Ah, CSI. What other television show could present digital forensics with such two-bit dialogue?
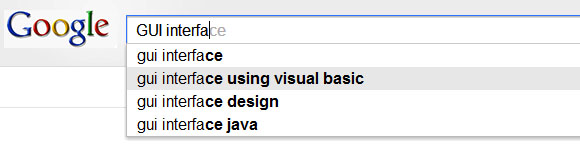
It’s time once again to put on your hacker hats – a red fedora, we guess – and tell us the worst hacker dialogue you’ve seen in movies or TV. We’ve seen a ton of shows and movies where writers and directors spend zero time doing any sort of research in whatever technology they’d like to show off in the story they’re trying to convey. Usually this results in lines like, “I’ll create a GUI interface using Visual Basic. See if I can track an IP address.” It’s technobabble at its best, and horribly misinformed at its worst.
We’re wondering what you, the readers of Hackaday, think are the worst examples of hacker lingo fails. Anything from, ‘Enhance!’ to the frightening real-life quote, “the Internet is not a big truck. It’s a series of tubes.”
We’ll compile your suggestions in a later post, but I’m betting something from Star Trek: Voyager will make the #1 technobabble/hacking lingo fails. There’s just too much in that show that isn’t internally consistent and doesn’t pay any heed to the laws of (fictional) physics. Warp 10, I’m looking at you. Of course there was the wonderful Habbo reference in last week’s Doctor Who, but I’m betting that was intentional as [Moffat] seems pretty up to speed on the tropes and memes of the Interwebs.
About a month ago, we asked you for your take on the worst hacking scenes ever shown on TV or film. The results made for good viewing, albeit with a surprising absence of Lawnmower Man. Now we want some dialogue to go with these horrendous hacking scenes. So, what say you, Hackaday? What are the worst hacking lingo fails you’ve seen or heard? Please be specific about what movie/TV show you’re referencing. Last time some good stuff probably slipped by because people just said a few words without context assuming we’d know exactly what they were referring to.
















The “frightening real-world quote” was from Senator Ted Stevens. I have no love for him, but I think he got more grief for that than he deserved. Engineers often speak of “sending data down the pipe”. In fact, Linux, Windows and other OSes have inter-process communication mechanisms called “pipes”.
It’s a metaphor, and it’s a metaphor I would readily use when explaining the internet to, say, my mother. Sure, Ted Stevens had a very shallow understanding of the internet. But he had an appropriate level of understanding for an 83 year old PoliSci major.
He was oddly right at a technical level. Every type of standards compliant cabling has a sheath, which can usually be removed. The internet really is a series of tubes. Just so happens the tubes have clad wiring or fiber within.
The obvious joke being networks are a series of cat tubes.
yeah, the doctor who uploading souls into “The WIFI” almost made me sick :(
thank you stephen moffat.
In Doctor Who’s defense, it’s not meant to be in any way realistic. They do very little technobabble, unless it’s time-machine related, and even there they end up with “wibbly wobbly timey-wimey” things.
He’s 1000 years old, has 2 hearts, travels in a space, time, and occasionally alternate universe machine, which is in the form of a police telephone box, his weapon of choice is a “sonic” screwdriver which can do basically anything by way of some sort of thought control at best, and he has battled everything from cybermen to cute ambulatory blobs of fat.
Uploading people to the wifi – all part of the day job.
Relax and go along for the ride.
Watch it again, pay close attention. That episode was loaded with jokes about “the cloud”. I am convinced Moffat is a bit of a nerd and wanted to take a jab at “the cloud”, but got lost in trying to make it presentable to non-nerds.
yeah, but the beginning really made me cringe. the moment i got the joke it was better, but really. “the wifi”? it really annoys me
In NCIS Season 10 Episode 14 where the prolific hacker has with ip address beginning with 192.168 (can’t find the exact address)
That’s probably a bit like 555-phone numbers. You don’t want anybody to say “hey, thats our IP. Someone hacked us because of the show, pay $alot”. Just not worth the hassle.
probably but it was still annoying lol
Variable $alot not found.Did you mean
$a_lot?http://hyperboleandahalf.blogspot.com/2010/04/alot-is-better-than-you-at-everything.html?m=1
He had spoken correctly.
Thanks for that, I needed a chuckle.
Easy workaround:
Just use the IP address of NSA.gov[1] and watch the scriptkiddies get whisked away in the middle of the night
[1] I daren’t run #host nsa.gov to find out their actual IP Address
Why not? Your browser does the same exact thing when you type nsa.gov into the address bar and hit Enter.
There’s also a scene somewhere in NCIS where one of them is watching a news stream from “127.0.0.1” on their phone.
at least that’s a valid IP address. In a movie I don’t remember (maybe Die Hard 4, not sure), the IP address was something like 352.263.42.553…
Just found 3 of them (not from the movie I was remembering): http://blog.haraldkraft.de/wp-content/uploads/2012/08/nikita_computer-gibberish_3.png, http://24.media.tumblr.com/9db522a0660cc08d3a01645ee42b04d9/tumblr_mfl5ij2rpD1r951fso1_r1_400.jpg and http://blog.haraldkraft.de/wp-content/uploads/2012/08/nikita_computer-gibberish_9.png
re: http://blog.haraldkraft.de/wp-content/uploads/2012/08/nikita_computer-gibberish_9.png
got to love the 5 section net masks lol
The ones in Nikita look so obvious that it seems like 555-555-1234 telephone numbers. Dodge just enough that a scriptkiddie doesn’t think ‘hey, let’s hack that computer and see if it’s part of an ARG”.
But the 3 part IP and 5 part mask does seem a bit out of place.
Maybe they’re using IPv5 :-p
Watching an Australian TV police drama, they did some computer bits and pieces and you got to see a raw IP for a split second. OK then pause show rewind, typeytypey blam up comes the shows website in the real world. Well done that man, gold friggin star. Rush I believe it was.
It’s not exactly hacking, but I’ve never seen animated bank transfers, if your account received a transaction, there’s never an animation counting the digits… You have to reload the page and there you go… And it’s like every bank transfer in movies…
My vote is for every movie that flicks through images of every fingerprint in the database, or every driver’s license photo while searching.
If you want realism, on the other hand, go rewatch “Day of the Jackal”, where the entire movie was built on the slowness of searching for information. While they collect hotel registration slips, the Jackal is about to check out, that kind of stuff. The movie would have ended in three minutes if SQL existed!
My favourite adapted-from-a-novel movie ever!
No kidding man. If transferring, logging in, copying, and pretty much everything on the computer popped up progress bars like the movies do I would go bat-shit-insane within a day. Not even back in 1995 when I was first introduced to a GUI interface for an OS was anything that freakishly slow outside of moving large files around.
http://www.youtube.com/watch?v=O2rGTXHvPCQ Numb3rs describes the Internet Relay Chat protocol, horrible, just horrible.
“Ah, yes, they’re running that “everything makes a f*cking beeping noise” interface that I’ve read so much about.”
XD
great captions too!
“Every” movie or TV show ever done that involves a counter of digits, and they make some sort of ‘clicking’ noise, like a ratchet mechanism. That, and tires that screech on a dirt road (but that’s a different story!).
And whenever a vehicle is going in a perfectly straight line the driver is always rocking the steering wheel left & right like they’re navigating some sort of invisible slalom course…
I cringe every time someone defeats an electronic lock by taking the faceplate off and hooking up some device that defeats the lock one digit at a time. And of course, before the digits are “hacked”, they run quickly through all the numbers before locking in place with an ominous beep.
Brute forcing anything should trigger automatic lockout on all but very old or badly designed login / other access systems. this one at a time getting the right one moving on stuff is a joke at best what system would tell a user that just failed to get the correct code what characters were correct in there attempt these systems are designed to keep people out.
what they should do to the door is disconnect it from the rest of the system then activate its debug mod and use the generic code to open the door or just connect power directly to the mechanism that opens the device.
Did exactly that in a Scott Bakula pilot episode that didn’t get picked up. (Was done between Quantum Leap and Eisenhower & Lutz) He busted open the keypad and applied power directly to the lock motor or solenoid. I think it would’ve made a good show, he played a scientist at Stuart Institute of Technology (SIT) working on teleportation and accidentally merged himself with a robotic space probe. When he was in danger he’d start morphing into a robot.
I bet someone at a screening said it was too much like the incredible hulk and that scuttled the series.
What series was that ?
So Return of the Jedi did it right.
These sort of hacks are real. In a system that compares a string to another, incorrect strings might return false as soon as the first character is wrong. Measure the time before the response and you can determine when the response time is longer – one of the characters is correct. Theres many papers about this, its even doable over ethernet in small networks if the software is crap.
http://en.wikipedia.org/wiki/Timing_attack
Yeah, that’s so unrealistic. In reality, it’s far easier than that to gain illegitimate access to many hotel rooms:
http://boingboing.net/2012/08/03/howto-open-an-electronic-hotel.html
The ultimate is Bruce Willis defeating the unbreakable lock in the movie RED at the CIA headquarters. I thought of all the other lock hacking movies when i saw that..
The latest episode of the tv-show Grimm had a computer savvy villain. The good guys try to track him down using a list of possible names to match against usernames for an online game server. Cut to shots of the heroes restlessly waiting while a computer scroll down two lists of text at a snails pace. The guy setting up the search then says “I’m sorry this is taking so long but… 221 names to check against the THOUSANDS playing”, portraying that as a very time consuming task for the state of the art looking computer to pull off.
The thing that bugged me about that wasn’t the time but the efficiency of what they were doing. They didn’t need to check it against the list of names, just check if it contained the letters they were looking for (the 221 names were generated by using combinations of a set of letter they started with). Been doing lots of performance stuff at work lately….
https://xkcd.com/208/
It’s hard to pick on some of theses, because they use things like animations and sound FX to keep an audience interested. It’s also entirely possible the writers knew exactly how the things worked, but altered them for drama and or the lowest common denominator. Or for plot devices.
And that’s the thing, movies have to be exciting and for the most part reality is boring.
My favourite is undoubtedly in “Independence Day” when Jeff Goldblum uses a Netware client to hack into the alien mother-ship’s central computer.
Of course, this might just be a critique of Novell…
[obligatory reply about this being explained in a deleted scene where we’re shown how our computers derive from alien tech from Area 51 crash and so systems are not dissimilar]
That just makes it even more painful… The most flexible hardware and software architecture in the universe, and we create a plethora of platforms based on that, that hardly communicate with each other.
If that was the underpinnings of our technology, then you’d install OSX on a toaster by accident.
Pretty sure toasters existed before the Area 51 crash, so not sure that makes sense
Okay, Allright….. IOS on a HTC then..
The fact that it was deleted makes it even WORSE surely?
Well Netware really IS super easy to administer….
You know I never really had a problem with being able to “hack” their computers, I mean a fresh perspective on a problem will often reveal interesting security holes in a supposedly secure system. Given an alien mindset perhaps they were more keen on defending from outside, an internal threat not even being considered. As for the hack itself, whilst the actual screens themselves may have been overly Hollywood the underlying premise seems valid. I mean how much more alien could their computer be compared to some of the weirdass computers architectures we have come up with. As such (and given 50 odd years of research) having an emulator and interfaces seems pretty reasonable to me.
http://us.norton.com/cybergeddon/ comes to mind
NCIS:
Tony: Oh, twenty bucks says McGee’s about to say something nobody understands again.
McGee: The GPS coordinates came bundled in a proprietary packet. Since it was a beta, I thought-
Gibbs: I’m starting to think you can’t help yourself, McGee.
You know what’s funny. I really do say things nobody understands all the time which actually make sense if your not a complete moron with computers. I get flak for it a lot. Maybe I should change my name to McGee.
Going way back – how come they can make a humanoid form robot that speaks 9 bazillion languages (C3PO) yet can’t somehow find the space to wedge a single language chip into the trashcan bot (R2D2).
R2D2 lines were all bleeped out b/c of his foul language
http://www.youtube.com/watch?v=BNtcWpY4YLY “Do you know anything about hackers? Can you jam with the console cowboys in cyberspace?” I’m surprised no one else mentioned it yet…
Neuromancer referenced in a kid show?
That’s why you should fund public TV.
That’s a young Julia Stiles. I thought she looked really familiar but it took me a while to place the face.
http://xkcd.com/130/
Perfect reaction at the end. “What?”
“I’ll create a GUI interface using Visual Basic. See if I can track an IP address.”
Though is may not be the best solution to the problem, and of course it is TV hype, poor at best, but the concept is not altogether out of line.
http://guivbip.codeplex.com/wikipage?title=Screen%20Shots&referringTitle=Home
Brilliant!
The entire movie “Hackers”. enough said.
The “lingo” really isn’t that bad. RISC *is* good and it did change everything.
Play with the best, die like the rest.
“killer refresh rate”
In Dutch “rate” is phonetically similar to our word “reet” which is a vulgar term for ones bottom. “Killer refresh reet” is particularly funny in most situations round here.
One day I”ve seen a scene from “The Bold and the Beautiful” that one of the guy ask the other a RJ45 cable. the other says: “wow you know a lot about computers.”
The infamous cringe-worthy “peer hacking” scene from NCIS takes the cake for me : http://www.youtube.com/watch?v=u8qgehH3kEQ
Dang! You beat me to that, Vic! That one may be my favorite because it’s not even technobabble. Anyone who’s used a computer knows you can’t just share a keyboard like that, it’s patently insane. I really believe that was included just to win a bet that they couldn’t oneup the gui in visual basic line.
Also, don’t forget anything in swordfish.
Wait, so other people don’t practice spooning. https://www.youtube.com/watch?v=dYBjVTMUQY0
Pretty much everything “Rat” does in The Core including the file search for keywords and sending electricity to Coney Island.
Jurassic Park, “This is Unix! I know this!” and then with the ‘advanced’ 3D interface manages to fix the door locks and she’s what, 13? Sure. let’s roll with that.
Side note, we did add in a cleaned up sample of the “ah ah ah you didn’t say the magic word” gif into a project as an error message. That is some priceless movie computer stuff right there.
http://gifsoup.com/view/1349477/ah-ah-ah.html
There was a reply to a similar post the other day explaining this was an actual interface at the time, though it was viewed more as a novelty.
It is real. SGI File System Navigator. Ran on IRIX. Oddly enough, there really is some access point control software packages that are comparable at a low level and can be used just as in the movie scene to unlock doors. It is incredibly annoying to do it via command line (or a shell) though and it is far easier to use the built in webserver.
In Super Troopers, there’s a scene where Ramathorne is supposed to print a still from a security feed and is just meaninglessly tapping on the keys and saying “Enhance” until Brian Cox gets pissed and says “oh, just print the damn picture”. Bad on purpose, and wonderful for it.
Same goes for “PDF format”.
Someone should invent some sort of portable PDF document format.
Film and TV script writers clearly don’t have a clue how GPS works. Many shows assume that the GPS satellites know where the satnav/phone is and can be used to track it. And some shows even use the word GPS as synonymous with coordinates.
A few weeks a go a student at my university asked how the GPS Satellites manage to handle all those GPS-Devices and if they don’t run out of capacity… Since then I believe many people actually know a lot less about GPS then I thought…
Nothing is immune, not even comics! http://24.media.tumblr.com/tumblr_lv4nb3IVxS1r4p6t9o1_400.jpg
Wow, that’s really bad. DC comics are full of completely absurd dialogue, but some stuff still surprises me.
I remember a scene from a little known (and B or even C grade) TV series in the first episode where some asks after a hacker had hacked into their system: “How did they get past our asymmetric encryption?”
http://www.imdb.com/title/tt1865640/synopsis
Every time you log into an SSH server using public/private key encryption, you’re using asymmetric encryption. The answer to the question “how did they get past it” is probably “Well, Paul forgot to disable password logins, and the root password was ‘changeme’.”
Anything from The Mangler 2. Anyone besides me remember that movie? Yea… Didn’t think so.
While trying to find the quote from CSI Episode “Grave Danger”, while watching a streaming video states something along the lines of “we can’t trace it because it is an encrypted ip address” well I just realized that I couldn’t trace it either “http : / / 183.172.201.254.5/vid/index.asp” [ http://www.youtube.com/watch?v=Mch9L5Bb-TU at 0:54]
Too many octets.
At least they only used numbers under 255…
just in case you wanted to know, 183.172.201.254 is
Tsinghua University
CN
CERNET
Beijing 100084, China
Brave Little Toaster Saves The Day – just the whole movie. XD
Replacing one tube actually makes the remainder of the damaged machine regrow. lol
GUI interface
ATM machine
HIV virus
The ‘microdogs’ scene in the first episode of Seaquest DSV. Genius hacker kid and squeaky voiced dolphin, sooooooo annoying.
Pretty much all of the science in Seaquest was techno babble
I’ve been watching Seaquest on Netflix and some of the wrtting is down right painful to listen to. I realize it’s supposed to be the “future” but they’d go from perfectly legitmate (and accurate) hyrdronamics to utter jibberish and back in the same sentence. The “hacking” done by the character Lucas was on the same level of sliliness as the movie hackers. Minus the VR headsets.
Yet another annoying thing with depictions of computers on TV well into the 1990’s, they almost always used a constant beep beep beep sound effect, sounding much like the head actuator on old Seagate MFM hard drives, which made the sound irregularly and only during head moves.
There’s a scene in two part crossover of Magnum P.I. and Murder She Wrote where a guy is repeatedly tapping a key on a PC keyboard, as if he’s paging through a document, but the computer isn’t turned on. Monitor is aimed right at the camera, nothing on the screen and no power LEDs lit.
There’s an episode of Riptide where they three guys are hired as consultants to a TV show and their intro to the cast is an obvious parody of all the stupid impossible BS done with computers and crime solving.
The use of the words firewall and mainframe anywhere on TV or in the movies.
I forgot about this.
http://tvtropes.org/pmwiki/pmwiki.php/Main/HollywoodHacking
NCIS Devil’s Triangle
“I have to inform our entire data services department that we’re officially switching to dual layer backup DVD medium!” Yep, dual layer dvd backups for your huge server farm. That’ll only take a few warehouses full of DVDs.
Screens that are apparently blinding the person as they project in perfect focus onto their face.
i forgot to post this last time, enjoy:
http://www.youtube.com/watch?v=o8oSOKeWlK4
On “any” movies, secret/spy devices (sound recorders, cams, detonators) put below tables/doors/lockers and so on. But all those devices have blinking leds to show they are ON. But a => hidden <= device with a blinking led ??? Hmmmmm…..
“Reverse the polarity of the neutron flow” – A classic line from the classic Doctor Who Series
Do whitehosue statements or c-span stuff count? ;)
Heat sync. ;-)
Best STNG technobabble.
LaForge: “Commander, the transporter is still online. It’s being fed
power from the auxilliary systems.”
Riker: “The rematerialization subroutine has been disabled.”
LaForge: “Yeah, and that’s not all. The phase inducers are connected to
the emitter array, the override is completely gone, and…pattern
buffer’s been locked into a continuous diagnostic cycle.”
Riker: “This doesn’t make any sense. Locking the unit into a diagnostic
mode just sends the matter array through the pattern buffer. Why would anyone – ”
LaForge: “There’s a pattern in the buffer still.”
Riker: “It’s completely intact. There’s less than .003% signal
degradation. How is that possible?”
i’m pretty sure swordfish had an escalating bit encryption scene, e.g “128 … not 256 …. 512 … etc.
There’s some REALLY bad hacking lingo in Criminal Minds. This is the best:
Garcia: “The information superhighway is closed. Someone had the nerve to run a black hat op into my computers, Morgan. They hacked me, okay? But you can bet your sweet ass I will find them. I’ve got honeypot farms hidden behind UML kernel data packets and a first generation honeynet I personally programmed. My snort-log lists every visitor, every server request, every keystroke of this entire network. If I have to back-hack his IP all the way to the freakin’ stone age I will find this son of a *****, okay? So, bye!”
saw in a b-movie a hacker coding a antivirus for a sentient virus that had spread alle over the world on A GAMEBOY ADVANCE.
I’m sure I saw that movie, I thought it was a game boy color that saved the day in the end…. Tragic
totally
An episode of Star Trek Voyager where they were trapped in a gravity well and decided to use their phasers to “punch through the event horizon.” The event horizon is a line on a map! Good thing they weren’t on Earth, otherwise latitude would be in trouble!
Here’s one which is mechanical hacking related. In Mad Max, his 600HP Ford Falcon GT coupe has a supercharger sticking out of the bonnet (hood). The belt only starts spinning when he engages it. A supercharger clutch is connected to the supercharger itself, so the belt will keep spinning even when it’s disengaged. In the commentary it’s revealed they had to use a starter motor to turn the supercharger in that scene.