This clever hack uses an Arduino to do a brute force attack on a computer’s BIOS. In theory, this technique could be used for other programs, but it’s use would be limited since there’s no way to account for too many wrong passwords.
The Arduino generates and outputs the possible password emulating a USB keyboard. When this is done, the pixel in the middle of the screen is read. This is done by reading the analog red signal synced up with the corresponding horizontal and vertical pulses. As with any hack, there were some programming issues that had to be overcome (including one that locked up the keyboard emulator), but this was resolved, and the code is available if you wan to build your own.
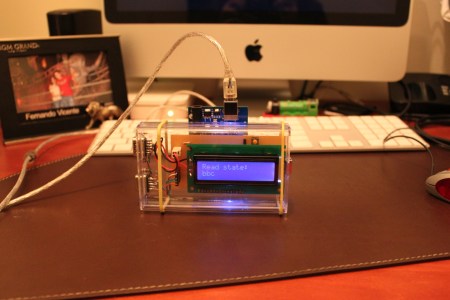
Hardware for this build is simple, involving a LCD output, a button to stop everything, and a couple diodes to get the USB keyboard working correctly. This hack turned out quite nicely, and the code and schematics are included!















keys per second?
Try default bios passwords first? You can even store list of default passwords in arduino if you need hardware solution so badly…
I’d agree with Harvie but how many bioses come locked down now-a-days? They are usually set by the sys admin. Still worth trying I suppose. Since the device analyzes the video signal, why not try to determine the bios make?
You can also dump the chip and deflate the image and find the pass. I’ve never seen one encrypted..
a bios password isn’t exactly a security thing. It’s just something to keep you 5 year old from fucking up your PC. There are manufactures’ passwords that should be in your computer’s/mobo’s manual just in case you forgot the one you made. If you lost it they can be easily found online.
Here is some I just googled
http://www.5starsupport.com/info/biospw.htm
Ummmm… Wow. What a waste of time. Dump the EEPROM or reset the password with the switch/jumper/whatever that most are equipped with.
um mm how about pull the internal battery? and leave it out and boot into bios?? just got done doing that for a customer desoudring a battery from the laptop mobo and was removed that way jeez something like this is clever but not needed.
Proof of concept is fine for a hack. I recognize the detractors in this thread, but the people stating the obvious bios reset options haven’t considered that there are possible situations where popping out the battery, the default bios password, or the sys password may not be available (maybe the PC is in a box, USB is available, but internal case access isn’t).
If you can’t access internals you can always do what I did in school – I got a big piezoeelectric gas lighter (one for stove, spark only, no flame), pulled cables from it and zapped about 15kV-20kV between case and power button. Bios memory got corrupted, automatically restored defaults and password was gone.
This spark generator was a very simple thing – tube of piezoelectric crystals compressed with a lever like those dynamo flashlights – but it was a beast. 2cm arcs from it generated enough EM to screw with keyboard status lights from 1 feet away.
I would be afraid of corrupting more then just the bios memory …
Yeah… And I made the point that you can easily reset the password in EEPROM… It’s documented for most manufacturers and OEM’s………………………………………………………………………
Everyone just needs to admit that this is a pretty dumb idea, and move on.
Dumb ideas have their place.
For those who suggest that this is not needed, that is true only if you do not have the requirement of retaining the original password. Nicely done.
There’s a lot of computers (most?) that this would take an extremely long amount of time on. My Dell will make you wait a full second after a wrong password. After four wrong tries, it restarts, then it does a full POST for about a minute before returning to the password screen. That means a maximum of 4 attempts per minute on some hardware.
Lots of laptops these days are not easy to reset. If it’s at all viable due to keys/s setting this up to run for a few days/weeks is probably easier than taking the machine apart and replacing an MSOP-8 or QFN EEPROM, or worse, cracking a TPM.
Clever approach. Might not be very useful, but nice work.
Great stuff!
There’s only one thing I’d really change: You got confused at the zener diode – resistor part. You want the resistors to be between the Arduino and the diodes, not between the diodes and the USB port…
interesting way to crack a BIOS. cool stuff and lots of things to learn from this project.
Thanks! I invite the commenters talking about a thousand ways to reset the password to read the original article, they can discover something revealing in the first paragraph: “There are no advantages in using this method, in fact this can be very slow and you may never find the password at all, but as always we do it for fun. It’s just a proof of concept, there are many ways of resetting a BIOS”
USB keyboards have a fundamental speed limitation, due to the way the HID protocol works. I wrote an explanation at the bottom of this page:
http://www.pjrc.com/teensy/td_keyboard.html
That 500 keystrokes/sec rate is with 12 MBit/sec USB, and only if the operating system (or bios’s USB implementation) actually honor’s the keyboard’s request for 1 HID transfer each USB frame. Each frame is 1 ms.
This project uses an Arduino running V-USB, which is only 1.5 Mbit/sec low-speed USB. The USB specification says low-speed devices are limited to at most 1 transfer every 10 frames. If the bios properly implements this, the maximum rate would be only 50 keystrokes/sec.
I wrote that section about the USB keyboard speed limits because in the early days of Teensy (about 2 years ago), several people asked about trying brute force password cracking. Most password prompts, even in a bios, have some mechanism to slow down repeated attempts. But even if they allow guessing at the maximum rate, the protocols keyboards use are inherently rate limited.
That little plastic enclosure looks really nice though. :-)
iPad (touch) case, I think.
To some people above: At least TRY to make it through the first paragraph before posting your redundant comments
I’ve read all comments, and still, I wanted to say it’s a very cool implementation and nice casing. Very inspiring!
Neat for a cute keyboard password try automater, but pretty much useless. Why brute force the Bios when you can simply wipe it. It’s just stored on a surface mount flash chip, just address the chip directly and either wipe the storage location or extract the information.
I’ve done this many times with laptops. Hell just shorting the chips power during boot up will make the bios assume that it’s corrupt and let you in to reset everything
Note: same thing can be used for getting int oa program or an OS. IT’s dumb to try passwords, put the drive in a linux box and end run the security. Only way to keep you from doing that is whole disk encryption. and in that case, if the password is somewhat long (you used a pass-phrase of at least 20 characters right? “My dog likes to eat cheese” is 900,000,000 times more secure than #$%f354ab) Then you are boned.
Although even if I used a 4 character password of only numbers this system will never get into my cellphone. after 3 failed tries it wipes the contents by simply destroying the encryption key for the flash memory.
As has already been posted, sometimes you forget the password for a machine used by multiple people who you don’t have access to, and you have to regain access without screwing them up. The applications are relatively few, but it’s not useless.
While I agree it’s overkill (there are easier ways to get around it), I think it’s uber cool. Certainly more useful in other circumstances than the bios.
Well, I thought the pixel sensing was pretty clever. I was surprised to see all the negativity.
Yah this is cool… but why don’t you just take out the CMOS Battery Yah it will get rid of the Password and reset the settings but… why? Maybe I just don’t get it.
wasnt being negitive but this thing is limited also id never try shorting connections its dangerous to pc boards while cool to see a bolt of electricity im better off removing the battery if its enclosed and under warrenty and can access the os flash it with new configs. If not take apart pull the battery out and unplug it wait 5 sec plug in power on and bam done. Reset the password.
i see so many ppl with destructive criticism what about the constructive ones? Replying bad about things is just too easy… Try to reply something good even if it takes more than a day and maybe next time you get something better. Would the driver be detected by a game? With the right keys this could be used to cheat something like bux.to…
I reread my own remarks to conclude I wasn’t being very constructive myself, but I was just too fed up with everybody giving the same “jeeh,-look-how-smart-i-am,-i-know-kompjoetors”-comments, even though the first paragraph of the article clearly reads: “There are no advantages in using this method”.
Just reading that single line makes half the commentators in this thread look like 10 year olds. I would expect more from an audience that is obviously (not to say self-proclaimingly) above average intelligence. Or should I refrase; I DEMAND MORE?
From the late 90’s till about 2002 certain Fujitsu B [business] series laptops stored the password in a little static rom just big enough for the access protocol,the password itself and “the individual machines unique identifier”. Although this could be got around,it was a huge time consuming pain in the posterior. Granted’ thats all obsolete tech now but given that such solutions come go and come again,such gadgets could well have there place in ones armory.
has anyone compiled this device?! I’ve gathered, I have not works!!! HELP!!!!
Is there a video for this?
I know this is a long dead thread.
But this is exactly what I need. I have a specialist motherboard from an arcade machine I want to use as a test platform for video cards. The whole system is locked down very tightly and I cannot get it to boot from any media except its factory hard disk.
When the bios is reset it still has a password.
Using this method, I should be able to gain access to boot settings and hopefully everything else will follow.
I need this, too. It is the only way to hack the password of my Scanner Kodak ScanStation 500.
Do somebody have such a machine?
Well for all of your crazy people out here not linking this tool.
What about now ? What about a E15 Lenovo Bios password. It CAN only be done with this tool.
There is no CMOS battery reset ,or whatever you were thinking. ONLY this tool will be able to hack it :) I love it when a plan comes together..