[Elliot] put together an intriguing proof-of-concept script that uses repeated deauthentication packet bursts to jam WiFi access points. From what we can tell it’s a new way to use an old tool. Aircrack-ng is a package often seen in WiFi hacking. It includes a deauthentication command which causes WiFi clients to stop using an access point and attempt to reauthenticate themselves. [Elliot’s] attack involves sending repeated deauthenitcation packets which in essence never allows a client to pass any data because they will always be tied up with authentication.
After the break you can see a video demonstration of how this works. The script detects access points in the area. The attacker selects which ones to jam and the script then calls the Aircrack-ng command. If you’ve got an idea on how to protect against this type of thing, we’d love to hear about. Leave your thoughts in the comments.
[youtube=http://www.youtube.com/watch?v=RmabhHiQ4yY&w=470]

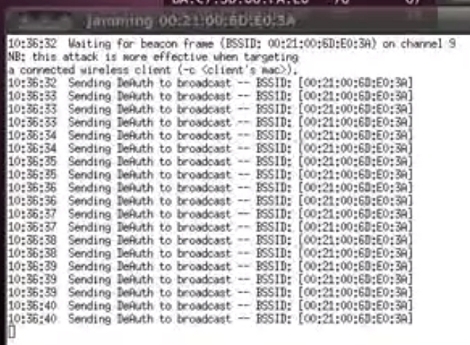













How long do 15 deauth packets jam for? I may or may not have booted myself.