Summer is nearly here, and with that comes the preparations for the largest gathering of security researchers on the planet. In early August, researchers, geeks, nerds, and other extremely cool people will descend upon the high desert of Las Vegas, Nevada to discuss the vulnerabilities of software, the exploits of hardware, and the questionable activities of government entities. This is Black Hat and DEF CON, when taken together it’s the largest security conference on the planet.
These conferences serve a very important purpose. Unlike academia, security professionals don’t make a name for themselves by publishing in journals. The pecking order of the security world is determined at these talks. The best talks, and the best media coverage command higher consultancy fees. It’s an economy, and of course there will always be people ready to game the system.
Like academia, these talks are peer-reviewed. Press releases given before the talks are not, and between the knowledge of security researchers and the tech press is network security theatre. In this network security theatre, you don’t really need an interesting exploit, technique, or device, you just need to convince the right people you have one.
ProxyHam
The clearest example of security researchers using the media and lifestyle blogs to increase their presence at a security conference is ProxyHam. This talk, planned then cancelled for DEF CON 23, laid the groundwork for an online anonymity box that would keep anyone secure from NSA snooping and balaclava-wearing foes.
ProxyHam, the creation of [Ben Caudill] of Rhino Security, was first released to the world through a Wired article that promised an easy way to maintain anonymity online using off-the-shelf 900MHz network bridges. By placing one end of a network bridge in a public place – a Starbucks or public library, for example – anyone could tap into that WiFi signal from miles away. “The KGB isn’t kicking in your door,” the article promised, “They’re kicking in the door of the library 2.5 miles away.”
Just two weeks later, [Ben Caudill] announced ProxyHam would not make a showing at DEF CON. The talk was cancelled, the release was cancelled, and the source destroyed. The Internet then went insane. Speculation ranged from national security letters, falling into the hands of nefarious FCC bureaucrats, gag orders, to vague threats from federal prosecutors.
Some people find comfort in a persecution complex, and there’s nothing more intriguing than vague references to the government silencing speech. The case of ProxyHam was far more interesting: instead of hacking a few 900MHz network bridges and a Raspberry Pi, [Ben Caudill] hacked the media. [Ben] was very careful not to give anyone a reason on why he cancelled his talk, allowing speculation to run rampant through the Twitterverse and Blogosphere.
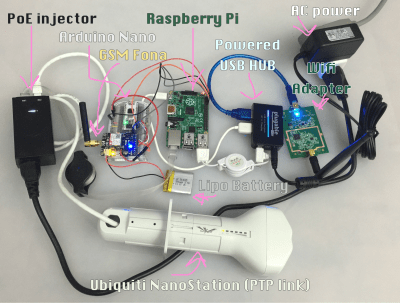
The simpler, more reasonable, and only probable reason why the ProxyHam talk was cancelled was far more mundane. ProxyHam just sucked. You can build one yourself on Newegg. It doesn’t make you secure; a burner laptop would do far more for your online anonymity than a four-foot long antenna would.
Just a few days after the ProxyHam cancellation was announced to an eager press, [Samy Kamkar] released a version of ProxyHam that actually works over 2G cellular connections. In the wake of a cancelled DEF CON talk, [Dave Maynor] and [Robert Graham] of Errata Security put together the proxy for ProxyHam that worked under the noise floor.
In two weeks, ProxyHam was duplicated by several independent researchers and two improved implementations were created. Both are exceptional feats of research and engineering. Now ask yourself: who got the most media attention, has more search results when Googling their name, and can now command higher consult fees? This is network security theatre, and the inevitable result of a world where charisma is not a dump stat.
Wait, apps have permissions?
Just days before Black Hat 2011, news thundered across the Internet that smartphones were vulnerable to attack through rogue apps. [Riley Hassell] and [Shane Macaulay] from Privateer Labs were set to give a talk at Black Hat on the brave new world of apps and permissions in the up and coming Android OS.
Two attacks were set to be presented at Black Hat. The first, AppPhishing, inserted a fake login screen on top of a second app. If an attacker wanted your Facebook login, the attack would detect when the Facebook app was launched, and display a pop-up asking the user to log in. These credentials would then be sent off to regions and persons unknown.
 The second attack, AppJacking, didn’t target an app to steal a login. Instead, a custom application would hijack an application for unintended activities. Any app downloaded to the phone could send a text message, place a phone call, or serve as a single node in a vast, mobile botnet. Scary stuff.
The second attack, AppJacking, didn’t target an app to steal a login. Instead, a custom application would hijack an application for unintended activities. Any app downloaded to the phone could send a text message, place a phone call, or serve as a single node in a vast, mobile botnet. Scary stuff.
Even though the talk, “Hacking Androids for Profit” was slated for Black Hat 2011, [Riley] and [Shane] were a no-show. Why? The official reason was, “To prevent an unacceptable window of risk to consumers worldwide and to guarantee credit where it was due.” According to Google, “the identified bugs are not present in Android.”
While [Riley] did go on to give the same talk at Hack In The Box 2011 just months after bailing on Black Hat, his research did not make an impact on the architecture of Android. The same vulnerabilities were rediscovered in 2014, heavily suggesting there was little risk to consumers worldwide.
I’m Spartacus Satoshi
Bitcoin was invented in 2008, and since then has become the most popular cryptocurrency. The importance of Bitcoin cannot be understated — it is the solution to the Byzantine Generals’ problem, the idea of a blockchain will revolutionize several fields, and the very fact that every single unit of currency and transaction in an economy can be accounted for provides the greatest wealth of economic research since World of Warcraft and Eve Online.
Bitcoin was invented by [Satoshi Nakamoto], an alias for someone, but we have no idea who. Because every individual coin can be tracked, and because [Satoshi] mined the first coins, there’s a very easy way for [Satoshi] to prove his identity: either show off the Bitcoin wallet, or spend a few of the first Bitcoins.
As far as fact checking and confirmation goes, it doesn’t get any easier than this. If someone claims to be [Satoshi], all they need to do is transfer a few Bitcoin to a wallet, or sign something with [Satoshi]’s private key. Guaranteeing a message comes from a specific person is pretty much the entire point of Bitcoin, anyway. This hasn’t stopped anyone from claiming to be [Satoshi] without providing this proof, and it hasn’t stopped journalists from enabling these people.
 The highest-profile [Satoshi] claim came from Newsweek, who apparently found someone born with the name ‘Satoshi Nakamoto’. No effort to confirm this [Satoshi]’s identity – either through blockchain analysis, or by asking the subject of this interview if he had created Bitcoin – was done.
The highest-profile [Satoshi] claim came from Newsweek, who apparently found someone born with the name ‘Satoshi Nakamoto’. No effort to confirm this [Satoshi]’s identity – either through blockchain analysis, or by asking the subject of this interview if he had created Bitcoin – was done.
While the (real, non-pseudonymous) [Satoshi Nakamoto] was caught up in something he didn’t understand, other Bitcoin insiders have been more than willing to fill (the Bitcoin creator) [Satoshi]’s shoes. In December of 2015, Wired announced the creator of Bitcoin was actually [Craig Steven Wright], an Australian academic who, in 2008, wrote several blog posts introducing Bitcoin to the world. This was the proof used to peg [Wright] as [Satoshi]. This is impossible, because we all know I invented Bitcoin in 2006.
The Bitcoin community rolled its eyes once again, waiting for [Wright] to move some of the original [Satoshi] coins, or sign a transaction. Journalists from the BBC and The Economist did witness a demonstration of [Wright] appearing to sign something using [Satoshi]’s signature, but this was a scam. [Wright] provided just enough evidence of being [Satoshi] to last three minutes of scrutiny. Anything more, and the whole scam comes tumbling down, but not before a few articles are published and [Wright] gets the fame he so desperately wanted.
We should move this to Broadway
Black Hat and DEF CON are where reputations are made. Sometimes, it happens at peppercon, sometimes it happens rappelling off a hotel. For the security researchers, reputations are made by giving talks. This may get you a mention in a middlebrow tech blog. There is one way to guarantee coverage: bail on the talk. You can just simply lie, too.
The fascination with security breaches, privacy devices, or scary electronic baubles keeping you safe from a boogieman will not stop, and as long as the incentive to make a name for yourself, the network security theatre will go on. In the next few weeks, you’re going to see a lot of media coverage on talks planned for DEF CON and Black Hat. Don’t pay any attention to that. The schedules for both events will be released soon. Just read those and you’ll be fine.

















Interesting take on gaming the system around the system. It’s kind of meta. Good use of a time machine too!
“Summer is nearly here”
The solstice is TODAY. Cant Benchoff get anything right? It’s the first line, and it’s crap.
Probably he was writing it piece by piece, and finished today. That line would be perfect fine a week ago. And I don’t care about details. And the article is good.
Sorry to have to point out that you are the one that is wrong and Brian is correct.
Today is the solstice but it hasn’t happened (at least not in the US where Brian lives). That will come in a few hours. So you see, summer *IS* nearly here.
“at least not in the US”
You are correct that the solstice hasn’t happened yet, but it’s a point in time and has nothing to do with what country you live in.
Haha
Silly Rabbit, [Satoshi Nakamoto] is a hacker group. j/k but many darknet blogs suggest this. What makes the concept of using blockchains as a chain of trust is the shear amount of applicable areas this can be applied to. Probably all the way down to the boot process on hardwares. Security should be like an onion, many layers. Blockchain being one of them.
Psst, the Defcon 24 schedule already dropped @ https://defcon.org/html/defcon-24/dc-24-schedule.html