In some ways, we’ve become a little jaded when it comes to news from Mars, which almost always has to do with the Ingenuity helicopter completing yet another successful flight. And so it was with the report of flight number 54 — almost. It turns out that the previous flight, which was conducted on July 22, suffered a glitch that cut the flight short by forcing an immediate landing. We had either completely missed that in the news, or NASA wasn’t forthcoming with the news, perhaps until they knew more. But the details of the error are interesting and appear related to a glitch that happened 46 flights before, way back in May of 2021, that involves dropped frames from the video coming from the helicopter’s down-facing navigational camera. When this first cropped up back on flight six, it was only a couple of missed frames that nearly crashed the craft, thanks to confusion between the video stream and the inertial data. Flight engineers updated the aircraft’s software to allow for a little more flexibility with dropped frames, which worked perfectly up until the aborted flight 53.
DEF CON82 Articles
Supercon 2022: Michael Whiteley Saves The Badge
Michael Whiteley (aka [compukidmike]) is a badgelife celebrity. Together, he and his wife Katie make up MK Factor. They have created some of the most popular electronic conference badges. Of course, even experts make mistakes and run into challenges when they dare to push the envelope of technology and delivery schedules. In his Supercon 2022 talk, There’s No Rev 2: When Badgelife Goes Wrong, Mike shares details from some of his worst badge snafus and also how he managed to gracefully pull them back from the edge of disaster.
Living the Badgelife
Attendees at the world’s largest hacker convention, DEF CON in Las Vegas, had already become accustomed to receiving and wearing very cool and novel admission tokens, more properly known as badges. Then in 2006, at DEF CON 14, everything changed. Designed by Joe Grand, the first electronic DEF CON badge was a circuit board featuring a tiny PIC microcontroller, two LEDs, and a single pushbutton. Badgelife was born.
DEF CON 30 Humans Sampling Board
Mike begins his war stories with one about the DEF CON 30 badge. This was a herculean project with 25,000 badges being produced on a short timeline in the ever-changing chaos of a semiconductor supply-chain meltdown. Even though many regard it as one of the best DEF CON badges ever made, the DC30 badge posed a number of challenges to its creators. Microcontrollers were in short supply during 2021 and 2022 forcing the badge team to keep an eye on component vendor supplies in order to snipe chips as soon as they appeared in stock. The DC30 badge was actually redesigned repeatedly as different microcontrollers fluctuated in and out of supply. Continue reading “Supercon 2022: Michael Whiteley Saves The Badge”
Finally We Can Watch The Deere Cracking Def Con Talk
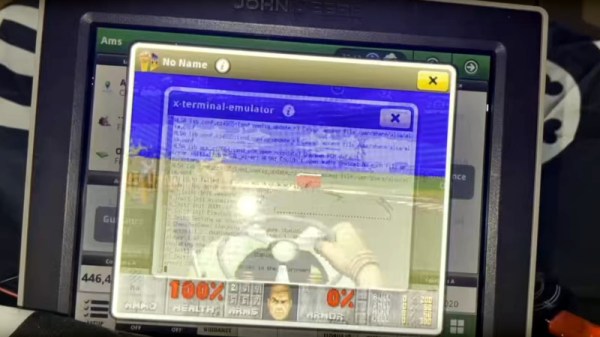
A few weeks ago, some tantalizing social media posts emerged from a Def Con talk, in which [Sick Codes] broke into the screen control unit for a John Deere tractor live on stage, and proceeded to play a special Deere-themed DOOM level upon it. At the time there was nothing more to go on, but we’re pleased to find out that the whole talk has been put online.
The talk starts with an introduction to the topic, to the basics of the control units within the machine and to the various different ages of Deere screen unit. We find that the earlier machines, which are still at work on farms worldwide, rely on outdated Windows CE versions, though the very latest screens run a Linux variant.
It’s one of these last screens to which he turns his attention, and we’re treated to an in-depth look at some of its secrets. After a lot of dead ends and learning exercises the final result is distilled into a pogo pin adapter for the hardware part, and a simple enough cron job to bypass one of Deere’s defenses by keeping the filesystem writable so a file can be updated. There’s a bit more detail about the special DOOM level too, as a special bonus.
You can see our original mention of this talk, or read some of our past Deere coverage.
Continue reading “Finally We Can Watch The Deere Cracking Def Con Talk”
Did You See A John Deere Tractor Cracked At DEF CON?
The Internet, or at least our corner of it, has been abuzz over the last few days with the news of a DEF CON talk by [Sick.Codes] in which he demonstrated the jailbreaking of the console computer from a John Deere tractor. Sadly we are left to wait the lengthy time until the talk is made public, and for now the most substantive information we have comes from a couple of Tweets. The first comes from [Sick.Codes] himself and shows a game of DOOM with a suitably agricultural theme, while the second is by [Kyle Wiens] and reveals the tractor underpinnings relying on outdated and un-patched operating systems.
You might ask why this is important and more than just another “Will it run DOOM” moment. The answer will probably be clear to long-term readers, and is that Deere have become the poster child for improper use of DRM to lock owners into their servicing and deny farmers the right to repair. Thus any breaches in their armor are of great interest, because they have the potential to free farmers world-wide from this unjust situation. As we’ve reported before the efforts to circumvent this have relied on cracked versions of the programming software, so this potential jailbreak of the tractor itself could represent a new avenue.
As far as we’re aware, this has so far taken place on the console modules in the lab and not in the field on a real tractor. So we’re unsure as to whether the door has been opened into the tractor’s brain, or merely into its interface. But the knowledge of which outdated software can be found on the devices will we hope lead further to what known vulnerabilities may be present, and in turn to greater insights into the machinery.
Were you in the audience at DEF CON for this talk? We’d be curious to know more. Meanwhile the Tweet is embedded below the break, for a little bit of agricultural DOOM action.
Continue reading “Did You See A John Deere Tractor Cracked At DEF CON?”
Hands On: DEF CON 29 Badge Embraces The New Normal
To say that 2020 was a transformative year would be something of an understatement. The COVID-19 pandemic completely changed the way we worked, learned, and lived. Despite all those jokes about how much time people spend on their devices rather than interacting face-to-face with other humans, it turns out that when you can’t get more than a few people together in the same room, it throws our entire society into disarray.
Our community had to rethink how we congregated, and major events like HOPE, DEF CON, and even our own Hackaday Supercon, had to be quickly converted into virtual events that tried with varying degrees of success to capture the experience of hundreds or thousands of hackers meeting up in real life. While few would argue that a virtual hacker convention can ever truly replace a physical one, we learned there are undeniable benefits to embracing the advantages offered by cyberspace. If nothing else, the virtual hacker meetups of 2020 saw a far larger and more diverse array of attendees and presenters than ever before.
 As we begin seeing the first rays of light at the end of the long, dark, tunnel we’ve been stuck in, it’s clear that some of the changes that COVID-19 forced on our community are here to stay. As eager as we all are to get back to the epic hackfests of old, nobody wants to close the door on all those who would be unable to attend physically now that they’ve gotten to peek behind the curtain.
As we begin seeing the first rays of light at the end of the long, dark, tunnel we’ve been stuck in, it’s clear that some of the changes that COVID-19 forced on our community are here to stay. As eager as we all are to get back to the epic hackfests of old, nobody wants to close the door on all those who would be unable to attend physically now that they’ve gotten to peek behind the curtain.
With this in mind, this year’s DEF CON is being presented in both physical and virtual forms simultaneously. If you made to Las Vegas, great. If not, you can follow along through chat rooms and video streams from the comfort of your own home. Following the theme, the DC29 badge is not only a practical tool for virtual attendees, but an electronic puzzle for those who are able to bring a few of them together physically. Let’s take a closer look at this socially distanced badge and the tech that went into it.
Continue reading “Hands On: DEF CON 29 Badge Embraces The New Normal”
AND!XOR’s DEF CON 29 Electronic Badge Is An Assembly Puzzle
For years I’ve looked forward to seeing each new unofficial hardware badge that comes out of the #Badgelife powerhouse known as AND!XOR. A mix of new and interesting components, alternate-reality game, and memes, you never know what they’re going to throw down.
A bubble pack landed on my desk on Thursday with the newest offering, the AND!XOR electronic badge built for DEF CON 29, happening this weekend as a hybrid in-person and online conference. While each previous year upped the ante on complexity and manufacturing magic tricks, it’s no surprise considering the uncertainty of both the global pandemic and global chip shortage that they took a different tack. What we have here is a badge hacking puzzle that challenges you to just figure out how to put the thing together!
Continue reading “AND!XOR’s DEF CON 29 Electronic Badge Is An Assembly Puzzle”
Breaking Smartphone NFC Firmware: The Gory Details
Near-field Communication (NFC) has been around a while and is used for example in access control, small data exchange, and of course in mobile payment systems. With such sensitive application areas, security is naturally a crucial element of the protocol, and therefore any lower-level access is usually heavily restricted and guarded.
This hardware is especially well-guarded in phones, and rooting your Android device won’t be of much help here. Well, that was of course only until [Christopher Wade] took a deep look into that subject, which he presented in his NFC firmware hacking talk at for this year’s DEF CON.
But before you cry out “duplicate!” in the comments now, [Jonathan Bennett] has indeed mentioned the talk in a recent This Week In Security article, but [Christopher] has since written up the content of his talk in a blog post that we thought deserves some additional attention.
To recap: [Christopher] took a rooted Samsung S6 and searched for vulnerabilities in the NFC chip’s safe firmware update process, in hopes to run a custom firmware image on it. Obviously, this wouldn’t be worth mentioning twice if he hadn’t succeeded, and he goes at serious length into describing how he got there. Picking a brain like his by reading up on the process he went through — from reverse engineering the firmware to actually exploiting a weakness that let him run his own code — is always fascinating and downright fun. And if you’re someone who prefers the code to do the talking, the exploits are on GitHub.
Naturally, [Christopher] disclosed his findings to Samsung, but the exploited vulnerability — and therefore the ability to reproduce this — has of course been out there for a long time already. Sure, you can use a Proxmark device to attack NFC, or the hardware we saw a few DEF CONs back, but a regular-looking phone will certainly raise a lot less suspicion at the checkout counter, and might open whole new possibilities for penetration testers. But then again, sometimes a regular app will be enough, as we’ve seen in this NFC vending machine hack.
Continue reading “Breaking Smartphone NFC Firmware: The Gory Details”