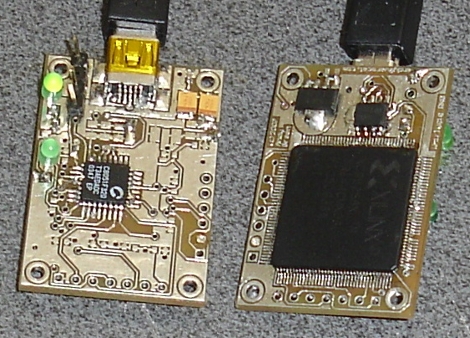
True randomness can be hard to come by in the digital world. [Andy Green] is making it easier to get true entropy by using this random USB dongle. The Whirlygig uses a CPDL to gather data from a set of of oscillators. The oscillators have a constantly fluctuating frequency due to temperature changes; if they run faster they generate more heat which in turn slows them down. This, along with the variable latency associated with polling a USB device, gives great depth of randomness. The device is detected and mounted under ‘/dev/hw_random’ and can then be fed into ‘/dev/random’ using the rng-tools package. [Andy’s] done a lot of testing, both on the hardware, and on the quality of randomness. We didn’t see an option to order this but he’s got hardware and firmware repositories so that you can throw one together yourself.
[Thanks Zunk]















now just for McGuvyer to poison the database with his trusty Zippo and then hack the Gibson with a paper clip
The problem with most hardware random number generators is failure detection. How do you know when the hardware craps out and starts generating a “less random” data stream?
Just a tip on Unix terminology – “mounting” is something you do with a file system. This is simply a device that appears at /dev/hw_random.
And the software package is called “rng-tools”. RNG = Random Number Generator.
Do you guys ever proof-read?
/nitpick
Intersting bit of hardware. Certainly more practical than the old lava-lamps-and-a-webcam hack from SGI.
Your nitpicking completely out of scope; everything is a file in linux, hardware included, and once it becomes a node in the file system, its mounted.
Try testing the output for randomness:
http://www.fourmilab.ch/random/
should of read on…
i don’t really have much of a need for random generation but this does look like it would be fairly affective
CPLD not CPDL
Nonetheless, cool idea.
@Keith
To detect when the hardware starts failing, you can create a hardware or software watchdog to regularly calculate the Entropy of a set of random samples. Given a sufficient big set, the Entropy should be near maximum.
So, when the Entropy goes below a certain threshold, it is guaranteed that your HW-RNG is failing.
An interesting device.
Would anyone like some ham?
you don’t mount devices.
@MrX:
Yes, exactly.
My (not terribly well-made) point: hardware RNGs are not “plug in and use forever” devices; they require constant monitoring to ensure the quality of their output.
Is there any device which is “plug in and use forever”? Of course a hardware RNG will eventually fail, just like anything else. It is no different from running occasional filesystem checks on a hard drive, you do spot checks on the system to make sure it is still working within certain tolerances.
That said, I am not sure how this relates to the project at hand. This device certainly doesn’t claim to be perfect, much less eternally perfect.
@MS3FGX Is there any device which is “plug in and use forever”?
Yes, my dick.
I think Keith still have a point. HW-RNGs are mostly used for security applications and on those cases the randomness of that is critical.
Making the device check the randomness of its output and discard sets of samples who are not, would be a important security improvement IMHO.
There is an object for the Parallax Propeller which does pretty much this same thing using the on-chip counter-timer PLL’s.
@localroger
I would like to try isolating a micro-controller tri-state pin from the environment and put it on low-impedance mode. I wonder how random the fluctuations on the readings will be.
You can inject data into /dev/random, and it measures the entropy in what you give it. So if your RNG starts failing, it just wont use the data anymore (and tell you).
You can buy entropy usb keys with fault, temp and randomness tests built in. I’ve seen one in use, makes ssh logins a lot faster :P http://www.entropykey.co.uk/
use a cmos camera and surplus lantern mantle?
:)
failing that, a traser lamp epoxied to a photodiode would also work as the output from these is random.
so erm.. other than servers and security, how can this benefit the average user?
would it be overkill for irc ssl?
I wonder how effective it would be to tap into junction noise of semiconductors, amplify them and feed that to a ADC.
For the average user it’s useless, but if your servers are handling a lot of ssl traffic it speeds things up a bit and provides a greater source of entropy.
“The problem with most hardware random number generators is failure detection. How do you know when the hardware craps out and starts generating a “less random” data stream?”
Take an FFT of the output to see what the spectrum is. If it’s flat then all is good otherwise it’s not.
You can make “random” data that is completely white (i.e. flat FFT) in the frequency domain despite not being the least bit random. e.g. LFSRs.
CPDL -> CPLD
http://www.kielnet.net/home/julien.thomas/tech/XR232WEB.htm
Simple and good one with rs232, unfortunately in german language.
http://translate.google.de/translate?js=y&prev=_t&hl=de&ie=UTF-8&layout=1&eotf=1&u=http%3A%2F%2Fwww.kielnet.net%2Fhome%2Fjulien.thomas%2Ftech%2FXR232WEB.htm&sl=de&tl=en&swap=1
HIJACK THE HARDWARE INPUT USED TO