A while back we saw the MintEye CAPTCHA system – an ‘are you human’ test that asks you to move a slider until an image is de-swirled and de-blurred – cracked wide open by exploiting the accessibility option. Later, and in a clever bit of image processing, the MintEye CAPTCHA was broken yet again by coming up with an algorithm to detect if an image is de-swirled and de-blurred.
It appears we’re not done with the MintEye CAPTCHA yet (Russian, translation). Now the MintEye CAPTCHA can be broken without any image processing or text-to-speech libraries. With 31 lines of Java, you too can crack MintEye wide open.
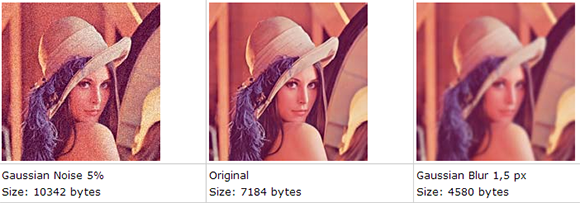
The idea behind the hack comes from the fact that blurred images will be much smaller than their non-blurred counterpart. This makes sense; the less detail in an image, the smaller the file size can be. Well, all the pictures MintEye delivers to your computer – 30 of them, one for each step of swirl and blurring – are the same size, meaning the ‘wrong answer’ images are padded with zeros at the end of the file.
There’s a 31 line program on the build page that shows how to look at thirty MintEye images and find the image with the fewest zeros at the end of the file. This is, by the way, the correct answer for the MintEye CAPTCHA, and has a reproducibility of 100%.
So, does anyone know if MintEye is a publicly traded company? Also, how exactly do you short a stock?















How long till they just start padding with random noise to the end of the image to prevent this?
the image data will contain some value that indicates the length of the image data rather than the filesize, otherwise we would see the padding in the image.
checking this rather than looking for and counting the padding should be simple enough
Also its too bad because I like these captchas far more than the squiggly garish multiclored reCaptcha
http://www.minteye.com/products.aspx
If I was MintEye, I’d be SO happy that I was getting all this FREE product testing and feedback! :) The good hackers are making it harder for the casual smartass to spam people’s sites. Keep it up!
You can rest assured that Minteye is taking this analysis and others very seriously. We and the white-hat community are trying to help each other, after all.
I kinda want MintEye on my blog now… I doubt any of the spambots or manual spammers I get on NorthStreetLabs can even figure out how to get passed this.
The (obvious) solution is to adjust the compression level on the generated images until the file sizes are random. This may also help a little with the other approaches for breaking minteye as the higher compression ratio may blur the images some…
The reason why the image size will be smaller is because in JPEG, when an image is blurred, a lot of the DCT high-frequency coefficients will be near-zero (and even more after quantization). All those zero coefficients will be highly compressed by the following coding stages (RLC and Huffman).
bmp format ftw
Then all the client needs to do is convert from BMP to JPG and compare sizes.
What about analyzing the image in the frequency space? That’s the first thing that came to my mind before reading the entry.
To a large extent thats what this ends up because of theway that JPEG compresses the image. This ends up a little indirect but works fairly well in practice. Id suspect even if they go bmp or random jpeg quality itll still work fairly well since you can recompress or do a direct fft check like you suggested. I dont see how they can prevent these attacks at the moment.
The only way I see to prevent FT like attacks would be to use low resolution images so there simply isnt much spatial information to work with. That sort of defeats the purpose of being easy for the user/aesthetic though.
instead of fiddling with the entropy, why not fiddle with the colours? We all know there are no pink elephants or blue bananas …
Colorblindness
blindness?
Different monitors, especially cheap ones, have wildly varying color accuracy. I am right now using two monitors of the same brand, model, and age. One makes everything look a little cool. The other makes everything pink. Neither can be adjusted far enough to make the effect not noticeable. I’m not convinced a CAPTCHA that relies on color could be set up to be reliably solvable by humans but not computers without being really, really annoying.
ok, maybe MintEye is meant to be not so annoying, but CAPTCHAs in general are annoyance to humans. The problem with colour accuracy is not really a problem. The colour shifts of the CAPTCHAs, or inversions of them are hardly something which can not be made distinguishable enough.
Compare this to the MinEye use case where your old CRT is out of focus. You’re probably able to tell where the picture is looking least off?
Colour based scrambling is least vulnerable to spectral analysis and image recognition based exploit angles.
Hey! Thats sounds great and promising.
Could you please suggest a way to break a different type of captcha?
Refer to http://stackoverflow.com/questions/15319528/removing-background-noisy-lines-from-captcha-image-using-python-pil