[HD Moore] recently posted an article on Rapid 7’s blog about an interesting security problem. They’ve been doing some research into the security of automated tank gauges (ATGs). These devices are used at gas stations and perform various functions including monitoring fuel levels, tracking deliveries, or raising alarms. [Moore] says that ATGs are used at nearly every fueling station in the United States, but they are also used internationally. It turns out these things are often not secured properly.
Many ATG’s have a built-in serial port for programming and monitoring. Some systems also have a TCP/IP card, or even a serial to TCP/IP adapter. These cards allow technicians to monitor the system remotely. The most common TCP port used in these systems is port 10001. Some of these systems have the ability to be password protected, but Rapid 7’s findings indicate that many of them are left wide open.
The vulnerability was initial reported to Rapid 7 by [Jack Chadowitz]. He discovered the problem due to his work within the industry and developed his own web portal to help people test their own systems. [Jack] approached Rapid 7 for assistance in investigating the issue on a much larger scale.
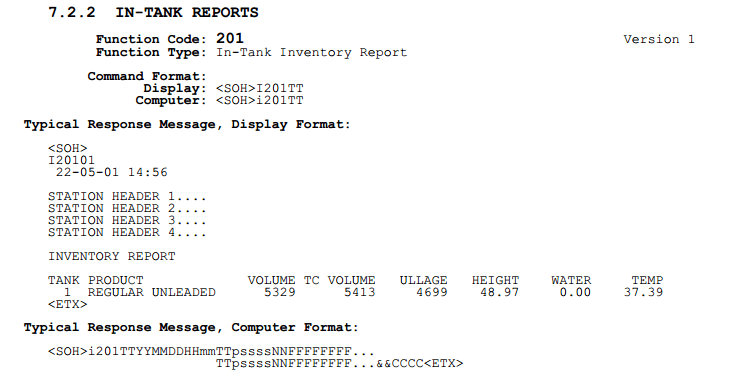
Rapid 7 then scanned every IPv4 address looking for systems with an open port 10001. Each live system discovered was then sent a “Get In-Tank Inventory Report” request. Any system vulnerable to attack would respond with the station name, address, number of tanks, and fuel types. The scan found approximately 5,800 systems online with no password set. Over 5,300 of these stations are in the United States.
Rapid 7 believes that attackers may be able to perform such functions as to reconfigure alarm thresholds, reset the system, or otherwise disrupt operation of the fuel tank. An attacker might be able to simulate false conditions that would shut down the fuel tank, making it unavailable for use. Rapid 7 does not believe this vulnerability is actively being exploited in the wild, but they caution that it would be difficult to tell the difference between an attack and a system failure. They recommend companies hide their systems behind a VPN for an additional layer of security.
[Thanks Ellery]
















no free gas?
Yawn
I used to work in the fuel management industry for private industry and government installations, and you’d be amazed how easily you can connect to them and start issuing AT commands through a serial connection to do your will. Some of which are connected to an Ethernet connection through another equally unsecured serial to Ethernet device server.
I should have mentioned that I’m speaking of the fuel dispensers themselves. It isn’t just the ATGs that are susceptible.
Disclosing attack vectors now? There is a point to this behavior but the color of the hat is in question… so many shades of gray, and purple, and orange…
White is white.
Pushing the line. Really pushing the line.
Editorial responsibility.
So the attack vector is made known? And what would an attacker do that can cause serious problems for the owner of an ATG equipped tank? Shut it down until a technician walks over and manually resets the device, or God forbid force them to use a measuring stick to verify the tank level correlates with the ATG’s reading?
We are not talking about missile launch systems here.
The ATG manufacturer is probably not going to concern themselves if one person approaches them with a discovered vulnerability. Only by making the exploit publicly available and with many people “hacking” the tanks for shits and giggles might the manufacturer possibly consider securing a product that they should’ve secured ages ago.
Hoooyy You! Didn’t you get the memo from like last century or so?
It was a Fax and it said:
Responsibility is for Losers, Bailouts are for Winners!
You see: Nothing gets fixed, or improved, or even maintained EVER, here in the de-regulated, de-supervised and de-criminalized corp-rat-istan, that we call “western democracy”. Unless pain, shame and inconvenience hits the “decision-makers” personally; The government won’t do it, the police is busy policing black folks – the only option left is Private Entrepreneurship. Activism.
When we see “How to get free fuel in seven steps” on PasteBin – and Exxon is a few ppm short in their hourly profit report, Then security will suddenly be better than Fort Knox in 6 weeks time. Being “responsible” just gives them time … to slap you with threats of Legal Action, DMCA takedowns and to call you a Terrorist.
You see: Nothing gets fixed, or improved, or even maintained EVER, here in the de-regulated, de-supervised and de-criminalized corp-rat-istan, that we call “western democracy”. Unless pain, shame and inconvenience hits the “decision-makers” personally; The government won’t do it, the police is busy policing
That’s how it should be. If you don’t like the way a company works, quit using them. If enough people quit using them it hurts their pocketbook and they change. I don’t need the government to regulate things for me. The government’s big enough and overstretches as it is.
“If you don’t like the way a company works, quit using them”
Sorry to burst your libertarian fantasy bubble, but that’s completely infeasible in modern society especially for commodities with inelastic demand and commodities who manufacture is effectively monopolized (petroleum products, for example).
I don’t like how Monsanto does things, so I should grow my own food? How would that hurt Monsanto? Few people can grow enough food to sustain themselves, not everyone has enough land, etc.
Not infeasible at all, it’s all in how bad you care. I didn’t like the way Apple worked, never bought a iphone or ipod. Neither did others now we have Android. Don’t like the petroleum industry? By an electric car or a bike. You don’t have to grow your own food, visit your local farmer’s market. There’s always a way if you are willing.
This wasn’t about the petroleum industry, but about all the gas stations buying their metering system from the same manufacturer. I wonder if anyone even asked if this thing had security, or if it was a “this is what everyone else is using” type approach. Unless it is regulated (if so where is the regulation working now?), there are several people who visit this site who could build a better product. No monopoly required.
Nothing gets fixed because they’re so over-regulated and taxed that they don’t have a large enough profit margin to reinvest into making their core business any better.Why bother when the feds just take it all anyway.
You think oil companies have a small profit margin? LOL
And you blame taxes?? L M A O
Hahaha, wow man, look up would you please. Consult the SEC filings on the profits and salaries of those people and you’ll find what’s its like to make every month what upper class middle Americans make in a year
Anyone who would describe the U.S. as ” de-regulated, de-supervised and de-criminalized ” is seriously out-of-touch with reality. Maybe you should spend less time reading blogs and get out into the real world.
I do so invite rebuttal… BUT… white is white… white uncovering an exploit so publicly isn’t really white, it is coercion and controlling. White is white because of clear soul taking the time through channels to never publicly divulge the exploit so needed time to plug the hole is granted graciously. There will always be holes, there will always be fixes… there is no need for those that exploit to be informed and granted time too.
I reject your arguments. What you do is what YOU do. Do it with forethought and concern for your soul. White IS white. Anything lesser is lesser.
I reject your rejection out in the real world of security management by lowest budgets and accountants ignoring specialist inputs.
From the article :-
“He discovered the problem due to his work within the industry and developed his own web portal to help people test their own systems. ”
Reads like not only did the guy discover and raise it within his industry, he also made tools so people could test for themselves and generally made aware.
I suspect working in a similar field and seeing it daily, the response of the suppliers of said systems was a giant meh at best, and no response at all at worst, until someone comes along to FORCE them to invest to do the job how it should have been done in the first place.
I have been working with vendors to fix security flaws in their products myself, some of which go back years, and if I weren’t in the employ of a specialist supplying this service and under strict NDA I would take the same name and shame route to force their hand they are being so lackadasical in their duty and whole approach. I don’t bite the hand that feeds because Ive undertaken to do so, but I agree fully with this person’s approach.
You will find the tech guys actually get the issues when you show them, but some management type does a risk analysis that they are not qualified to undertake and decides its worth the risk, until it becomes public knowledge.
And we give people like this the keys to steer the ship…
Whats soul got to do with it…
At any rate, most of these sorts of public disclosures are only done after the white/gray had discussed with the concerned industry and given them a reasonable amount of time to fix the problem. Often industries simply ignore the facts. At which time the researcher then issues a “30 day warning” or some specific amount of time before going public. Often just the threat of public disclosure forces the hand of the companies involved to fix the problem BEFORE the public disclosure date.
But white hats still have the public RESPONSIBILITY to divulge vulnerability scenarios as a security community educational exercise. If the target company continues to ignore the research, ignore the fact that a researcher only has so much time to keep it quite, and continues to ignore their vulnerabilities, then the problem lies with the company. Not the researcher. No crisp white hats are dirtied in such a case.
So, what you SHOULD be asking Biomed, and the only question that is really relevant, is: “was the industry given ample time to fix the issue before Rapid 7 posted his blog?” A possibly legitimate follow up question might be “how was ‘ample time’ defined, and how much time was actually given.” But the most important question is “Did they bother to fix the problem once it was discovered?”
A quick scan of the blog post makes it clear: The vulnerability was detected and the scan made early in January of 2014. LAST YEAR (caps just so there is no confusion). BUT!! The catalyst for the the scan was that two people IN THE INDUSTRY had already long since noticed the trend. So, it is safe to assume the industry had at least some knowledge of the problem before 2014.
The blog post was put up January 22 of 2015 (this year). So, the industry had AT LEAST 12 months to roll out a solution. Probably more like 16 months.
Hmmm. No. White is the addonim from the old western tv shows. The good guy always wore the white hat, and the bad guy always wore a black hat. So if you don’t do it for anything but moral intentions, and no mistakes its white, if you do bad things but for moral intentions is grey, if you do bad things for lulz or money, its black. Very, very, very, very rarely are hacks white hat, because the nature of a hack requires subversion, manipulation, and doing something that inherently causes problems, albeit a lot of times for the greater good. Therefore 99% of all released hacks is grey hat. Anyone that does it for money is black hat. White hat really is only if in defense of an attack you defend with a hack, so pretty much never.
Its not really an exploit, it’s just 5800 people who didn’t bother to set a password on their device. Not to mention if he actually scanned the entire ipv4 range, 5800 affected devices is a very small percentage.
+1
Or do something simple like change port numbers. Sounds like to me the problem is not in the system, but in the installation and usage.
About as smart as the people that leave the passwords on their routers set as “admin”
That’s not really describing a specific attach vector. It’s pointing out something that is available in a security forum and proposing a solution. If they posted a study that says “53% of households in Minnesota do not lock their doors at night.”, would you blame them for the rash of burglaries? Or burglars arrested for attempted burglary? Or rather that it would teach people to lock their doors and point out to people that they cannot rely on security through ignorance, laziness, and luck to feel safe?
Given that the scan was performed a year ago, it would be very interesting to perform the scan again and compare the results in order to assess how well the industry responded.
I see several ways in which this could be used to perform criminal acts: The most obvious is modifying calibration so deliveries show greater volume than actual, leading to greater payment to a supplier. This would, undoubtedly, lead to follow up questions why the pumpout totals don’t match delivery, and the associated costs of looking for a leak, if nobody thought to use the stick…. Several other come to mind that could be applicable to the general public.
This was my thought as well, but I’m assuming that filling stations and suppliers have long-term relationships. Would a supplier risk that for a one-time gain?
I am assuming that the pumps themselves have their own metering hardware not susceptible to this.
Well… if you know the guy down the road was vulnerable, you might be tempted to keep knocking his pumps offline to steal his trade. Just because I can’t think of anything particularly devious to do with this particular vulnerability doesn’t mean somebody smarter or more devious than you or me wont think of one… now what was that port number again }:¬)
“Rapid 7 does not believe this vulnerability is actively being exploited “. At least not until now…
“Rapid 7 believes that attackers may be able to perform such functions as to reconfigure alarm thresholds, reset the system, or otherwise disrupt operation of the fuel tank.”
So there may or may not be an actual problem.
Many industrial systems I’ve had the opportunity to play with have a dual password scheme. One to get in and look around, which may be left blank since you can’t hurt anything. Another is required to actually change anything, and must be entered at the time you request a change, kind of like going “sudo” in Linux. Often the end user doesn’t have this password, as the system is meant to be configured ONLY by the company that provides it, as they are the only ones qualified (or legally permitted) to do so. Even that’s assuming the reporting and configuration interfaces are the same. For all we know, configuration in this case might be possible only through DIP switches behind a locked panel, by plugging in a USB memory stick with a certain file on it, or other methods which require direct physical access.
Now if [Rapid 7] had claimed he was able to remotely change an alarm threshold (even an harmless and insignificant amount) or perform a reset, THEN this could properly be called a security problem. Instead he only says he “believes” it could be done. Leaving readers with the impression that this is a serious issue which could be easily exploited, when in fact it’s left completely vague whether this is actually true.
Was this vagueness intentional? [Rapid 7] says he was asked to look into this by [Jack Chadowitz]. Jack founded a company called Kachoolie. The first line of text on their website is. “Providing low cost, reliable, and SECURE tank gauge access.” They sell serial-to-Internet adapters with encryption. Kachoolie’s mother company, BostonBase Inc., also provides connectivity and remote monitoring software for fuel tanks.
So if Kachoolie can get an “independent” security researcher to publish a report that makes this sound like a problem, regardless of whether it is or not, they stand to profit. Especially if that report is then picked up by other sites. I suspect HAD has been had, for some free advertising.
HAD needs a comment system like reddit. This comment needs an upvote!
HaD + Reddit, that would indeed be awesome! [upvotes]
Almost 9 years later and my local gas station has this hole still wide open. Shodan still reports my local stations fuel tank levels. Interesting enough they only show unleaded, diesel, and premium levels. Makes you wonder if that midgrade is just regular at an inflated price. Hmmm?