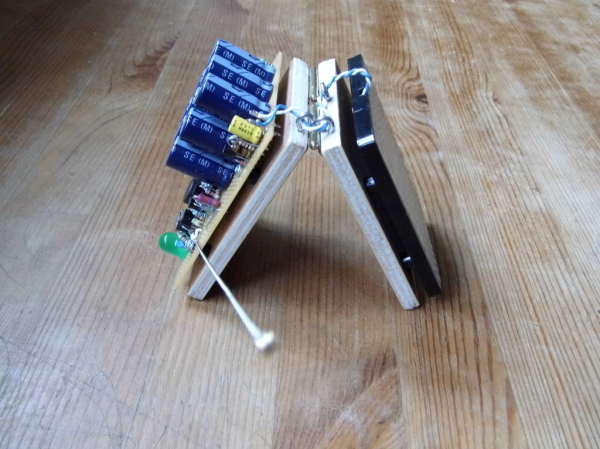
Whether it’s a game of D&D or encrypting top-secret information, a wide array of methods are available for generating the needed random numbers with high enough entropy for their use case. For a tabletop game this might be a single die but for more sensitive applications a more robust method of generating random numbers is needed. Programmers might reach for a rand() function of some sort, but these pseudorandom numbers don’t cut the mustard for encryption. For that you’ll need a true random number generator (RNG), and this open-source hardware RNG uses one of the better methods we’ve seen.
The device, called RAVA, is based on a property found in many electronic devices called avalanche breakdown. Avalanche breakdown occurs when a high voltage (in this case approximately 25V) is applied in the reverse bias direction, with this device using a pair of Zener diodes. When this high voltage is applied, an “avalanche” of electrons occurs which allows the diodes conduct in the opposite direction that they would when they are forward biased. This isn’t a constant current flow, though; there are slight variations over time which can be amplified and used as the random number generator. The noise is amplified over a series of op amps and then fed to an ATmega32U4 microcontroller which can provide the user with 136.0 Kbit/s of random data.
Unlike other random number generators, this device is based on a method generally accepted to be truly random. Not only that, but since it’s based on discrete hardware it can be accessed directly for monitoring and replacement in case of faults, unlike other methods which are more “black boxes” and are more opaque in their processes which are thus harder to audit. We also appreciate it’s open-source nature as well, and for some more information on it be sure to check out the paper on it in IEEE. If you’re looking for something to generate random numbers but will also bring some extra flair to the next game night, take a look at this radioactive dice replacement.



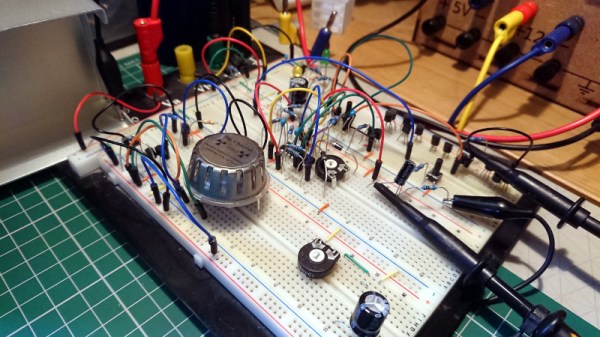
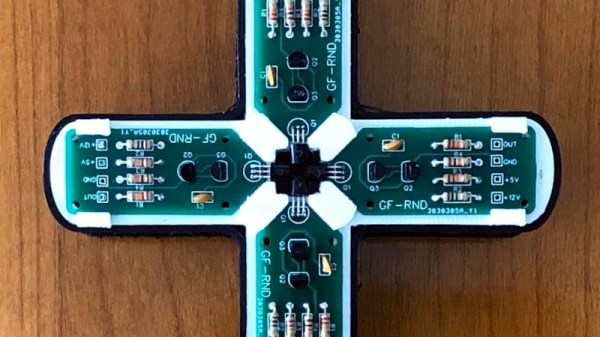
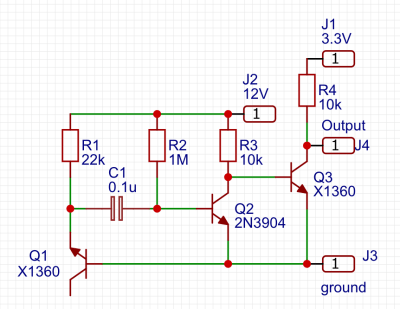 One of the simplest circuits for generating random analogue noise involves a reverse biased diode in either Zener or avalanche breakdown, and it is a variation on this that he’s using. A reverse biased emitter junction of a transistor produces noise which is amplified by another transistor and then converted to a digital on-off stream of ones and zeroes by a third. Instead of a shift register to create his four bits he’s using four identical circuits, with no clock their outputs randomly change state at will.
One of the simplest circuits for generating random analogue noise involves a reverse biased diode in either Zener or avalanche breakdown, and it is a variation on this that he’s using. A reverse biased emitter junction of a transistor produces noise which is amplified by another transistor and then converted to a digital on-off stream of ones and zeroes by a third. Instead of a shift register to create his four bits he’s using four identical circuits, with no clock their outputs randomly change state at will.