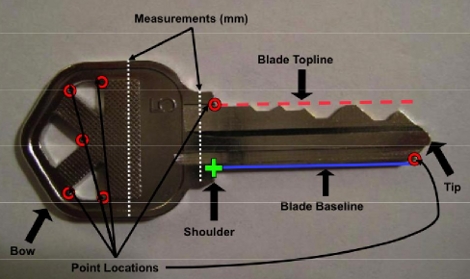
[Ben] and his associates over at the University of California at San Diego came up with a way to duplicate keys using a picture of them. They developed an algorithm that uses measurements from known key blanks to extrapolate the bitting code. Because the software is measuring multiple points it can correct the perspective of the photo when the key is not photographed on a flat surface, but from an angle.
They went so far as to test with cell phone cameras and using a telephoto lens from 195 feet away. In most cases, correct keys were produced within four guesses. Don’t miss their wonderful writeup (PDF) detailing how key bitting works, traditional covert duplication methods, and all the details of their process. The lack of available code prevents us all from playing secret agent (or felon) with this idea but [Ben] did mention that if there is sufficient interest he might release it.
Lock bumping showed us how weak our security is, but this is a bit scary.
[Thanks Mike]
















I once had a car key snap in half when I was pretty far from home. After going to numerous locksmiths I finally came to one where the guy just looked at the key and made a new one free hand.
The key he made actually ended up working smoother than the original.
This tech could actually be useful for more than just snooping. If it’s perfected we could get better key copies and less degradation over copies.
Whats even funnier are the people who have been using crypto techniques to break building keying systems.
You take pictures of as few as three keys from the same building and you can usually extrapolate the freaking MASTERKEY sequences for full access to the whole place. Fun.
This has actually been done for some time in intelligence circles, which is why they don’t rely on keys.
@Dan, or perhaps we could just take the human error factor out of key replication so next time i have a house key made at home depot i dont have to follow it up with a call to my locksmith when i lock the original inside.
but on a serious note i dont think there software would be that hard to replicate even with no code to start, sure the measurements need to be precise no matter the angle or scale of the photo but for a vast majority of key blanks if you have a picture of the real key, an identical blank a computer and a metal file i would think you could do it by hand… going to check now
what about a scanner?
you could scan a key and have a copy that can be used later.
Perspective correction comes in most image editors. I don’t think you’d need to write any code at all.
I suspect that the code is to come up with the key automatically.
after reading the whole PDF i see they have gone many more step then a camera a file and the GIMP but there point is the same as mine you could do this for just one key with nominal cost and time investment or for a fairly reasonable sum implement a system to automatically parse images and cut keys.
evil thought in 3, 2, 1, parse the web for images of keys feed them into your machine and start sending working keys to people with a note saying ‘i have another of these in my pocket please send 100 bucks to….’
@kyle
being the s.a. i am, i would send them a picture of the 100 bucks.
Hey Dan, if that was a Porsche, and in Indianapolis, about 15 years ago? your welcome.
This is interesting in that the software can come up with a solution for any key, but if you know what type of lock it goes to(usually on the key)even just by looking at it you can guess the cuts. Most(just to cover my ass) keys are cut in increments, so you can look at a key and say, “oh so that is cut like 4-5-3-6”. That’s how experienced locksmiths can make copies of keys just by looking at them.
My girlfriend once locked her keys inside her running car when she left it to warm up one cold winter day. It was an older car, the door key was seperate from the ignition key. The mobile locksmith who came out to help us just simply looked into the car, saw the door key on the ring and went back to his van and cut one in about a minute. Amazing skills, and kind of scary. This is also why it’s a good idea to never put pictures of your keys on the internet. I know it sounds like something that wouldn’t happen, but I can’t tell you how many times I’ve seen people take pics of something on their desk or something and have their keys right there, all their little bits and bobbles completely obvious!
My grandfather is a locksmith. He has made keys with a hand-held tool after just looking at the key.
It’s a bit overkill to come up with an algorithmic solution since any sufficiently skilled locksmith can do the same thing without the technology, and can probably turn out the key more quickly.
If this thing could instantly start cutting a key the second a picture was snapped in an automated process, it might beat a locksmith at it. Of course, its kind of man vs. machine in the “John Henry” sort of way (and about as irrelevant and pointless to today’s society).
Rated high on the research to never be finalized or publicized list.
I wouldn’t be too worried, this isn’t a new concept. I’ve been doing it for quite some time and it often does make better keys than the original.
While traditional key copying methods are analog and error prone, this method relies on matching the given measurements to exact known depths. This means that as long as the error in your measurements or the original key is less than 50%, a new key can be produced to perfectly match the target lock.
The only difficult part in the process is getting a clean shot; resolution is no issue whatsoever, but many cameras have difficulty attaining proper focus at that level.
@Bob: You know any resources for insight on the algorithm? I can see how some type of pattern in a bitmap and known key sizes can be cross referenced and deduced, but I want to see it actually implemented. There are hundreds of key blade types just in pin tumblers too; I’d like too see some type of geometry database.
If I was going to write code to do this, I’d keep reducing or increasing bitmap geometry and after any potential matches where pointed to I’d go to another stage that does further pattern recognition.
The dynamic aspects of camera angles are what are kind of confusing here. My above mentioned topology could probably get exhausted trying to modify geometry by changing aspect ratio.
If everyone would request the Matlab code for this, maybe we could get them to release it. Being someone currently utilizing matlab for optical pattern recognition, this could be interesting.
xerox…
@za: I requested. I’ve seen research like this before though. It’ll probably see legal troubles before it even has a chance to be released.
It’ll end up like the Johns Hopkins University passive RFID research.
well before machine, that take one key and duplicate it. This is exactly how people did copy keys, look and copy
Ever heard of Abloy keys and locks?
Try hacking those from a picture.
Dunno why they are not used more as bumping would not work either.
There is a guy on ebay who will uplicat you a new VW car key from a photo. Apparently he has scripts that convert it to GCODE and loads it into a CNC machine. Nifty
In my misspent youth, I successfully copied keys after placing the originals on a sheet of photographic paper, and exposing it to light. The resulting image was then used as a template when filing down a blank.
Finally, some awesome hacks!
I concur, This is the sort of thing I used to come to HackADay to see. Pity it isn’t implemented on an arduino.. (read: I dont give a shit about arduinos)
What is even better- if it is an original key (i.e. not a copy) the pin numbers are stamped on the side of the key- at least for Weiser, Kwikset, Schlage and Baldwin locks- and the manufacturers are easily determined bu the shape of the key.
I worked at a hardware store for several years and these numbers are invaluable when rekeying a house full of locks that all need to use the same key (or for master keying/grand master keying locks in an apartment/office scenario)
tosspot – Learn to spell. Bloody typos.
Should be: “No-one gives a shit about arduinos.”
The problem with just picking up a key and duplicating it is that unless you get a picture of the side with the identifying number it’s difficult or impossible to find the correct keyway even if you can get the correct depths, which still need to be matched to a known key. To make a system like this work in the real world you would need to database reference points that can identify and scale common keys.
The easier method is to just grab reference points in your photo and skew them to match up with the template key, where you can get the depths by matching contrast in a single dimension. By nature of the transformation however, you’re losing a small amount of information. While this information may simply be redundant in a high resolution image, it’s important information when pixels are scarce.
For this reason, it’s better to vectorize the bitmap BEFORE transforming. You’re still just grabbing reference points and skewing them to a template, but if you vectorize first and skew second you’re not losing any information.
@dan take your VIN and go to a car dealer will net you a new key.
Many better locksmiths also have access to that database as well. It’s incredibly easy to get a key to a car, even someone elses car.
speaking of locksmiths and porsches, i locked my keys into an old 914. the locksmith didn’t need to look at the key. he just sat by the door and stuck the blank into the lock and wiggled it around. then pulled it back out and cut some groves with a small file by hand. after wasting 2 blanks he handed me the 3rd key that also worked better than the original. there is no replacement for true skill.
(CAPS?)
@max – called impressioning, easy in theory, and OMG I KNOW.
This is a neat hack, but I wrote a chook for mastercam x4 that traces pics and generates the gcode for cnc milling. The only problem is that the key has to be on a white background for the chook to work.
…combined with 3d-printing: :)
http://www.blendernation.com/german-hacker-3d-prints-dutch-police-handcuff-key/
“It’s a bit overkill to come up with an algorithmic solution since any sufficiently skilled locksmith can do the same thing without the technology, and can probably turn out the key more quickly.”
Exactly. As a fellow locksmith, any one with a little time in the trade can quickly, and easily, identify the depth of each cut of most keys, without actually measuring the depths.
To take pictures of a key, and use software to figure out those depths is stupid. Just get a micrometer if you can’t identify a key by looking at it.
Most guys in any related business (locksmith, crook, or spook) can identify a blank on sight, and the actual break heights for that blank are published – i.e. you don’t have to extrapolate the depth of each bit relative to the key, you only need to see them relative to one another to get the right breaks.
It really isn’t rocket surgery, just takes a little foreknowledge, and that is readily obtainable.
I dont understand why ‘flat’ type of keys so popular ? they can be braked so easily without any key at all(bumping known for decades) , all protection you get coming from neighbors that might hear someone braking yours lock. The ‘+’ type of lock much more secure and key physically wear less (did you ewer had situation flat key brakes inside the lock because it too old ?)
Dumb this down. Take a picture of a key you want to duplicate with your hand phone camera. Measure tooth-to-tooth distance on the original key. Then scale the hand phone pic to match the tooth-to-tooth distance when printing. Then get a blank key (not too difficult) then take out your hand file and have at it; matching the 1:1 dimensional image. I’m pretty sure there’s an “app” for a hand phone that displays a reasonably accurate ruler in inches or mm on you hand phone display; so you don’t have to carry a ruler or scale with you. Hmmm…
I can’t count the number of times I’ve thought about making a key from a high-res picture of it. I would’ve thought a camera-phone would be too low-detail to capture the picture at >5 feet even with a lens in front of it.
The weird thing – i had a lock rekeyed, and i asked the bit codes. the locksmith didn’t want to give to me.. i should do this to get the bit codes if i get locked out again.
From the comments and my own experience, the code to do this doesn’t need to be open source. The idea is out there already and it doesn’t take much more than just the idea to recreate the same result.
There aren’t any 100% secure locks. A lock only keeps an honest man honest but it does nothing to stop a determined criminal.
hi you’re all stupid keys being duplicated is a thing of the past the government can open any lock or door with an electro-magnetic key register
Electro-magnetic key register. OKIE DOKIE!
Electro-magnetic key register eh? Shame most lock pins are brass, and brass is notoriously NOT magnetic…..
Sounds like the mechanic forgot to reset the trouble code in the braking system computer. Take it back and have him do that. If it’s anything like some of the ABS modules-all that’s required is to wave a magnet over a certain part of the module that contains a reed switch. Others require an electronic reset with a scan tool.
Why not just run a blank through a 3d scanner? Hear me out… the vast majority of keys are the same depth. If I run a blank through a 3d scanner there are only 2 views where I cannot measure the depth. Now I have a known measurement to reference for the actual cutting and since each “view” will provide a slightly different measurement while scanning I take the depth measurement from my target picture search my scans for a match apply some high speed trig and violla. Key.
This statement is simply not true.
Bitting specifications for cylinder locks vary widely.
Add to this, angular cuts on some of the higher security locks and you would never be able to cut these keys using a photo. Cut-to-cut distances are not all the same between manufacturers. Neither is distance to first cut.
Bumping locks can be easily eliminated by taking away the physics involved in bumping in the first place. One way is to insert an anti-bump pin stack in one of the chambers. If you can’t impart energy uniformly to the ALL the bottom pins, at the same time, the drivers won’t all be lifted above the shear line. In this case, “two out of three” is bad! :)
Nitrous
Easily can be done using photoshop to scale as shown in youtube video – http://www.youtube.com/watch?v=SO0Y0HLvvpA
I needed a key for a 1940’s piggy bank that I had lost the key to. I found a picture of the key, scaled it to life-size, cut the key out, and now I have a working key. I wrote up a detailed tutorial on how others can do it too on my website: http://www.johnfixesstuff.com/2015/04/how-to-make-key-from-picture-how-to-make-add-o-bank-key.html
Photographic key duplication is a best way for cloning the keys. It is better than key cutting.